
Global Zero Trust Security Market Outlook to 2030
Region:Global
Author(s):Naman Rohilla
Product Code:KROD5500
December 2024
94
About the Report
Global Zero Trust Security Market Overview
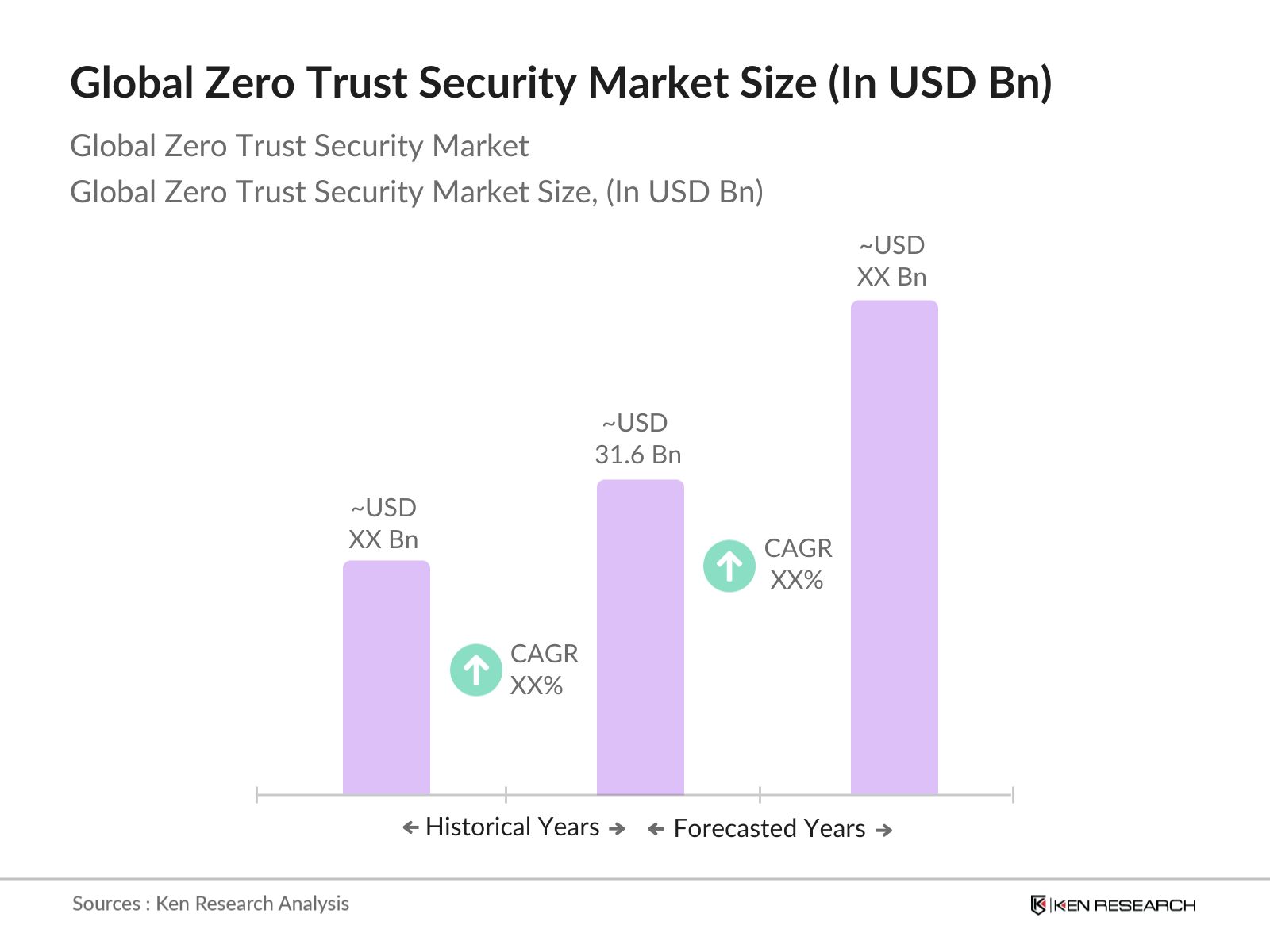
- The global Zero Trust Security market is valued at USD 31.6 billion, based on a five-year historical analysis. This market is driven by the growing need for comprehensive cybersecurity solutions due to the increase in cyberattacks, remote working, and cloud-based operations. The rise of ransomware and sophisticated breaches targeting companies and government institutions has necessitated the adoption of Zero Trust Security architectures to ensure that no entity is trusted by default, even within the organization's perimeter. The Zero Trust Security approach focuses on continuous verification of identities and secure access to sensitive data.
- The market is dominated by countries like the United States, China, and the United Kingdom due to their advanced technological infrastructure, large-scale enterprise adoption, and stringent regulatory frameworks. The U.S. leads the market primarily due to its well-established IT ecosystem and government mandates on cybersecurity measures, including zero-trust policies implemented for federal institutions. In contrast, China is rapidly advancing in Zero Trust Security owing to the expansion of its cloud computing and mobile-first companies, which are increasingly targeted by cyber threats.
- Data protection laws like the GDPR and CCPA have set global standards for securing personal data. Over $3 billion in fines have been levied under GDPR enforcement since its inception in 2018. These regulations require organizations to have strict access controls, continuous monitoring, and rapid breach detection, making Zero Trust Security a crucial tool for compliance and mitigating potential penalties.
M Global Zero Trust Security Market Segmentation
- By Solution Type: The Zero Trust Security market is segmented by solution type into Network Security, Identity & Access Management (IAM), Data Security, Security Analytics, and Endpoint Security. Recently, Identity & Access Management has dominated the market share in the segmentation by solution type, largely due to the rising need to authenticate and verify user credentials rigorously across various touchpoints. IAM solutions allow businesses to manage user identities, preventing unauthorized access to corporate systems and sensitive data, making it crucial for large enterprises and governmental institutions.
- By Deployment Mode: The market is segmented by deployment mode into On-Premises and Cloud. Cloud-based Zero Trust Security solutions have gained a dominant share within this segmentation due to the shift of businesses and government agencies towards cloud services. Cloud platforms offer flexibility, scalability, and ease of deployment, driving widespread adoption, particularly among small and medium enterprises that prefer avoiding the overhead of on-premise solutions.
- By Region: The Zero Trust Security market is divided regionally into North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa. North America currently dominates the market due to the high concentration of major technology firms and cybersecurity providers in the U.S. and Canada. The adoption of Zero Trust Security in this region is further propelled by regulatory pressures, such as compliance with the National Institute of Standards and Technology (NIST) and other cybersecurity frameworks, which mandate organizations to implement secure access and verification systems.
Global Zero Trust Security Market Competitive Landscape
The global Zero Trust Security market is dominated by several key players, each contributing to market growth through technological advancements and strategic partnerships. The Zero Trust Security market is concentrated, with leading companies leveraging their vast distribution networks and R&D capabilities to innovate and expand globally. These players are strategically positioned to capture market share, especially with the rising demand for cloud-based Zero Trust architectures.
|
Company |
Establishment Year |
Headquarters |
Market Share |
Key Solutions |
R&D Spending |
Cloud Offerings |
Key Partnerships |
Global Presence |
Revenue (2023) |
|
Palo Alto Networks |
2005 |
Santa Clara, USA |
- |
- |
- |
- |
- |
- |
- |
|
Cisco Systems |
1984 |
San Jose, USA |
- |
- |
- |
- |
- |
- |
- |
|
IBM Corporation |
1911 |
Armonk, USA |
- |
- |
- |
- |
- |
- |
- |
|
Microsoft Corporation |
1975 |
Redmond, USA |
- |
- |
- |
- |
- |
- |
- |
|
Zscaler, Inc. |
2007 |
San Jose, USA |
- |
- |
- |
- |
- |
- |
- |
Global Zero Trust Security Market Analysis
Global Zero Trust Security Market Growth Drivers
- Increasing Cybersecurity Threats: The global cybersecurity landscape has seen a rise in incidents, with over 1,000 major data breaches reported in the first half of 2023, impacting critical industries including healthcare, finance, and government sectors. According to the World Economic Forum, cybercrime could cost the global economy up to $10.5 trillion annually by 2025. The surge in sophisticated attacks such as ransomware, phishing, and nation-state cyber threats has created an urgent need for Zero Trust Security frameworks to secure sensitive data and operations across digital ecosystems.
- Cloud and IoT Adoption: By 2024, it is estimated that over 30 billion IoT devices will be connected worldwide, further increasing the surface area vulnerable to cyberattacks. Cloud computing adoption has surged as well, with 69% of enterprises globally utilizing multi-cloud environments to optimize their operations. This rapid adoption of cloud and IoT technologies has made traditional perimeter-based security models obsolete, boosting the demand for Zero Trust solutions, which ensure continuous authentication and monitoring.
- Regulatory Compliance Mandates: Governments worldwide are enforcing stringent regulatory compliance requirements to secure personal and financial data. Over 120 countries have introduced data protection legislation, with the EUs General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) setting high standards for data security and privacy. These laws demand enhanced access control and monitoring protocols, key features provided by Zero Trust Security architectures. Non-compliance can lead to penalties, further driving the need for secure solutions.
Global Zero Trust Security Market Challenges
- High Implementation Costs: Zero Trust Security requires a comprehensive overhaul of an organization's IT infrastructure, including software, hardware, and personnel training. The International Data Corporation (IDC) reports that 68% of large enterprises cite the high costs of adopting new security models as a primary barrier. The initial investment includes advanced authentication systems, continuous monitoring tools, and the integration of identity and access management (IAM) solutions, which can strain IT budgets, especially for small and medium-sized businesses.
- Complex Integration with Legacy Systems: A major challenge in Zero Trust adoption is integrating new security frameworks with legacy systems. By 2023, 47% of organizations reported difficulties in merging modern cybersecurity architectures with older, incompatible technologies. Legacy systems, particularly in critical sectors like healthcare and government, are often outdated and not designed to support continuous verification mechanisms, creating vulnerabilities during the transition phase.
Global Zero Trust Security Market Future Outlook
Over the next five years, the Zero Trust Security market is expected to exhibit robust growth driven by factors such as increasing cyberattacks targeting cloud infrastructure, the growing use of IoT devices, and an evolving regulatory landscape. Government agencies and enterprises across all regions are expected to adopt Zero Trust strategies to enhance their cybersecurity infrastructure. Moreover, advancements in artificial intelligence and machine learning are anticipated to further bolster the capabilities of Zero Trust solutions, making them more efficient and adaptive to evolving cyber threats.
Global Zero Trust Security Market Opportunities
- Expansion in Emerging Markets: Emerging economies in Asia, Latin America, and Africa present growth opportunities for Zero Trust Security adoption. As digital infrastructure expands in these regions, with more than 500 million new internet users in Asia alone by 2023, the demand for advanced cybersecurity solutions has risen sharply. Governments in these regions are also adopting stricter cybersecurity laws, creating an opportune environment for Zero Trust Security vendors to expand their footprint.
- Adoption of AI-Driven Security: Artificial intelligence (AI) is increasingly being integrated into Zero Trust Security frameworks to enhance threat detection and response times. By 2024, AI-driven security solutions are expected to reduce incident response times by up to 50%, according to a report from the OECD. This technological advancement offers tremendous growth potential as companies look to improve the efficiency and accuracy of their security operations through automation and predictive analytics.
Scope of the Report
|
By Solution Type |
Network Security IAM Data Security Security Analytics Endpoint Security |
|
By Deployment Mode |
On-Premises Cloud |
|
By Authentication Method |
MFA SSO Biometric Authentication |
|
By Vertical |
BFSI IT & Telecommunications Healthcare Government Retail & eCommerce |
|
By Region |
North America Europe Asia-Pacific Latin America Middle East & Africa |
Products
Key Target Audience
Government and Regulatory Bodies (NIST, European Union Agency for Cybersecurity)
Large Enterprises
Cloud Service Providers
Financial Institutions
Banks and Financial Institutions
Healthcare Organizations
Telecommunications Providers
Defence & Intelligence Agencies
Investor and Venture Capitalist Firms
Companies
Players Mentioned in the Report:
Palo Alto Networks
Cisco Systems
IBM Corporation
Microsoft Corporation
Zscaler, Inc.
Fortinet, Inc.
Akamai Technologies
Check Point Software Technologies
Cloudflare, Inc.
CrowdStrike Holdings
Table of Contents
1. Global Zero Trust Security Market Overview
1.1. Definition and Scope
1.2. Market Taxonomy
1.3. Market Growth Rate
1.4. Market Segmentation Overview
2. Global Zero Trust Security Market Size (In USD Bn)
2.1. Historical Market Size
2.2. Year-on-Year Growth Analysis
2.3. Key Market Developments and Milestones
3. Global Zero Trust Security Market Analysis
3.1. Growth Drivers
3.1.1. Increasing Cybersecurity Threats
3.1.2. Cloud and IoT Adoption
3.1.3. Regulatory Compliance Mandates
3.1.4. Growing Demand for Remote Work Security Solutions
3.2. Market Challenges
3.2.1. High Implementation Costs
3.2.2. Complex Integration with Legacy Systems
3.2.3. Lack of Skilled Cybersecurity Professionals
3.3. Opportunities
3.3.1. Expansion in Emerging Markets
3.3.2. Adoption of AI-Driven Security
3.3.3. Rise in Hybrid Workforces
3.4. Trends
3.4.1. Identity-Based Segmentation
3.4.2. Integration with DevSecOps
3.4.3. Micro-Segmentation Adoption
3.5. Government Regulations
3.5.1. Data Protection Laws (GDPR, CCPA)
3.5.2. Cybersecurity Maturity Model Certification (CMMC)
3.5.3. National Security Directives
3.6. SWOT Analysis
3.7. Stakeholder Ecosystem
3.8. Porters Five Forces
3.9. Competitive Landscape Overview
4. Global Zero Trust Security Market Segmentation
4.1. By Solution Type (In Value %)
4.1.1. Network Security
4.1.2. Identity & Access Management (IAM)
4.1.3. Data Security
4.1.4. Security Analytics
4.1.5. Endpoint Security
4.2. By Deployment Mode (In Value %)
4.2.1. On-Premises
4.2.2. Cloud
4.3. By Authentication Method (In Value %)
4.3.1. Multi-Factor Authentication (MFA)
4.3.2. Single Sign-On (SSO)
4.3.3. Biometric Authentication
4.4. By Vertical (In Value %)
4.4.1. BFSI
4.4.2. IT & Telecommunications
4.4.3. Healthcare
4.4.4. Government
4.4.5. Retail & eCommerce
4.5. By Region (In Value %)
4.5.1. North America
4.5.2. Europe
4.5.3. Asia-Pacific
4.5.4. Latin America
4.5.5. Middle East & Africa
5. Global Zero Trust Security Market Competitive Analysis
5.1. Detailed Profiles of Major Competitors
5.1.1. Palo Alto Networks
5.1.2. Cisco Systems, Inc.
5.1.3. IBM Corporation
5.1.4. Microsoft Corporation
5.1.5. Okta, Inc.
5.1.6. Zscaler, Inc.
5.1.7. Akamai Technologies
5.1.8. Fortinet, Inc.
5.1.9. Cloudflare, Inc.
5.1.10. CrowdStrike Holdings, Inc.
5.1.11. Check Point Software Technologies Ltd.
5.1.12. Broadcom Inc. (Symantec)
5.1.13. VMware, Inc.
5.1.14. Trend Micro Incorporated
5.1.15. Proofpoint, Inc.
5.2. Cross Comparison Parameters (Revenue, Product Offerings, Deployment Capabilities, Target Customer Base, Geographic Presence, Innovation Focus, Partnerships, Market Share)
5.3. Market Share Analysis
5.4. Strategic Initiatives
5.5. Mergers and Acquisitions
5.6. Investment Analysis
5.7. Venture Capital Funding
5.8. Government Grants
5.9. Private Equity Investments
6. Global Zero Trust Security Market Regulatory Framework
6.1. Compliance Standards
6.2. Industry Certifications
6.3. Data Privacy & Security Laws
7. Global Zero Trust Security Future Market Size (In USD Bn)
7.1. Future Market Size Projections
7.2. Key Factors Driving Future Market Growth
8. Global Zero Trust Security Future Market Segmentation
8.1. By Solution Type (In Value %)
8.2. By Deployment Mode (In Value %)
8.3. By Authentication Method (In Value %)
8.4. By Vertical (In Value %)
8.5. By Region (In Value %)
9. Global Zero Trust Security Market Analysts Recommendations
9.1. TAM/SAM/SOM Analysis
9.2. Target Market Prioritization
9.3. Marketing Initiatives
9.4. Strategic Opportunity Identification
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
The first step involved identifying the key stakeholders and market influencers in the Zero Trust Security ecosystem. We conducted a detailed desk analysis using secondary sources such as industry reports, cybersecurity journals, and regulatory publications.
Step 2: Market Analysis and Construction
We analyzed historical data to build market models, focusing on the adoption of Zero Trust Security solutions across industries and regions. Market penetration rates were calculated based on deployment modes (cloud vs. on-premises).
Step 3: Hypothesis Validation and Expert Consultation
We validated market assumptions through direct interviews with industry leaders and cybersecurity experts. This step ensured that our data accurately reflected current market conditions and growth projections.
Step 4: Research Synthesis and Final Output
The final step involved synthesizing the collected data and expert insights to deliver a comprehensive market report. The data was further validated through cross-verification with multiple industry stakeholders.
Frequently Asked Questions
01. How big is the Global Zero Trust Security Market?
The global Zero Trust Security market is valued at USD 31.6 billion, driven by the increasing need for secure network architectures amid rising cyber threats.
02. What are the challenges in the Zero Trust Security Market?
Challenges in the global Zero Trust Security market include high implementation costs, integration difficulties with legacy systems, and a lack of skilled cybersecurity professionals in some regions.
03. Who are the major players in the Zero Trust Security Market?
Key players in the global Zero Trust Security market include Palo Alto Networks, Cisco Systems, IBM Corporation, Microsoft Corporation, and Zscaler, Inc., all leading the market due to their innovative product offerings and large global presence.
04. What are the growth drivers of the Zero Trust Security Market?
The global Zero Trust Security market is driven by the growing threat of cyberattacks, cloud and IoT adoption, regulatory compliance requirements, and increasing demand for secure remote access.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















