Region:Global
Author(s):Dev
Product Code:KRAA1628
Pages:98
Published On:August 2025
By Type:The market is segmented into various types, including Data Security, Threat Protection, Risk & Compliance Management, Visibility & Access Control, Cloud Security Posture Management, and API, Proxy, and Agent-Based Modes. Each of these segments plays a crucial role in addressing specific security needs of organizations. CASBs commonly bundle visibility, DLP, encryption/tokenization, threat protection, and policy enforcement to address SaaS/IaaS/PaaS risks; integration with broader SSE/SASE stacks is increasingly common .

The Data Security segment, which includes DLP, encryption, and tokenization, is currently dominating the market due to the increasing need for organizations to protect sensitive information from data breaches and cyber threats. As businesses continue to adopt cloud services, the demand for robust data protection solutions has surged, driven by regulatory requirements and the need for compliance. This segment is expected to maintain its leadership position as organizations prioritize data security in their cloud strategies .
By End-User:The market is segmented by end-user industries, including BFSI, Healthcare & Life Sciences, Retail & E-commerce, Government & Public Sector, IT & Telecom, Education & Research, and Manufacturing & Industrial. Each sector has unique security requirements that drive the demand for cloud access security solutions. Industries with regulated data (finance, healthcare, public sector) emphasize DLP, encryption, auditability, and access governance in cloud apps, while retail/e-commerce and manufacturing focus on SaaS risk, identity, and third?party exposure .
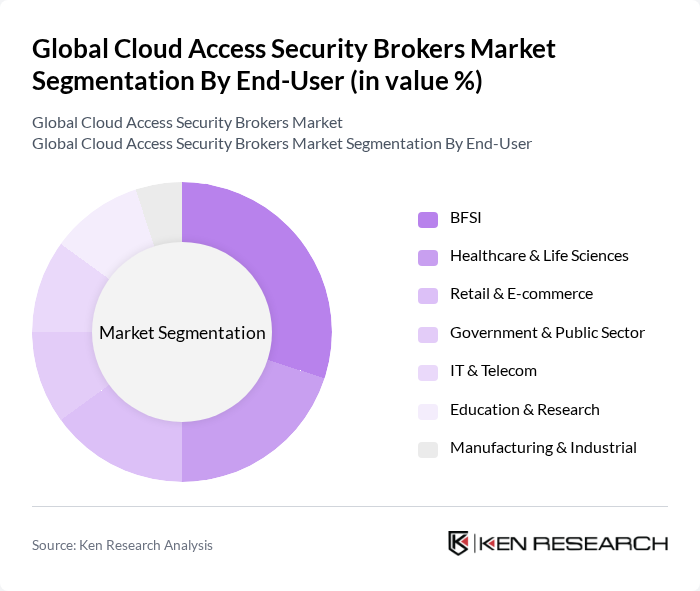
The BFSI sector is the leading end-user of cloud access security solutions, driven by stringent regulatory requirements and the need to protect sensitive financial data. Financial institutions are increasingly adopting cloud technologies, necessitating robust security measures to safeguard customer information and ensure compliance with regulations. This trend is expected to continue as the BFSI sector prioritizes security in its digital transformation efforts .
The Global Cloud Access Security Brokers Market is characterized by a dynamic mix of regional and international players. Leading participants such as Netskope, Inc., Zscaler, Inc., Palo Alto Networks, Inc. (Prisma Access/Prisma SaaS), Cisco Systems, Inc. (Cloudlock/Cisco Umbrella), Microsoft Corporation (Defender for Cloud Apps), Forcepoint LLC, Trend Micro Incorporated, Check Point Software Technologies Ltd. (CloudGuard), Proofpoint, Inc., Skyhigh Security (formerly McAfee Enterprise CASB), Broadcom Inc. (Symantec CloudSOC), Lookout, Inc., Bitglass (acquired by Forcepoint), CipherCloud (rebranded as Securiti for CASB assets; legacy references), CloudLock, Inc. (acquired by Cisco) contribute to innovation, geographic expansion, and service delivery in this space. CASB capabilities are increasingly delivered as part of broader SSE/SASE offerings combining secure web gateway, zero trust network access, and DLP to secure cloud access for distributed workforces .
The future of the Cloud Access Security Brokers market appears promising, driven by the increasing emphasis on cybersecurity and regulatory compliance. As organizations continue to embrace digital transformation, the demand for advanced security solutions will grow. Innovations in AI and machine learning will enhance CASB capabilities, enabling proactive threat detection and response. Additionally, the rise of remote work will necessitate robust security measures, further propelling the adoption of CASBs as essential tools for safeguarding cloud environments and sensitive data.
| Segment | Sub-Segments |
|---|---|
| By Type | Data Security (DLP, encryption, tokenization) Threat Protection (malware/URL filtering, anomaly detection) Risk & Compliance Management (policy enforcement, audit, data residency) Visibility & Access Control (shadow IT discovery, access policies) Cloud Security Posture Management (CSPM) & SSPM API, Proxy, and Agent-Based Modes |
| By End-User | BFSI Healthcare & Life Sciences Retail & E-commerce Government & Public Sector IT & Telecom Education & Research Manufacturing & Industrial |
| By Deployment Model | Cloud-Delivered (SaaS) On-Premises Hybrid |
| By Service Model | Software as a Service (SaaS) Platform as a Service (PaaS) Infrastructure as a Service (IaaS) |
| By Region | North America Europe Asia-Pacific Latin America Middle East & Africa |
| By Pricing Model | Subscription-Based (per user/device) Pay-As-You-Go (consumption-based) Tiered Pricing (Good/Better/Best) Enterprise Licensing (EAs, multi-year) |
| By Customer Size | Small Enterprises Medium Enterprises Large Enterprises |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Enterprise Cloud Security Implementation | 150 | IT Security Managers, Cloud Architects |
| SMB Cloud Access Security Adoption | 100 | IT Directors, Compliance Officers |
| Industry-Specific CASB Solutions | 80 | Sector-Specific IT Leads, Risk Management Executives |
| Cloud Security Policy Development | 70 | Security Policy Leads, Security Analysts |
| Data Protection and Compliance Strategies | 90 | Data Protection Officers, Legal Advisors |
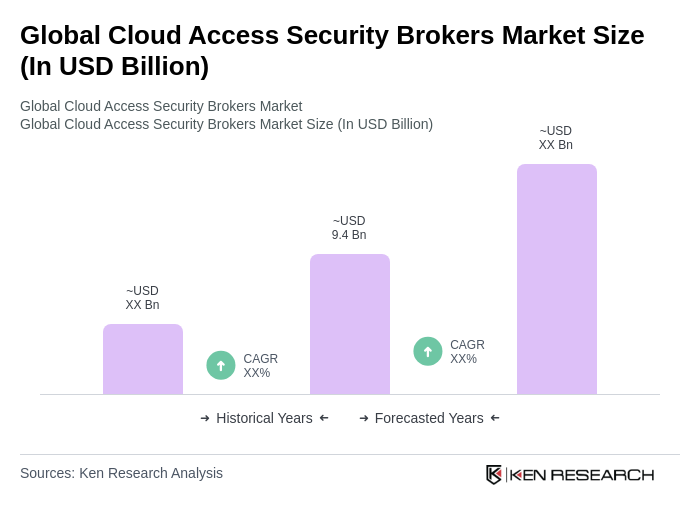
The Global Cloud Access Security Brokers Market is valued at approximately USD 9.4 billion, with estimates ranging from USD 9.4 to USD 10.7 billion. This reflects strong demand driven by cloud adoption and increasing security needs across enterprises.