Region:Global
Author(s):Dev
Product Code:KRAD3226
Pages:91
Published On:November 2025
By Type:The encryption software market can be segmented into various types, including File Encryption, Disk Encryption, Cloud Encryption, Database Encryption, Email Encryption, Network Encryption, Communication Encryption, and Others. Each of these sub-segments serves specific needs and industries, contributing to the overall growth of the market.
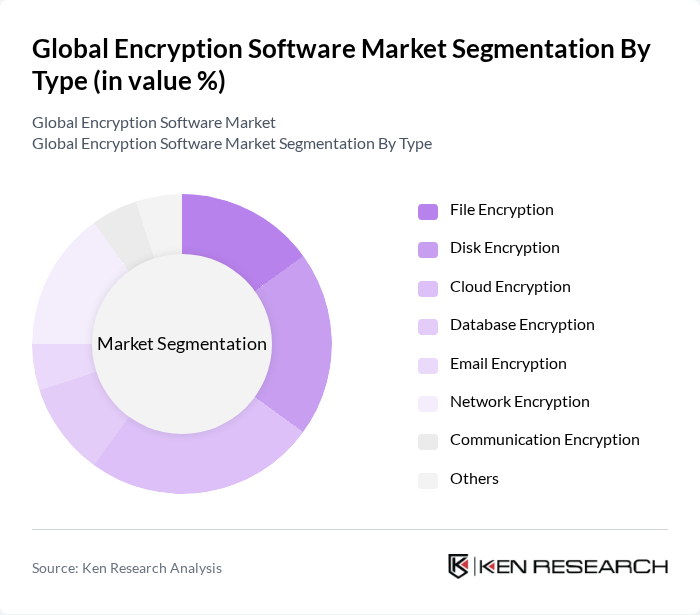
The Cloud Encryption sub-segment is currently dominating the market due to the rapid adoption of cloud services across various industries. Organizations are increasingly migrating their data to cloud platforms, necessitating robust encryption solutions to protect sensitive information from unauthorized access. The growing trend of remote work and the need for secure data sharing further drive the demand for cloud encryption solutions. As businesses prioritize data security, cloud encryption is expected to maintain its leading position in the market.
By End-User:The encryption software market is also segmented by end-user industries, including BFSI (Banking, Financial Services & Insurance), Healthcare & Life Sciences, Government & Defense, IT & Telecom, Retail & E-Commerce, Manufacturing, Education, and Others. Each sector has unique requirements for data protection, influencing the adoption of encryption technologies.
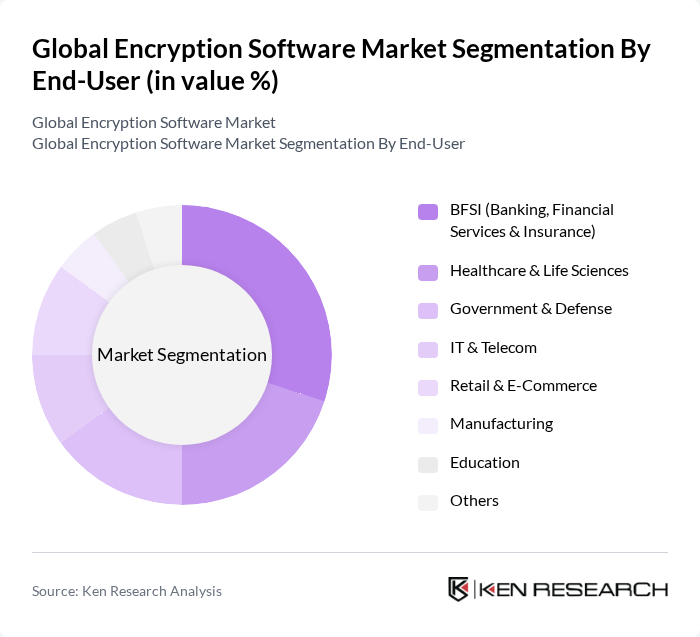
The BFSI sector is the leading end-user of encryption software, driven by stringent regulatory requirements and the need to protect sensitive financial data. Financial institutions are increasingly investing in encryption technologies to safeguard customer information and comply with regulations such as GDPR and PCI DSS. The high volume of transactions and the critical nature of data in this sector necessitate robust encryption solutions, solidifying its dominance in the market.
The Global Encryption Software Market is characterized by a dynamic mix of regional and international players. Leading participants such as Symantec Corporation, McAfee LLC, IBM Corporation, Thales Group, Microsoft Corporation, RSA Security LLC, Trend Micro Incorporated, Check Point Software Technologies Ltd., Sophos Group plc, Digital Guardian, ESET, spol. s r.o., Kaspersky Lab, Acronis International GmbH, Varonis Systems, Inc., CipherCloud, Entrust Corporation, Cisco Systems, Inc., Hewlett Packard Enterprise (HPE), East-Tec, InterCrypto Ltd. contribute to innovation, geographic expansion, and service delivery in this space.
The future of the encryption software market is poised for significant transformation, driven by technological advancements and evolving consumer expectations. As organizations increasingly adopt cloud-based solutions, the demand for scalable encryption technologies will rise. Additionally, the integration of artificial intelligence in encryption processes is expected to enhance security measures, making them more efficient. Companies that prioritize end-to-end encryption will likely gain a competitive edge, as data privacy becomes a central focus for consumers and regulators alike.
| Segment | Sub-Segments |
|---|---|
| By Type | File Encryption Disk Encryption Cloud Encryption Database Encryption Email Encryption Network Encryption Communication Encryption Others |
| By End-User | BFSI (Banking, Financial Services & Insurance) Healthcare & Life Sciences Government & Defense IT & Telecom Retail & E-Commerce Manufacturing Education Others |
| By Deployment Model | On-Premises Cloud-Based Hybrid Others |
| By Region | North America Europe Asia-Pacific Latin America Middle East & Africa |
| By Industry Vertical | Manufacturing Energy & Utilities Transportation & Logistics Media & Entertainment Others |
| By Encryption Method | Symmetric Encryption Asymmetric Encryption Hash Functions Quantum Encryption Blockchain-Based Encryption Others |
| By Application | Data Protection Secure Communication Identity Protection Compliance Management Others |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Encryption Solutions | 100 | Chief Information Security Officers, IT Managers |
| Healthcare Data Protection Software | 60 | Compliance Officers, IT Security Analysts |
| Government and Defense Encryption Tools | 40 | Cybersecurity Specialists, Policy Makers |
| Enterprise Software Encryption | 80 | IT Directors, Software Architects |
| Consumer Encryption Applications | 50 | End-users, Tech-savvy Consumers |
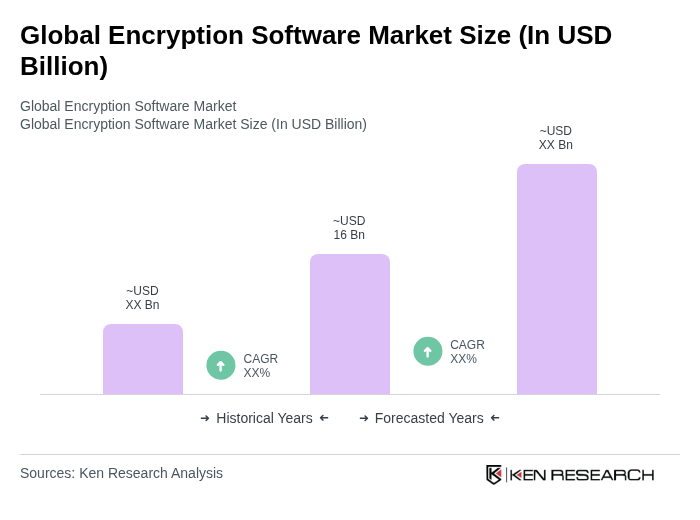
The Global Encryption Software Market is valued at approximately USD 16 billion, driven by the increasing need for data security, regulatory compliance, and the rising number of cyber threats faced by organizations across various sectors.