Region:Global
Author(s):Dev
Product Code:KRAD5149
Pages:94
Published On:December 2025
By Component:The components of the market include solutions and services. Solutions encompass insider threat platforms, user and entity behavior analytics (UEBA), data loss prevention (DLP), and security information and event management (SIEM) add-ons. Services are divided into professional and managed services. The solutions segment is currently leading the market due to the increasing demand for advanced technologies that can effectively detect and mitigate insider threats.

By Deployment Mode:The deployment modes in the market include on-premises, cloud, and hybrid solutions. The cloud deployment mode is gaining traction due to its scalability, cost-effectiveness, and ease of integration with existing systems. Organizations are increasingly adopting cloud-based solutions to enhance their security posture while reducing operational costs, making it the leading deployment mode in the market.

The Global Insider Threat Protection Market is characterized by a dynamic mix of regional and international players. Leading participants such as Microsoft Corporation (Insider Risk Management, Purview, Defender), IBM Security (QRadar, Guardium, Security Verify), Broadcom Inc. (Symantec Enterprise Division), Forcepoint LLC, Digital Guardian (by Fortra), Proofpoint Inc., Cisco Systems, Inc., CyberArk Software Ltd., Varonis Systems, Inc., Trellix (McAfee Enterprise & FireEye), Teramind Inc., DTEX Systems Inc., Securonix Inc., ObserveIT (Proofpoint Insider Threat Management), Code42 Software, Inc. (Incydr) contribute to innovation, geographic expansion, and service delivery in this space.
The future of insider threat protection is poised for significant evolution, driven by technological advancements and changing workplace dynamics. As organizations increasingly adopt remote work models, the demand for sophisticated security solutions will rise. Furthermore, the integration of artificial intelligence and machine learning will enhance threat detection capabilities, enabling proactive responses to potential insider threats. Companies will prioritize employee training and awareness programs to foster a security-conscious culture, ensuring a comprehensive approach to mitigating risks.
| Segment | Sub-Segments |
|---|---|
| By Component | Solutions (Insider Threat Platforms, UEBA, DLP, SIEM Add?ons) Services (Professional & Managed Services) |
| By Deployment Mode | On-Premises Cloud Hybrid |
| By Organization Size | Small and Medium-sized Enterprises (SMEs) Large Enterprises |
| By Application / Use Case | Data Exfiltration & IP Theft Prevention Privileged User & Administrator Monitoring Fraud & Business Process Abuse Detection Compliance & Audit Monitoring Third?Party & Contractor Risk Management |
| By Industry Vertical | BFSI (Banking, Financial Services & Insurance) IT & Telecommunications Government & Defense Healthcare & Life Sciences Retail & E?commerce Manufacturing Energy & Utilities Others |
| By Security Analytics Type | User and Entity Behavior Analytics (UEBA) Security Information and Event Management (SIEM)–based Analytics Endpoint & Network Telemetry Analytics Identity & Access Analytics |
| By Region | North America Europe Asia-Pacific Latin America Middle East and Africa |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Insider Threat Programs | 100 | Chief Information Security Officers, Risk Management Directors |
| Healthcare Data Protection Strategies | 80 | IT Security Managers, Compliance Officers |
| Technology Sector Security Measures | 90 | Cybersecurity Analysts, IT Directors |
| Manufacturing Industry Threat Mitigation | 70 | Operations Managers, Security Compliance Managers |
| Retail Sector Data Breach Responses | 60 | Data Protection Officers, IT Risk Assessors |
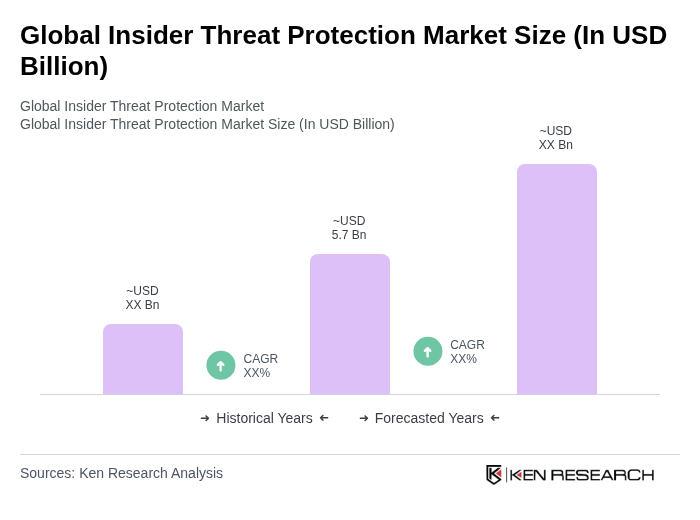
The Global Insider Threat Protection Market is valued at approximately USD 5.7 billion, driven by the increasing frequency of insider threats and the need for organizations to protect sensitive data from internal risks.