Region:Global
Author(s):Shubham
Product Code:KRAD0603
Pages:86
Published On:August 2025
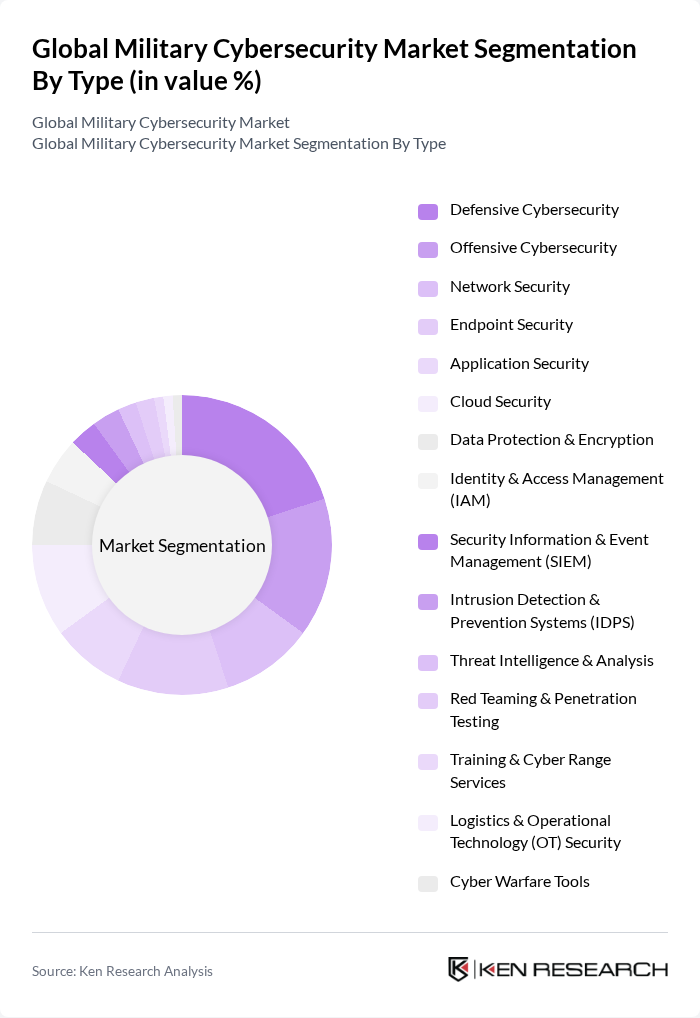
By Type:
By End-User:

The Global Military Cybersecurity Market is characterized by a dynamic mix of regional and international players. Leading participants such as Northrop Grumman Corporation, RTX Corporation (Raytheon), Lockheed Martin Corporation, BAE Systems plc, Thales Group, General Dynamics (GDIT), Leonardo S.p.A., Airbus Defence and Space, L3Harris Technologies, Inc., Booz Allen Hamilton, SAIC (Science Applications International Corporation), CACI International Inc, Palantir Technologies Inc., Microsoft (Azure Government, Microsoft Defense), Amazon Web Services (AWS GovCloud), Google Public Sector (Google Cloud), IBM Corporation, Cisco Systems, Inc., Palo Alto Networks, Inc., Fortinet, Inc., Check Point Software Technologies Ltd., CrowdStrike Holdings, Inc., Splunk Inc., Darktrace plc, Elastic N.V., Trellix (McAfee Enterprise and FireEye), Mandiant (a Google Cloud company), Rafael Advanced Defense Systems Ltd., Israel Aerospace Industries (IAI) – ELTA Systems, KBR, Inc. contribute to innovation, geographic expansion, and service delivery in this space.
The future of military cybersecurity in future is poised for significant transformation, driven by the increasing integration of advanced technologies and collaborative efforts between public and private sectors. As military organizations prioritize cyber resilience, the adoption of zero trust security models and AI-driven tools will become prevalent. Additionally, the emphasis on data privacy regulations will shape cybersecurity strategies, ensuring that military operations remain secure and compliant in an ever-evolving threat landscape.
| Segment | Sub-Segments |
|---|---|
| By Type | Defensive Cybersecurity Offensive Cybersecurity Network Security Endpoint Security Application Security Cloud Security Data Protection & Encryption Identity & Access Management (IAM) Security Information & Event Management (SIEM) Intrusion Detection & Prevention Systems (IDPS) Threat Intelligence & Analysis Red Teaming & Penetration Testing Training & Cyber Range Services Logistics & Operational Technology (OT) Security Cyber Warfare Tools |
| By End-User | Defense Ministries Armed Forces (Army, Navy, Air Force, Space, Cyber Commands) Defense Prime Contractors Intelligence Agencies Defense Research Organizations |
| By Component | Software Hardware Services (Managed, Professional, Training) |
| By Deployment Mode | On-Premises Cloud-Based Hybrid |
| By Application | Cyber Defense Operations (SOC, CSOC) Threat Intelligence & Hunting Incident Response & Recovery Secure Communications & C2 Platform & Weapon Systems Cybersecurity Critical Infrastructure & OT/ICS Security Secure Cloud and Data Centers |
| By Sales Channel | Direct to Government (Prime Contracts) System Integrators/Primes & Subcontractors Value-Added Resellers (VARs) and Distributors |
| By Policy Support | Government Grants & Programs Tax Incentives Public-Private Partnerships Defense Standards & Compliance (NIST, CMMC, NATO STANAGs) National Cyber Strategies & Doctrines |
| By Region | North America Europe Asia Pacific Middle East & Africa Latin America |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Military Cybersecurity Solutions | 120 | Cybersecurity Analysts, Defense IT Managers |
| Government Defense Agencies | 100 | Procurement Officers, Cybersecurity Program Managers |
| Defense Contractors | 80 | Project Managers, Technical Leads |
| Cybersecurity Training Programs | 60 | Training Coordinators, Military Educators |
| Incident Response Teams | 90 | Incident Response Managers, Security Operations Center Analysts |
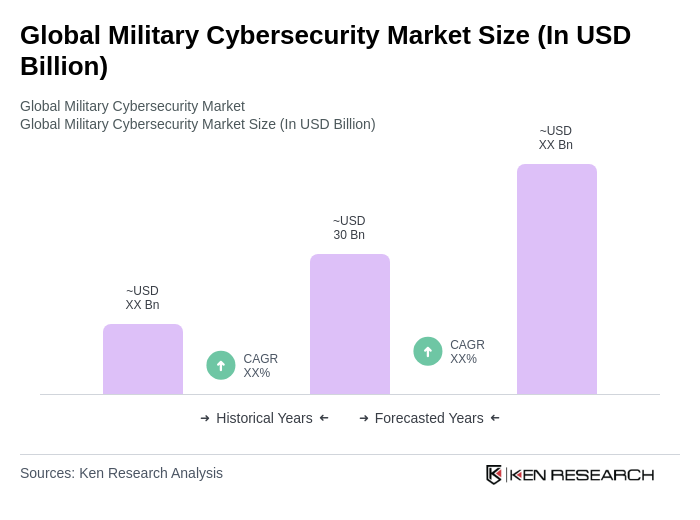
The Global Military Cybersecurity Market is valued at approximately USD 30 billion, reflecting a significant increase driven by the rising frequency of cyber threats targeting military infrastructure and the need for advanced security solutions to protect sensitive data and systems.