Region:Global
Author(s):Shubham
Product Code:KRAB0539
Pages:84
Published On:August 2025
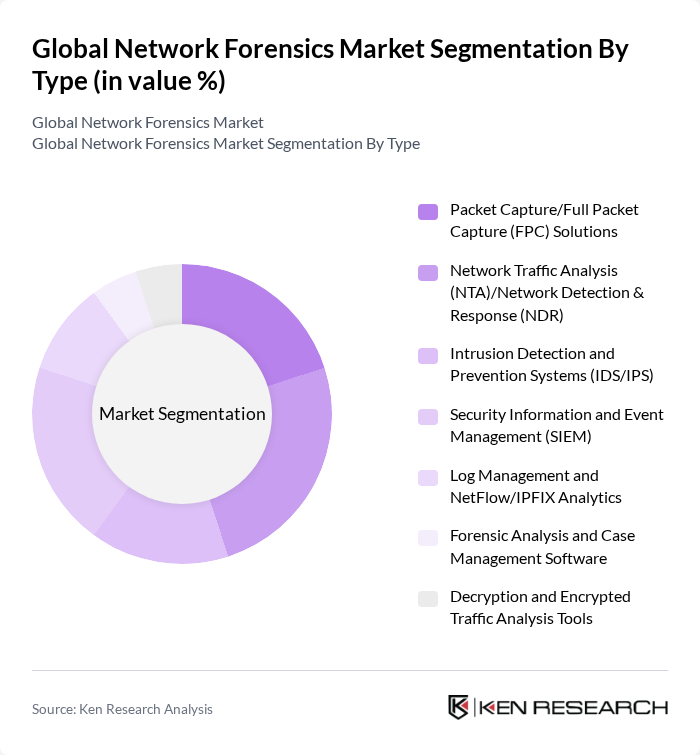
By Type:The market is segmented into various types of network forensics solutions, including Packet Capture/Full Packet Capture (FPC) Solutions, Network Traffic Analysis (NTA)/Network Detection & Response (NDR), Intrusion Detection and Prevention Systems (IDS/IPS), Security Information and Event Management (SIEM), Log Management and NetFlow/IPFIX Analytics, Forensic Analysis and Case Management Software, and Decryption and Encrypted Traffic Analysis Tools. Each of these subsegments plays a crucial role in enhancing network security and incident response capabilities.
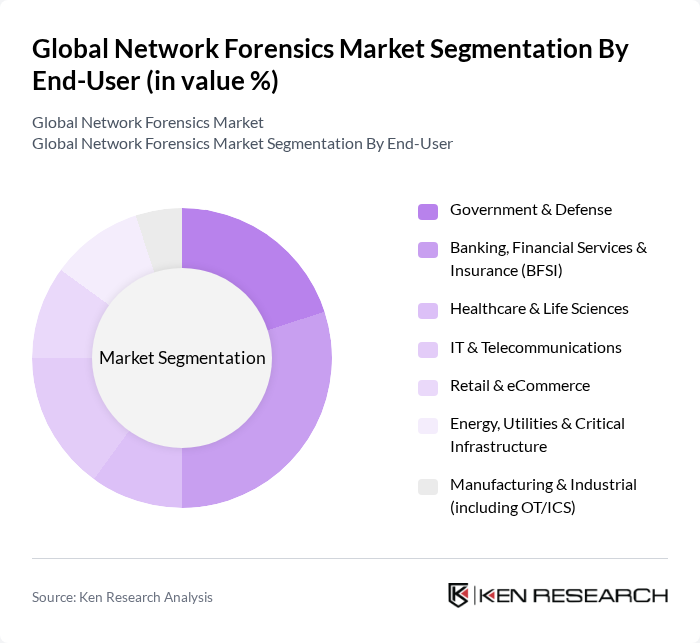
By End-User:The end-user segmentation includes Government & Defense, Banking, Financial Services & Insurance (BFSI), Healthcare & Life Sciences, IT & Telecommunications, Retail & eCommerce, Energy, Utilities & Critical Infrastructure, and Manufacturing & Industrial (including OT/ICS). Each sector has unique requirements for network forensics solutions, driven by regulatory compliance, data protection needs, and the necessity to safeguard sensitive information.
The Global Network Forensics Market is characterized by a dynamic mix of regional and international players. Leading participants such as Cisco Systems, Inc., Palo Alto Networks, Inc., Trellix (formerly FireEye and McAfee Enterprise), Splunk Inc., CrowdStrike Holdings, Inc., IBM Corporation, RSA Security LLC, LogRhythm, Inc., Fortinet, Inc., Check Point Software Technologies Ltd., NetWitness Corporation, Elastic N.V. (Elastic Security), Vectra AI, Inc., Sumo Logic, Inc., Darktrace plc contribute to innovation, geographic expansion, and service delivery in this space.
The future of the network forensics market is poised for significant transformation, driven by technological advancements and evolving cybersecurity needs. As organizations increasingly adopt automated forensics solutions, the focus will shift towards real-time data analysis capabilities. Furthermore, the integration of AI and machine learning will enhance threat detection and response times, enabling businesses to proactively address vulnerabilities. The growing emphasis on data privacy regulations will also drive demand for comprehensive forensics solutions, ensuring compliance and safeguarding sensitive information.
| Segment | Sub-Segments |
|---|---|
| By Type | Packet Capture/Full Packet Capture (FPC) Solutions Network Traffic Analysis (NTA)/Network Detection & Response (NDR) Intrusion Detection and Prevention Systems (IDS/IPS) Security Information and Event Management (SIEM) Log Management and NetFlow/IPFIX Analytics Forensic Analysis and Case Management Software Decryption and Encrypted Traffic Analysis Tools |
| By End-User | Government & Defense Banking, Financial Services & Insurance (BFSI) Healthcare & Life Sciences IT & Telecommunications Retail & eCommerce Energy, Utilities & Critical Infrastructure Manufacturing & Industrial (including OT/ICS) |
| By Deployment Mode | On-Premises Cloud (SaaS) Hybrid Managed/Hosted (MSSP) |
| By Application | Incident Response & Post-Incident Investigation Threat Hunting & Advanced Persistent Threat (APT) Detection Compliance Auditing & Reporting Data Breach & Fraud Investigation Encrypted Traffic Visibility & Anomaly Detection Lateral Movement & East-West Traffic Monitoring |
| By Region | North America Europe Asia-Pacific Latin America Middle East and Africa Rest of World |
| By Pricing Model | Subscription (Per Sensor/Appliance, Per TB Ingested, or Per User) Perpetual License Consumption-Based/Pay-As-You-Go (Cloud) Enterprise/EAL Agreements |
| By Service Type | Consulting & Assessment Implementation & Integration Support, Managed Detection & Response (MDR), and Maintenance Training & Digital Forensics/Incident Response (DFIR) Forensic Readiness & Tabletop Exercises |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Enterprise Network Security | 120 | IT Security Managers, Network Administrators |
| SME Cybersecurity Solutions | 100 | Small Business Owners, IT Consultants |
| Government Cybersecurity Initiatives | 80 | Policy Makers, Cybersecurity Analysts |
| Healthcare Data Protection | 70 | Healthcare IT Directors, Compliance Officers |
| Financial Sector Forensics | 90 | Risk Management Officers, Fraud Analysts |
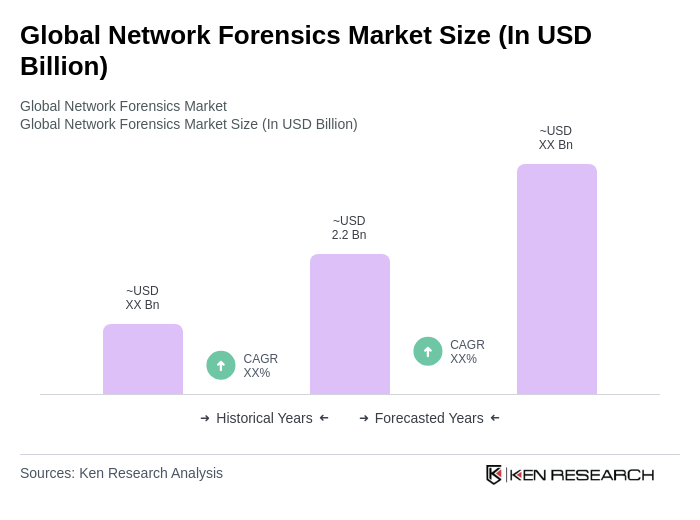
The Global Network Forensics Market is valued at approximately USD 2.2 billion, reflecting a significant investment by organizations to enhance their cybersecurity measures in response to increasing cyber threats and regulatory compliance requirements.