
Asia Pacific Identity and Access Management (IAM) Market Outlook to 2030
Region:Asia
Author(s):Shreya Garg
Product Code:KROD8752
December 2024
98
About the Report
Asia Pacific Identity and Access Management (IAM) Market Overview
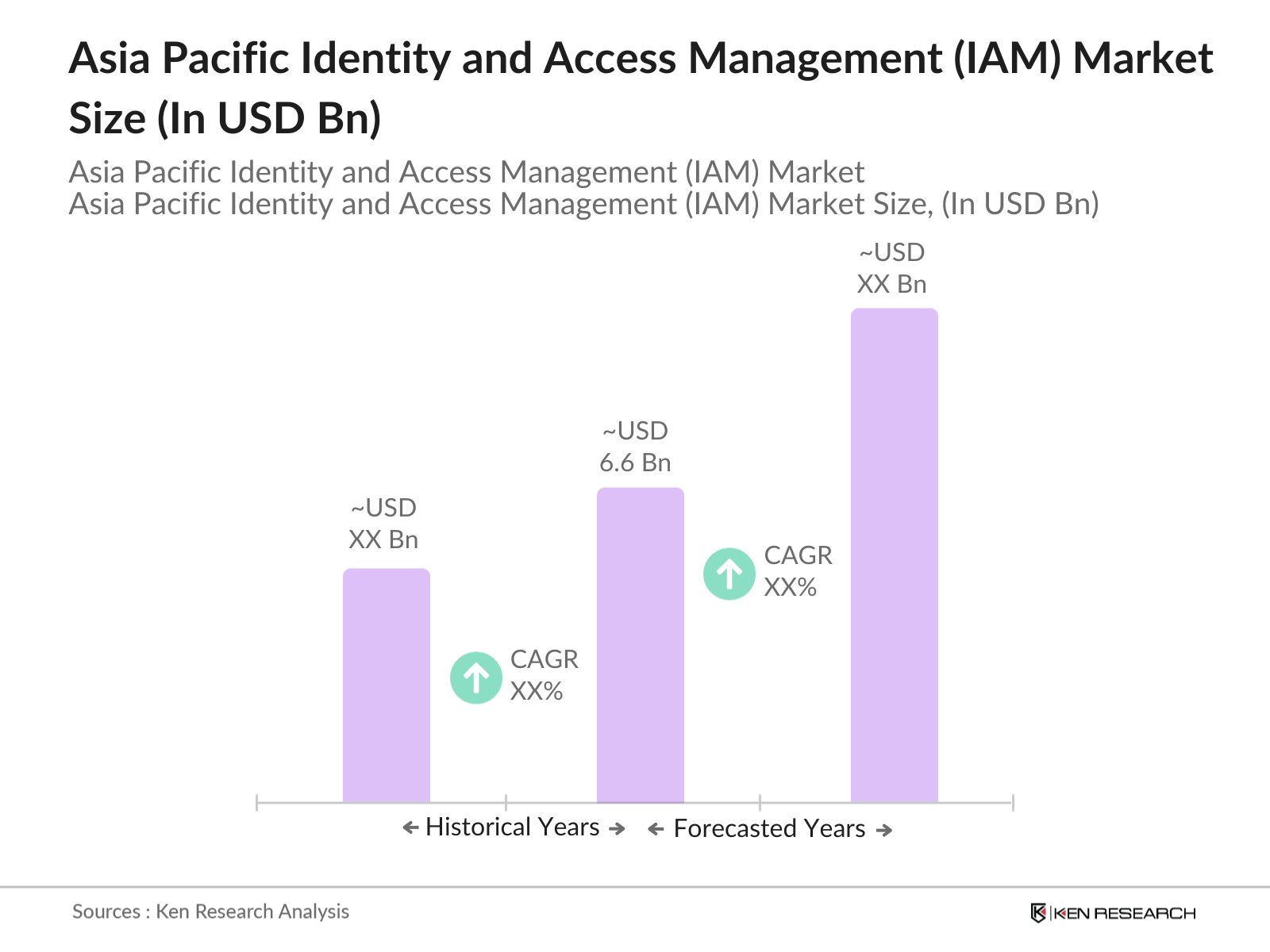
- The Asia Pacific Identity and Access Management (IAM) market, driven by heightened digital transformation and stringent regulatory compliance requirements, has reached a valuation of USD 6.6 billion. This growth is bolstered by an increase in remote working models, advancements in cybersecurity infrastructure, and government-backed initiatives supporting digital identity. Key sectors, such as finance, healthcare, and government services, are implementing IAM solutions to enhance security and improve data privacy.
- Leading countries in the IAM market include China, Japan, and India. Chinas dominance stems from its large-scale digital initiatives and stringent cybersecurity policies, while Japan leverages its advanced technological landscape and corporate investments in IAM solutions. Indias substantial growth is attributed to government-led programs promoting digital identity systems and rapid cloud adoption by enterprises across major cities like Bangalore, Mumbai, and New Delhi.
- Countries across APAC have implemented data protection laws inspired by the GDPR to safeguard personal information. Japans updated APPI law and Singapores PDPA require strict data handling protocols, pushing organizations to invest in IAM solutions. In 2023, 85% of corporations in APAC indicated compliance with these standards, reinforcing the demand for secure IAM solutions.
Asia Pacific Identity and Access Management (IAM) Market Segmentation
By Solution Type: The market is segmented by solution type into Identity Governance and Administration, Authentication, Privileged Access Management, and Access Management. Identity Governance and Administration leads in this segment due to regulatory requirements mandating secure access to sensitive data. This segment has gained traction among BFSI and healthcare industries, where secure identity management is critical for compliance and risk reduction. The adoption of AI-driven identity governance for efficient identity lifecycle management further reinforces this segments dominance. 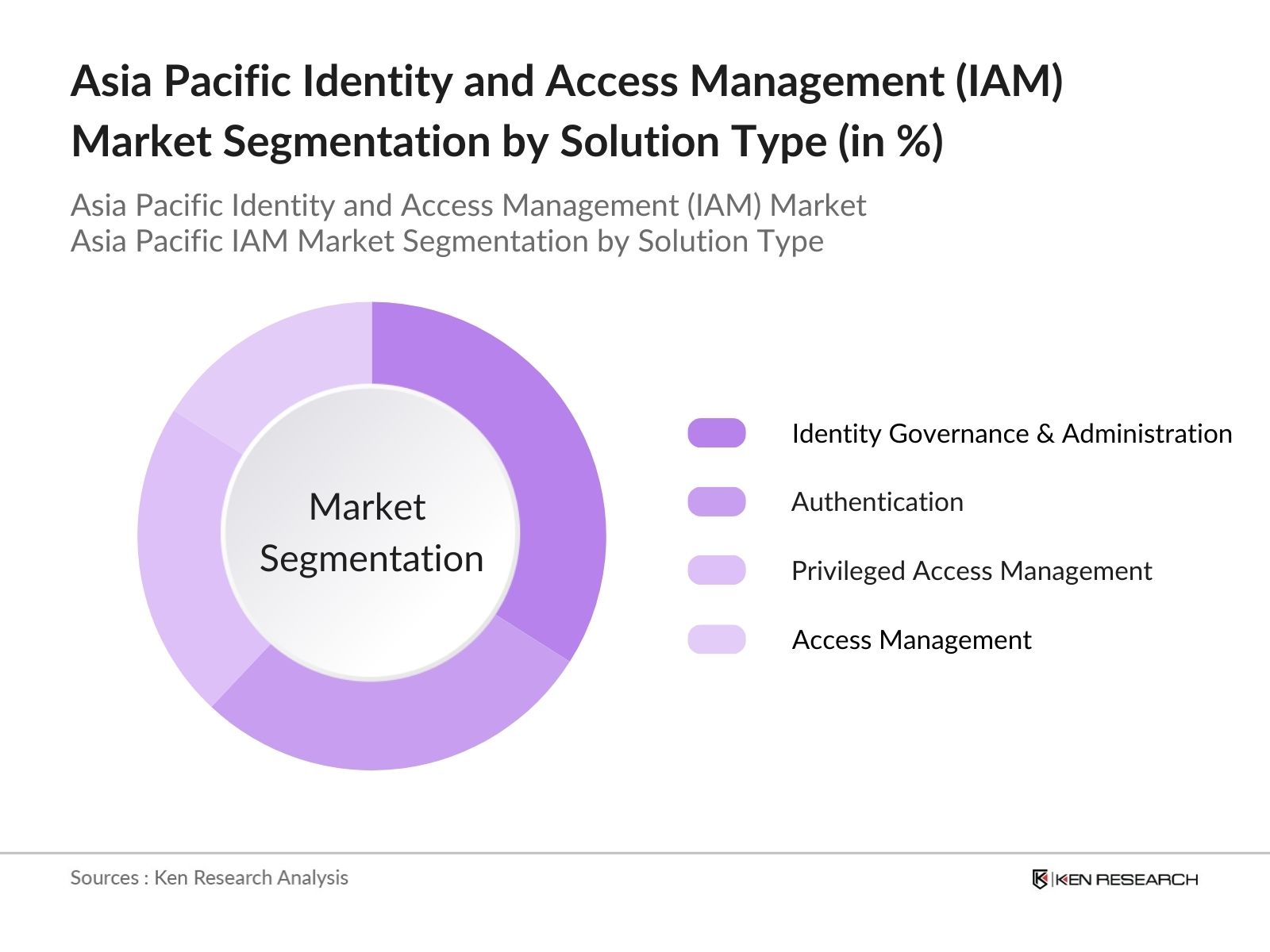
By Deployment Mode: The market is also segmented by deployment mode into On-Premises and Cloud-Based. Cloud-Based IAM solutions dominate due to the flexibility and scalability they offer for remote access, essential in the post-pandemic shift towards hybrid work environments. Additionally, cloud solutions facilitate quicker deployment and cost-efficiency, making them highly attractive to SMEs and large enterprises across the Asia Pacific region, especially within emerging markets like India and Southeast Asia. 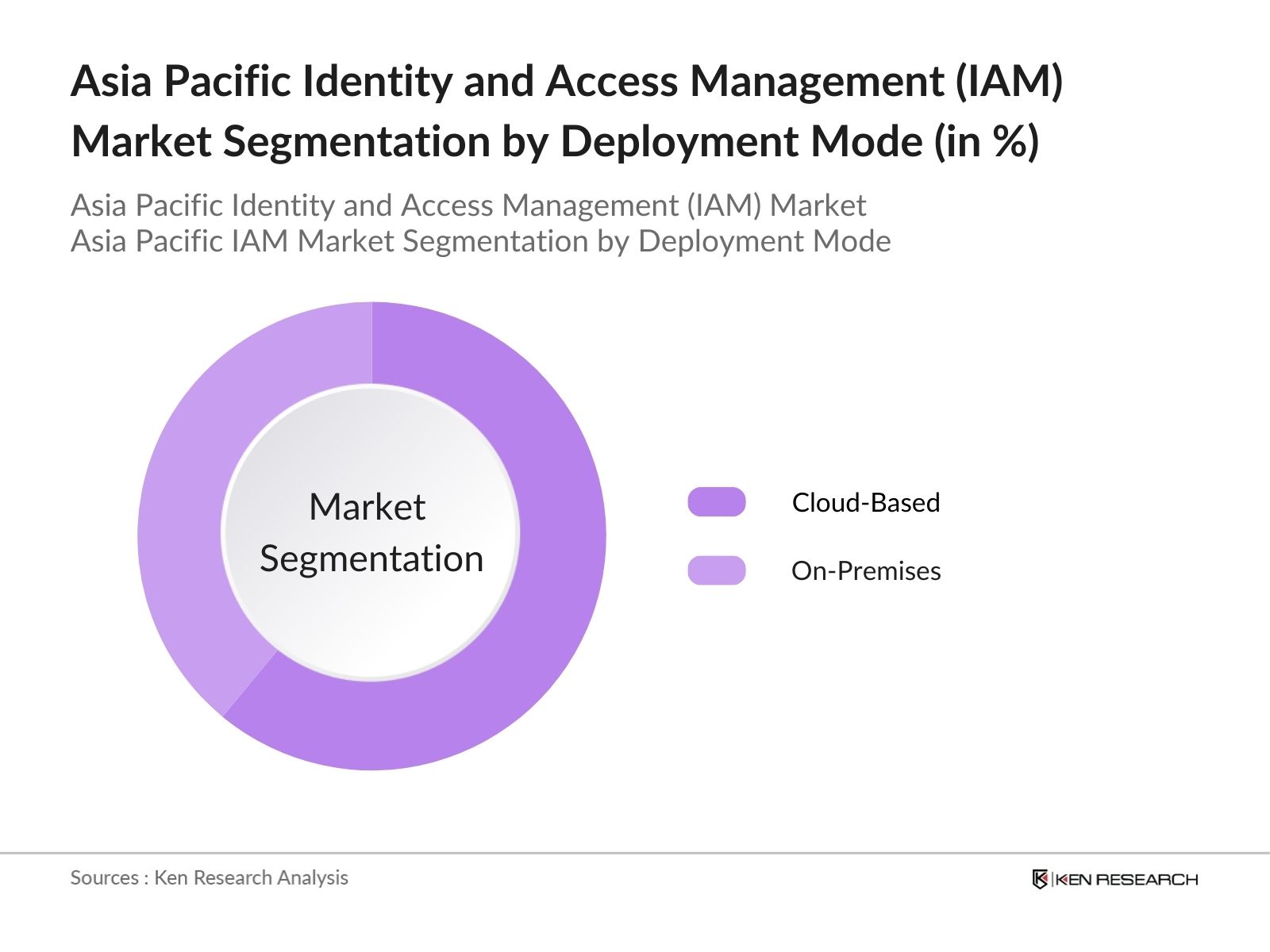
Asia Pacific Identity and Access Management (IAM) Market Competitive Landscape
The Asia Pacific IAM market is shaped by a mix of global and regional players that focus on technological advancement and extensive customer support. Major competitors are consolidating their presence through mergers, acquisitions, and partnerships to offer comprehensive IAM solutions.
|
Company |
Establishment Year |
Headquarters |
Revenue (USD Mn) |
Employees |
Geographical Reach |
Product Range |
Key Partnerships |
Customer Base Size |
Cloud Adoption Rate |
|
IBM Corporation |
1911 |
Armonk, USA |
|||||||
|
Microsoft Corporation |
1975 |
Redmond, USA |
|||||||
|
Oracle Corporation |
1977 |
Redwood City, USA |
|||||||
|
CyberArk Software |
1999 |
Petah Tikva, Israel |
|||||||
|
Ping Identity |
2002 |
Denver, USA |
Asia Pacific Identity and Access Management (IAM) Industry Analysis
Growth Drivers
- Increasing Digital Transformation in Enterprises: The rapid digital transformation across Asia-Pacific enterprises has intensified the need for effective Identity and Access Management (IAM) systems, driven by stringent data protection regulations like the Personal Data Protection Act (PDPA) in Singapore and Australias Privacy Act. For instance, Japans amended Act on the Protection of Personal Information mandates enterprises to adopt robust data handling and access control measures. As of 2023, 40% of APAC companies are transitioning their digital infrastructure, especially in Japan and Australia, to comply with these regulations, requiring advanced IAM solutions. Source: Japan Data Protection Laws.
- Rising Cybersecurity Concerns and Compliance Requirements: Asia-Pacifics cybersecurity threat landscape has escalated, with reported cyber incidents in sectors such as finance and healthcare increasing by 25% since 2022. IAM solutions are now essential in compliance frameworks like Singapores Cybersecurity Act, which impacts 1,500 Critical Information Infrastructure (CII) operators. Malaysia's cybersecurity budget reached USD 2.3 billion in 2023, emphasizing the urgent demand for IAM solutions in government and enterprise sectors to prevent data breaches and regulatory non-compliance.
- Adoption of Multi-Factor Authentication (MFA) Solutions: Driven by government directives and cyber threats, APAC businesses increasingly prioritize multi-factor authentication (MFA) within IAM protocols. Japan, South Korea, and Australia have seen a 30% increase in MFA adoption among financial institutions since 2022, aligning with the Financial Action Task Force (FATF) standards. South Koreas National Intelligence Service supports MFA deployment for sensitive industries, and as of 2024, 78% of large enterprises have implemented MFA as a compliance measure, particularly in banking and government sectors.
Market Challenges
- High Initial Costs and Deployment Complexities: The deployment of IAM systems involves substantial costs and expertise, making it challenging for small and mid-sized companies. For instance, in Malaysia, IAM deployment costs ranged between USD 500,000 and USD 2 million for mid-size enterprises as of 2023, impacting their adoption rates. High capital requirements for robust IAM solutions deter smaller firms from implementation, especially in regions where IT budgets remain constrained, as seen in Indonesia and Thailand.
- Integration Issues with Legacy Systems: Integrating IAM solutions with outdated or proprietary legacy systems is a significant hurdle. In Japan and South Korea, up to 42% of firms reported integration difficulties in 2023, particularly within industries relying on legacy infrastructure like manufacturing and utilities. The complexity arises from incompatibility issues that require additional middleware, increasing deployment timelines and costs. Government sectors face similar challenges, especially in maintaining compliance with regional regulations while updating their IAM frameworks. Source: Japans Ministry of Economy, Trade, and Industry.
Asia Pacific Identity and Access Management (IAM) Market Future Outlook
The Asia Pacific IAM market is set to evolve further as organizations continue prioritizing data security, user authentication, and compliance with privacy regulations. Heightened adoption of multi-factor authentication (MFA), AI-enhanced identity governance, and the integration of zero-trust security models are anticipated to drive demand. Enterprises are increasingly shifting to cloud IAM solutions, supporting this trend with dedicated investments in digital identity platforms, especially in countries with growing internet and smartphone penetration.
Future Market Opportunities
- Growing Demand for Identity-as-a-Service (IDaaS) Solutions: With a surge in cloud computing adoption, IDaaS solutions are witnessing robust demand. In 2023, 36% of APACs digital-first companies adopted IDaaS for flexible and scalable identity management, aligning with strict regional regulatory standards. IDaaS adoption is especially strong in India and Japan, where IDaaS solutions offer enhanced compliance and security. This demand is likely to increase, driven by regulatory mandates and the need for remote workforce security solutions.
- Potential in Small and Medium Enterprises: Small and Medium Enterprises (SMEs) are recognizing the importance of IAM as cyber threats increase. In 2023, the Australian government allocated AUD 1.3 billion to support cybersecurity initiatives, indirectly benefiting IAM adoption within SMEs. This growing awareness among SMEs, especially in urban areas of India and Malaysia, highlights an opportunity for simplified and cost-effective IAM solutions tailored to smaller-scale deployments.
Scope of the Report
|
Component |
Solution |
|
Deployment Type |
On-Premises |
|
Organization Size |
Large Enterprises |
|
Industry Vertical |
BFSI |
|
Country |
China |
Products
Key Target Audience
Identity and Access Management Solution Providers
IT and Cybersecurity Service Providers
Financial Institutions (e.g., Asia-Pacific Banking Sector)
Healthcare Providers (e.g., Hospitals, Health Insurance Providers)
Government and Regulatory Bodies (e.g., Ministry of Industry and Information Technology, Japan's METI)
Retail and E-commerce Sector
Investor and Venture Capitalist Firms
Telecommunication Operators (APAC-based)
Companies
Major Players
IBM Corporation
Microsoft Corporation
Oracle Corporation
CyberArk Software
Ping Identity
SailPoint Technologies
RSA Security LLC
Okta, Inc.
OneLogin, Inc.
Centrify Corporation
ForgeRock
SecureAuth Corporation
Dell Technologies
Avatier Corporation
Broadcom Inc.
Table of Contents
Asia Pacific IAM Market Overview
1.1. Definition and Scope
1.2. Market Taxonomy
1.3. Market Dynamics Overview
1.4. Market Segmentation Overview
Asia Pacific IAM Market Size (In USD Mn)
2.1. Historical Market Size
2.2. Year-On-Year Growth Analysis
2.3. Key Market Developments and Technological Advancements
Asia Pacific IAM Market Analysis
3.1. Growth Drivers
3.1.1. Increasing Digital Transformation in Enterprises (GDPR, APAC Regulatory Influence)
3.1.2. Rising Cybersecurity Concerns and Compliance Requirements
3.1.3. Adoption of Multi-Factor Authentication (MFA) Solutions
3.1.4. Expanding Role of Cloud-Based IAM Solutions
3.2. Market Challenges
3.2.1. High Initial Costs and Deployment Complexities
3.2.2. Integration Issues with Legacy Systems
3.2.3. Shortage of Skilled Workforce for Advanced IAM Solutions
3.3. Opportunities
3.3.1. Growing Demand for Identity-as-a-Service (IDaaS) Solutions
3.3.2. Potential in Small and Medium Enterprises (SMEs)
3.3.3. Expansion of IAM Solutions in Financial Services Sector
3.3.4. Advancements in Artificial Intelligence and Machine Learning in IAM
3.4. Trends
3.4.1. Integration of IAM with Blockchain Technology
3.4.2. Rise of Zero Trust Security Models
3.4.3. Increasing Use of Biometric Authentication
3.4.4. Mobile-Based IAM Solutions for APAC Markets
3.5. Regulatory Environment
3.5.1. Data Protection and Privacy Laws (APAC GDPR, PDPA, etc.)
3.5.2. Regional Compliance Standards (PCI-DSS, SOX, etc.)
3.5.3. Government Initiatives and Cybersecurity Frameworks
3.6. SWOT Analysis
3.7. IAM Stakeholder Ecosystem (Providers, End-Users, Regulators)
3.8. Porters Five Forces Analysis (IAM Market-Specific)
3.9. IAM Competitive Ecosystem Overview
Asia Pacific IAM Market Segmentation
4.1. By Component (In Value %)
4.1.1. Solution
4.1.2. Services
Managed Services
Professional Services
4.2. By Deployment Type (In Value %)
4.2.1. On-Premises
4.2.2. Cloud-Based
4.3. By Organization Size (In Value %)
4.3.1. Large Enterprises
4.3.2. Small and Medium Enterprises (SMEs)
4.4. By Industry Vertical (In Value %)
4.4.1. BFSI
4.4.2. IT and Telecommunications
4.4.3. Government and Public Sector
4.4.4. Healthcare
4.4.5. Retail and eCommerce
4.5. By Country (In Value %)
4.5.1. China
4.5.2. Japan
4.5.3. India
4.5.4. South Korea
4.5.5. Australia and New Zealand
Asia Pacific IAM Competitive Analysis
5.1. Detailed Profiles of Major Companies
5.1.1. IBM Corporation
5.1.2. Microsoft Corporation
5.1.3. Oracle Corporation
5.1.4. CA Technologies
5.1.5. RSA Security LLC
5.1.6. SailPoint Technologies
5.1.7. ForgeRock
5.1.8. Okta, Inc.
5.1.9. Ping Identity
5.1.10. Symantec Corporation
5.1.11. CyberArk Software Ltd.
5.1.12. OneLogin, Inc.
5.1.13. Centrify Corporation
5.1.14. SecureAuth Corporation
5.1.15. Dell Technologies
5.2. Cross Comparison Parameters (Revenue, Product Portfolio, Geographical Presence, Customer Base, R&D Expenditure, Strategic Partnerships, Technological Investments, Cloud vs. On-Premises Solutions)
5.3. Market Share Analysis
5.4. Strategic Initiatives (Mergers, Acquisitions, Alliances)
5.5. Venture Capital and Private Equity Funding Analysis
5.6. Government Grants and Public-Private Partnerships
5.7. Investment Analysis (Key Investors and Funding Trends)
Asia Pacific IAM Market Regulatory Framework
6.1. Data Privacy and Security Compliance (APAC-Specific)
6.2. Certification and Audit Processes (ISO 27001, SOC 2)
6.3. Impact of Cybersecurity Acts and Government Guidelines
Future Asia Pacific IAM Market Size (In USD Mn)
7.1. Projected Growth Dynamics
7.2. Key Factors Impacting Future Growth
Future Market Segmentation for Asia Pacific IAM Market
8.1. By Component (In Value %)
8.2. By Deployment Type (In Value %)
8.3. By Organization Size (In Value %)
8.4. By Industry Vertical (In Value %)
8.5. By Country (In Value %)
Asia Pacific IAM Market Analysts Recommendations
9.1. Total Addressable Market (TAM), Serviceable Available Market (SAM), Serviceable Obtainable Market (SOM) Analysis
9.2. Customer Segmentation and Profiling
9.3. Targeted Marketing Initiatives
9.4. Strategic Positioning and White Space Identification
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
The initial phase involved mapping the ecosystem of the Asia Pacific IAM market, covering stakeholders from technology providers to end-users. Extensive secondary research, combined with proprietary databases, helped identify critical variables such as regulatory trends and cybersecurity needs.
Step 2: Market Analysis and Construction
This phase included historical data analysis for the Asia Pacific IAM market, covering growth rates, technological adoption, and end-user demand. Revenue estimations were verified through assessment of product quality and service standards.
Step 3: Hypothesis Validation and Expert Consultation
We conducted hypothesis validation through direct interactions with IAM industry experts from leading companies. Insights from these discussions allowed us to refine and confirm the reliability of our revenue and demand projections.
Step 4: Research Synthesis and Final Output
The final phase consolidated insights from IAM solution providers to validate segmented data on product and service offerings, consumer behavior, and adoption trends, ensuring a comprehensive, validated overview of the market.
Frequently Asked Questions
01 How big is the Asia Pacific IAM Market?
The Asia Pacific Identity and Access Management market is valued at USD 6.6 billion, driven by increased digital transformation efforts and government-backed digital identity initiatives.
02 What are the primary drivers of the Asia Pacific IAM Market?
Key drivers in the Asia Pacific Identity and Access Management market include cybersecurity concerns, regulatory mandates, and the adoption of cloud-based IAM solutions that cater to businesses prioritizing data protection and user authentication.
03 Which companies dominate the Asia Pacific IAM Market?
Leading players in the Asia Pacific Identity and Access Management market include IBM Corporation, Microsoft Corporation, and Oracle Corporation, which have extensive product portfolios, strategic partnerships, and strong regional presence.
04 What are the common deployment modes in the IAM Market?
IAM solutions in the Asia Pacific market are predominantly cloud-based, offering scalability and cost-efficiency, with on-premises solutions still preferred by sectors needing more control over data.
05 What challenges face the Asia Pacific IAM Market?
Integration issues with legacy systems and high initial deployment costs pose challenges for IAM solution adoption, particularly among SMEs in the Asia Pacific Identity and Access Management market.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















