
Global HSM (Hardware Security Module) Market Outlook to 2030
Region:Global
Author(s):Naman Rohilla
Product Code:KROD8173
December 2024
85
About the Report
Global Hardware Security Module (HSM) Market Overview
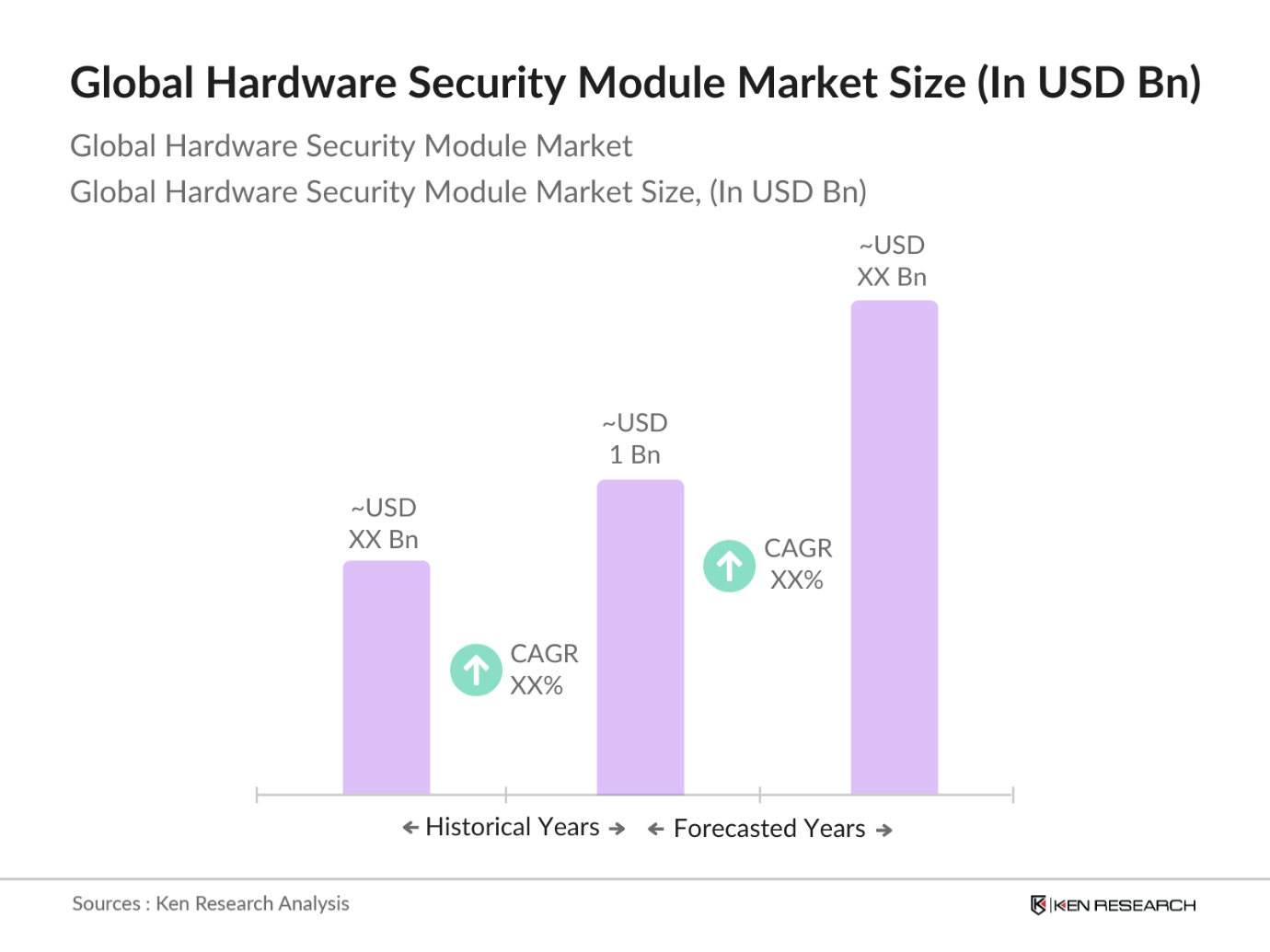
- The Global Hardware Security Module (HSM) market is valued at USD 1 billion, based on a five-year historical analysis. The market is primarily driven by the increasing demand for secure cryptographic key management, as companies and governments worldwide focus on enhancing data protection. The rapid adoption of cloud services and growing concerns about data breaches and cyber threats have accelerated the deployment of HSMs across industries like banking, financial services, healthcare, and government. As a critical part of cybersecurity infrastructure, HSMs ensure encryption, decryption, and authentication, contributing to their rising demand globally.
- Countries such as the United States, Germany, and Japan dominate the HSM market due to their advanced IT infrastructure, regulatory mandates, and technological expertise in data security. The United States leads the market due to the concentration of financial institutions, healthcare systems, and cloud providers, which rely heavily on secure cryptographic key management. Germanys leadership is driven by strict data privacy regulations like GDPR, while Japan benefits from its robust electronics and IT sectors, fueling demand for secure data management solutions.
- Government regulations mandate strict compliance with security standards such as FIPS, PCI-DSS, and Common Criteria for data protection. As of 2023, the U.S. National Institute of Standards and Technology (NIST) certified over 15,000 HSMs for compliance with FIPS 140-2, ensuring secure key management in sectors like finance, healthcare, and government. These certifications are essential for organizations to meet industry-specific regulations, ensuring the safe handling of sensitive information.
Global Hardware Security Module (HSM) Market Segmentation
- By Type: The Global HSM market is segmented by type into network-attached HSMs, portable/USB HSMs, and PCIe-based HSMs. Among these, network-attached HSMs hold a dominant market share due to their widespread adoption in large enterprises that require scalable and secure cryptographic services. Their capability to manage multiple cryptographic operations over a network provides businesses with enhanced security and flexibility, making them the preferred option for industries such as banking and telecom. On the other hand, portable HSMs are gaining traction for their utility in personal use cases and smaller businesses.
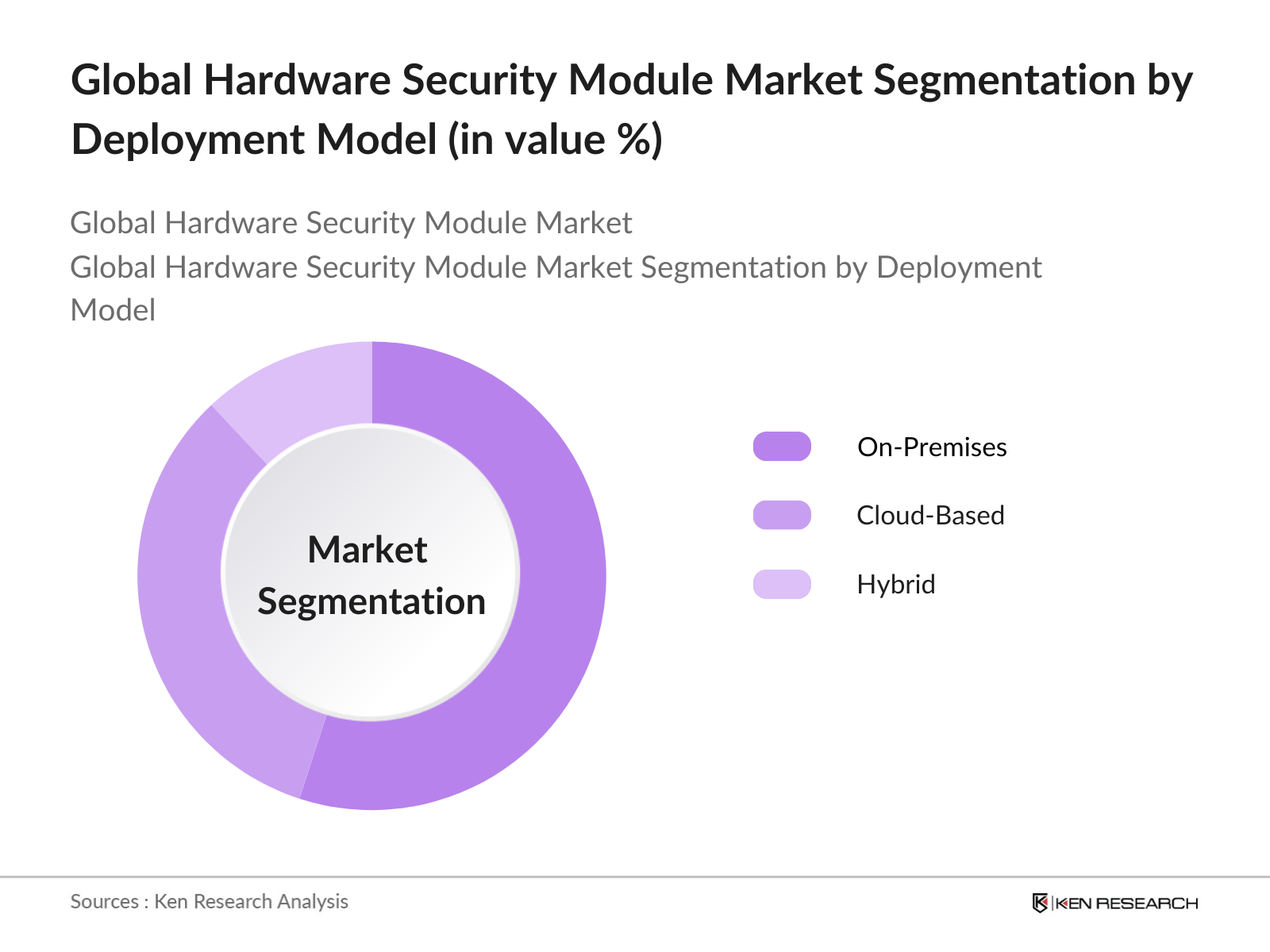
- By Deployment Model: The market is divided into on-premises, cloud-based, and hybrid deployment models. On-premises HSMs hold a dominant market share due to their strong presence in sectors such as banking and government that demand strict control over sensitive data. However, cloud-based HSMs are rapidly increasing in popularity, driven by the growing adoption of cloud computing services. Many enterprises are transitioning to cloud-based HSMs for greater scalability, flexibility, and cost efficiency, especially as cloud service providers are incorporating HSM functionalities directly into their offerings.
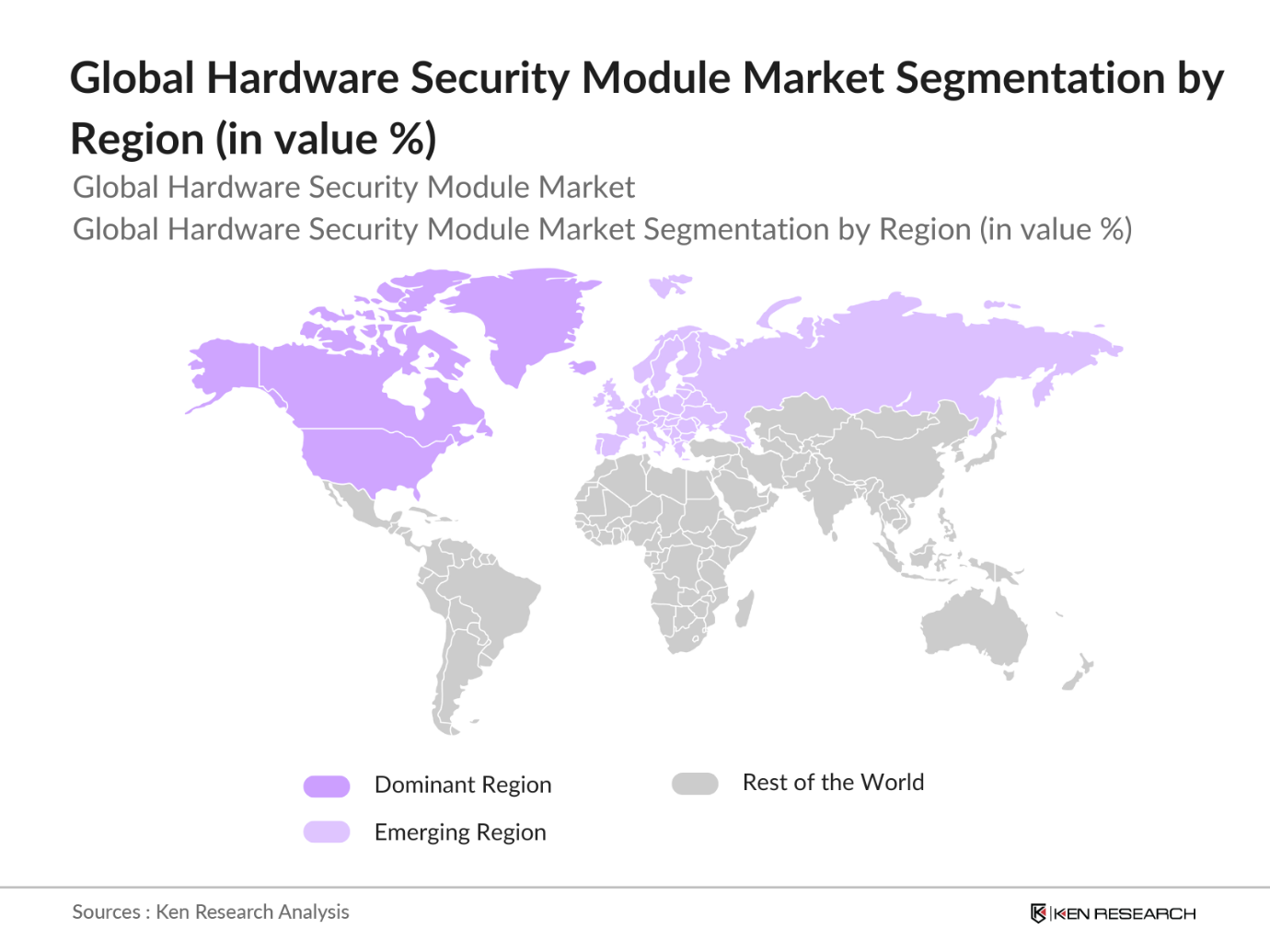
- By Region: The market is segmented into North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa. North America leads the global market, attributed to the high concentration of financial institutions, technology companies, and stringent data protection regulations. The United States is the largest market within this region due to its advanced cybersecurity infrastructure and regulatory requirements. Europe follows closely, driven by GDPR compliance and the growth of cloud computing, particularly in countries like Germany and the UK.
Global Hardware Security Module (HSM) Market Competitive Landscape
The Global HSM market is dominated by several key players, each contributing to the market through innovation and compliance with international security standards. Leading companies are focusing on expanding their product portfolios, integrating cloud capabilities, and forming strategic partnerships to meet the growing demand for secure data protection.
Global Hardware Security Module (HSM) Market Analysis
Global Hardware Security Module (HSM) Market Growth Drivers
- Growing Need for Cryptographic Security in Financial Transactions: The rising volume of global financial transactions necessitates robust cryptographic security to prevent data breaches and fraud. According to the Bank for International Settlements (BIS), global payment transaction volumes exceeded 1,500 billion in 2023, emphasizing the need for secure encryption methods such as Hardware Security Modules (HSMs). Cryptographic protection is becoming essential as cross-border and real-time payment systems grow, with institutions implementing HSMs to safeguard sensitive data, protect private keys, and ensure compliance with security standards in financial transactions.
- Increased Adoption of Cloud-Based HSMs: Cloud-based HSM solutions are gaining traction as businesses move to the cloud, driven by the need for scalable and secure data management. In 2023, the cloud computing market saw an increase of over 120 million enterprises adopting cloud services worldwide, according to the World Bank. Cloud HSMs provide enhanced key management services and seamless integration into cloud environments, allowing businesses to maintain high levels of security without managing physical hardware. The integration of these HSMs ensures data protection across various cloud platforms, reducing risks associated with data breaches and cyberattacks.
- Stringent Regulatory Requirements: Regulatory frameworks such as the General Data Protection Regulation (GDPR) and FIPS 140-2 mandate encryption for data protection, encouraging the adoption of HSMs. In 2023, the European Commission reported that over 35,000 companies faced fines for non-compliance with GDPR encryption standards. HSMs help organizations meet these regulatory requirements by securing cryptographic keys, ensuring that sensitive information is protected from unauthorized access. This has led to an increasing demand for HSMs in sectors that handle high volumes of personal data, including finance, healthcare, and e-commerce.
Global Hardware Security Module (HSM) Market Challenges
- High Initial Investment in HSM Infrastructure: The cost of deploying HSM infrastructure remains a challenge, particularly for small and medium enterprises (SMEs). According to the International Monetary Fund (IMF), enterprises in developing economies often allocate 25% of their IT budgets to data security, making it difficult for smaller businesses to invest in high-end HSM solutions. Despite the benefits of enhanced security, the upfront capital expenditure for HSMs, including hardware, installation, and maintenance, continues to limit widespread adoption, especially for firms with limited financial resources.
- Integration Challenges with Legacy Systems: Many businesses still operate on legacy systems, which pose technical challenges when integrating modern HSM solutions. The World Bank reports that 30% of financial institutions globally rely on legacy infrastructure as of 2023, creating barriers to adopting cutting-edge cryptographic technology. HSMs require specialized integration protocols to function with older systems, often leading to operational disruptions or costly upgrades. This challenge is particularly pronounced in highly regulated sectors, where downtime or failures in security could result in penalties and loss of customer trust.
Global Hardware Security Module (HSM) Market Future Outlook
Over the next five years, the Global HSM market is expected to show steady growth, driven by increasing regulatory requirements, the expansion of cloud-based HSM solutions, and the rise of IoT devices requiring secure data encryption. The demand for quantum-resistant cryptography is expected to further fuel market growth, as companies prepare for future security threats posed by quantum computing. Additionally, advancements in AI and machine learning will enable enhanced automation and intelligence in cryptographic key management, making HSMs even more integral to global cybersecurity frameworks.
Global Hardware Security Module (HSM) Market Opportunities
- Integration of HSM in IoT Devices for Enhanced Security: With the growing number of connected devices, the demand for IoT security solutions is expanding. The International Telecommunication Union (ITU) states that the number of IoT devices reached 18 billion in 2023. HSMs are increasingly being integrated into IoT ecosystems to ensure secure data exchange and device authentication, protecting sensitive data from cyberattacks. This trend is driven by industries such as automotive, healthcare, and smart cities, which require robust cryptographic solutions to protect real-time data.
- Quantum-Resistant Cryptography Solutions: As quantum computing capabilities advance, the need for quantum-resistant cryptographic solutions is becoming more critical. The National Institute of Standards and Technology (NIST) has initiated the development of post-quantum cryptographic standards, with many HSM providers already working on implementing these solutions. Quantum-resistant encryption is expected to safeguard data in sectors such as finance and defense, where sensitive information must remain secure against future quantum threats. The World Economic Forum (WEF) notes that securing quantum-vulnerable assets is a key priority for industries as of 2024.
Scope of the Report
|
By Type |
Network-Attached HSMs Portable/USB HSMs PCIe-Based HSMs |
|
By Deployment Model |
On-Premises Cloud-Based Hybrid |
|
By Industry |
Banking and Financial Services (BFSI) Healthcare Government Retail and E-commerce Telecommunications |
|
By End-User |
Large Enterprises Small and Medium Enterprises (SMEs) |
|
By Region |
North America Europe Asia-Pacific Middle East & Africa Latin America |
Products
Key Target Audience
Hardware Security Module Manufacturers
Cryptographic Service Providers
Data Encryption Technology Providers
Banking, Financial Services & Insurance (BFSI) Sector
Government and Regulatory Bodies (FIPS, GDPR Compliance Bodies)
Telecommunication Companies
Banks and Financial Institutions
Healthcare Providers
Investor and Venture Capitalist Firms
Companies
Players Mentioned in the Report
Thales Group
IBM Corporation
Atos SE
Hewlett Packard Enterprise
Utimaco GmbH
Futurex
Gemalto (Now part of Thales)
Entrust Datacard
Securosys SA
Cryptomathic
Table of Contents
1. Global HSM Market Overview
1.1 Definition and Scope
1.2 Market Taxonomy
1.3 Market Growth Rate
1.4 Market Segmentation Overview
2. Global HSM Market Size (USD Billion)
2.1 Historical Market Size and Analysis
2.2 Year-On-Year Growth Analysis
2.3 Key Developments and Market Milestones
3. Global HSM Market Analysis
3.1 Growth Drivers
3.1.1 Growing Need for Cryptographic Security in Financial Transactions
3.1.2 Increased Adoption of Cloud-Based HSMs
3.1.3 Regulatory Requirements Driving Compliance (GDPR, FIPS)
3.1.4 Rising Cybersecurity Threats and Data Breach Concerns
3.1.5 Expansion of Digital Payment and E-commerce Sectors
3.2 Market Challenges
3.2.1 High Initial Investment and Maintenance Costs
3.2.2 Integration Challenges with Legacy Systems
3.2.3 Limited Awareness and Knowledge among SMEs
3.2.4 Shortage of Skilled Professionals in Data Security
3.2.5 Complexities in Managing Multi-Cloud Environments
3.3 Market Opportunities
3.3.1 Integration of HSM in IoT Devices for Enhanced Security
3.3.2 Growing Demand for Quantum-Resistant Cryptography Solutions
3.3.3 Expansion into Emerging Markets with Rising Digitization
3.3.4 Adoption of AI and Machine Learning in Cryptographic Security
3.3.5 Increased Investment in Data Privacy and Regulatory Compliance
3.4 Industry Trends
3.4.1 Rise of AI and Machine Learning in HSM Solutions
3.4.2 Mobile and Hybrid HSM Solutions for Flexibility and Accessibility
3.4.3 Adoption of Multi-Cloud Strategies with HSM Integration
3.4.4 Shift Toward Edge Computing and On-Device Encryption
3.4.5 Growing Interest in Blockchain-Based HSM Solutions
3.5 Government Regulations
3.5.1 Compliance Standards (FIPS, PCI-DSS, GDPR)
3.5.2 Data Privacy and Protection Laws by Region
3.5.3 Cross-Border Data Protection and Encryption Requirements
3.6 SWOT Analysis
3.6.1 Strengths (e.g., High Demand for Secure Data Management)
3.6.2 Weaknesses (e.g., High Costs, Complexity)
3.6.3 Opportunities (e.g., Quantum-Resistant Solutions, IoT Expansion)
3.6.4 Threats (e.g., Cybersecurity Risks, Regulatory Challenges)
3.7 Stakeholder Ecosystem
3.7.1 Key Suppliers and Component Providers
3.7.2 Hardware Security Module Manufacturers
3.7.3 End-User Industries (BFSI, Government, Healthcare, etc.)
3.7.4 Cryptographic Service Providers and Integrators
3.8 Porters Five Forces Analysis
3.8.1 Supplier Power
3.8.2 Buyer Power
3.8.3 Threat of Substitutes
3.8.4 Threat of New Entrants
3.8.5 Competitive Rivalry
3.9 Competition Ecosystem
3.9.1 Industry Competition Analysis
3.9.2 Market Share of Key Players
3.9.3 Strategic Initiatives (Mergers, Partnerships, R&D)
3.9.4 Investment Landscape and Funding Sources
4. Global HSM Market Segmentation
4.1 By Type (Value %)
4.1.1 Network-Attached HSMs
4.1.2 Portable/USB HSMs
4.1.3 PCIe-Based HSMs
4.2 By Deployment Model (Value %)
4.2.1 On-Premises
4.2.2 Cloud-Based
4.2.3 Hybrid
4.3 By Industry (Value %)
4.3.1 Banking and Financial Services (BFSI)
4.3.2 Healthcare
4.3.3 Government
4.3.4 Retail and E-commerce
4.3.5 Telecommunications
4.4 By End-User (Value %)
4.4.1 Large Enterprises
4.4.2 Small and Medium Enterprises (SMEs)
4.5 By Region (Value %)
4.5.1 North America
4.5.2 Europe
4.5.3 Asia-Pacific
4.5.4 Middle East & Africa
4.5.5 Latin America
5. Global HSM Market Competitive Landscape
5.1 Key Players Overview
5.2 Cross-Comparison Parameters
5.3 Market Share Analysis
5.4 Strategic Initiatives and R&D Investments
5.5 Mergers, Acquisitions, and Partnerships
6. Global HSM Market Regulatory Framework
6.1 Compliance Standards (e.g., FIPS, PCI-DSS, GDPR)
6.2 Sector-Specific Requirements
6.3 Cross-Border Data Protection Regulations
7. Global HSM Market Future Outlook
7.1 Future Market Size Projections (USD Billion)
7.2 Key Factors Shaping Future Market Trends
8. Global HSM Market Future Segmentation
8.1 By Type
8.2 By Deployment Model
8.3 By Industry
8.4 By End-User
8.5 By Region
9. Global HSM Market Analysts Recommendations
9.1 White Space Opportunity Analysis
9.2 Market Expansion Strategies
9.3 Competitive Positioning and Differentiation Strategies
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
In this phase, the focus is on mapping out the entire ecosystem of the HSM market. This is achieved by conducting extensive secondary research using trusted industry databases and official government publications. The aim is to identify key factors such as technological advancements, regulatory requirements, and industry adoption patterns.
Step 2: Market Analysis and Construction
This step involves collecting and analyzing historical data on HSM adoption across different industries. Factors such as market penetration, the number of HSM installations in critical industries like banking, and data encryption trends are analyzed to provide a detailed understanding of market dynamics and performance.
Step 3: Hypothesis Validation and Expert Consultation
Insights derived from the market analysis are then validated through consultations with industry experts and HSM providers. These consultations are conducted via interviews and surveys, allowing the validation of market hypotheses and ensuring that the data reflects real-time industry trends.
Step 4: Research Synthesis and Final Output
The final phase focuses on synthesizing the research findings to produce a comprehensive analysis of the HSM market. This includes verifying the accuracy of the data through multiple sources and ensuring that the final report is both reliable and actionable for business professionals and decision-makers.
Frequently Asked Questions
01. How big is the Global HSM Market?
The global HSM market is valued at USD 1 billion, driven by the increasing demand for cryptographic key management across industries, including financial services and healthcare.
02. What are the key challenges in the Global HSM Market?
Challenges include high implementation costs, technical complexities in integrating HSMs with legacy systems, and limited awareness of HSMs among smaller enterprises.
03. Who are the major players in the Global HSM Market?
Major players include Thales Group, IBM Corporation, Utimaco GmbH, Hewlett Packard Enterprise, and Futurex, all known for their innovative solutions and regulatory compliance.
04. What are the key growth drivers of the Global HSM Market?
Key drivers include the growing need for data protection, increasing regulatory mandates (such as GDPR and FIPS), and the rise in cloud computing, which necessitates advanced security measures.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















