
Global Identity and Access Management (IAM) Market Outlook 2030
Region:Global
Author(s):Shivani Mehra
Product Code:KROD1274
December 2024
89
About the Report
Global Identity and Access Management (IAM) Market Overview
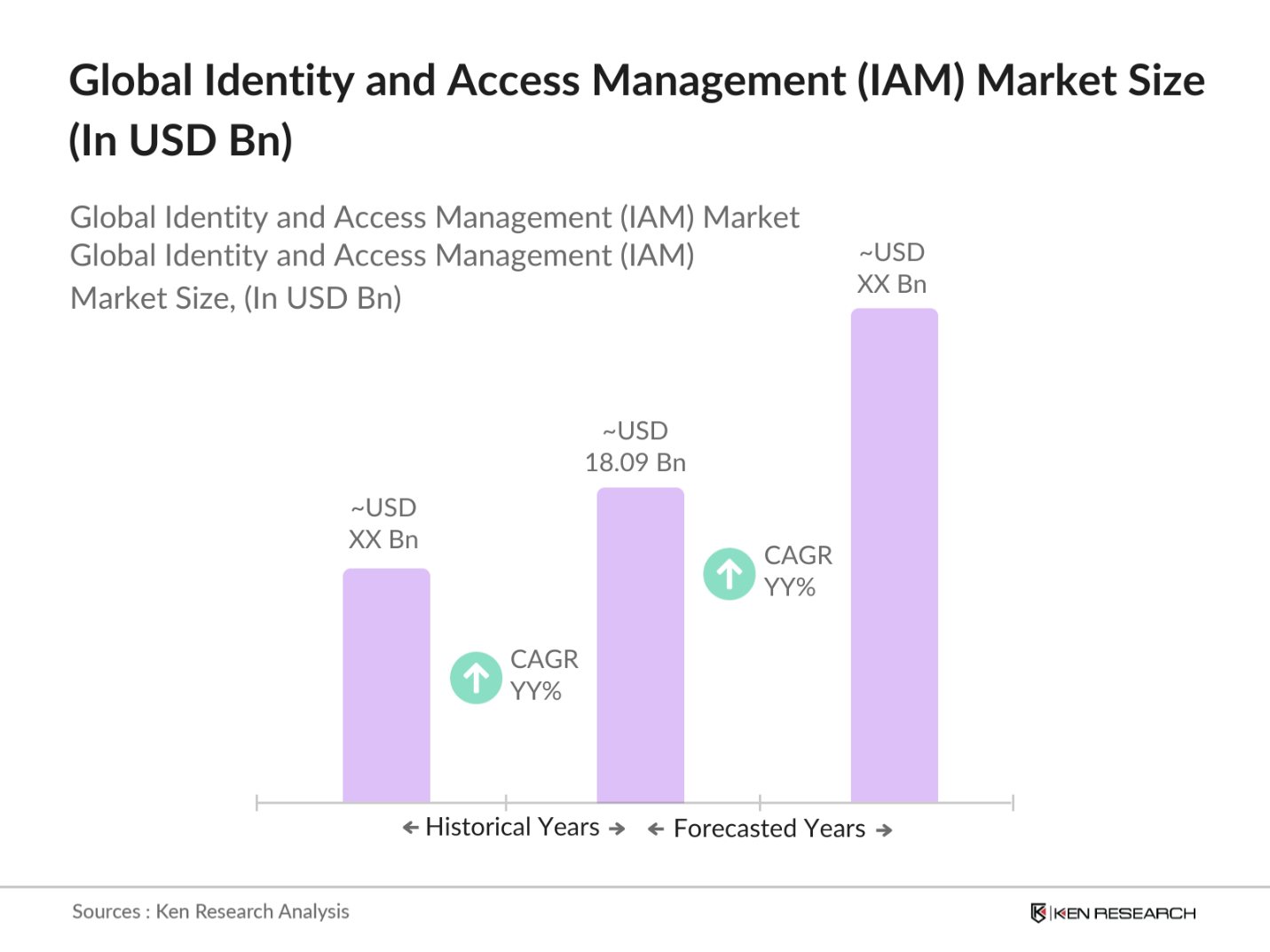
- The Global Identity and Access Management (IAM) market was valued at USD 18.09 billion, based on a five-year historical analysis. This market is primarily driven by the growing need for enhanced security in both private and public sector organizations. The increasing frequency of cyber-attacks, alongside stringent government regulations on data protection, has significantly contributed to the demand for IAM solutions. Cloud adoption across various industries has further amplified the need for identity and access management to safeguard sensitive data and manage digital identities efficiently.
- Countries like the United States, the United Kingdom, and Germany dominate the IAM market due to their well-established cybersecurity regulations and advanced technological infrastructure. The United States, with a vast number of enterprises implementing IAM solutions, leads the market. This dominance is further supported by the presence of top IAM providers, advanced IT infrastructure, and rigorous data privacy laws such as the California Consumer Privacy Act (CCPA). Similarly, European countries, particularly Germany, benefit from stringent data protection policies like the General Data Protection Regulation (GDPR), contributing to the widespread adoption of IAM solutions.
- National and international cybersecurity frameworks, such as the National Institute of Standards and Technology (NIST) guidelines, are setting new standards for identity management. In 2023, the U.S. government allocated $15 billion to strengthen its cybersecurity infrastructure, with IAM solutions being a key component of these initiatives. These frameworks are pushing businesses worldwide to adopt IAM systems for improved data security and compliance.
Global Identity and Access Management (IAM) Market Segmentation
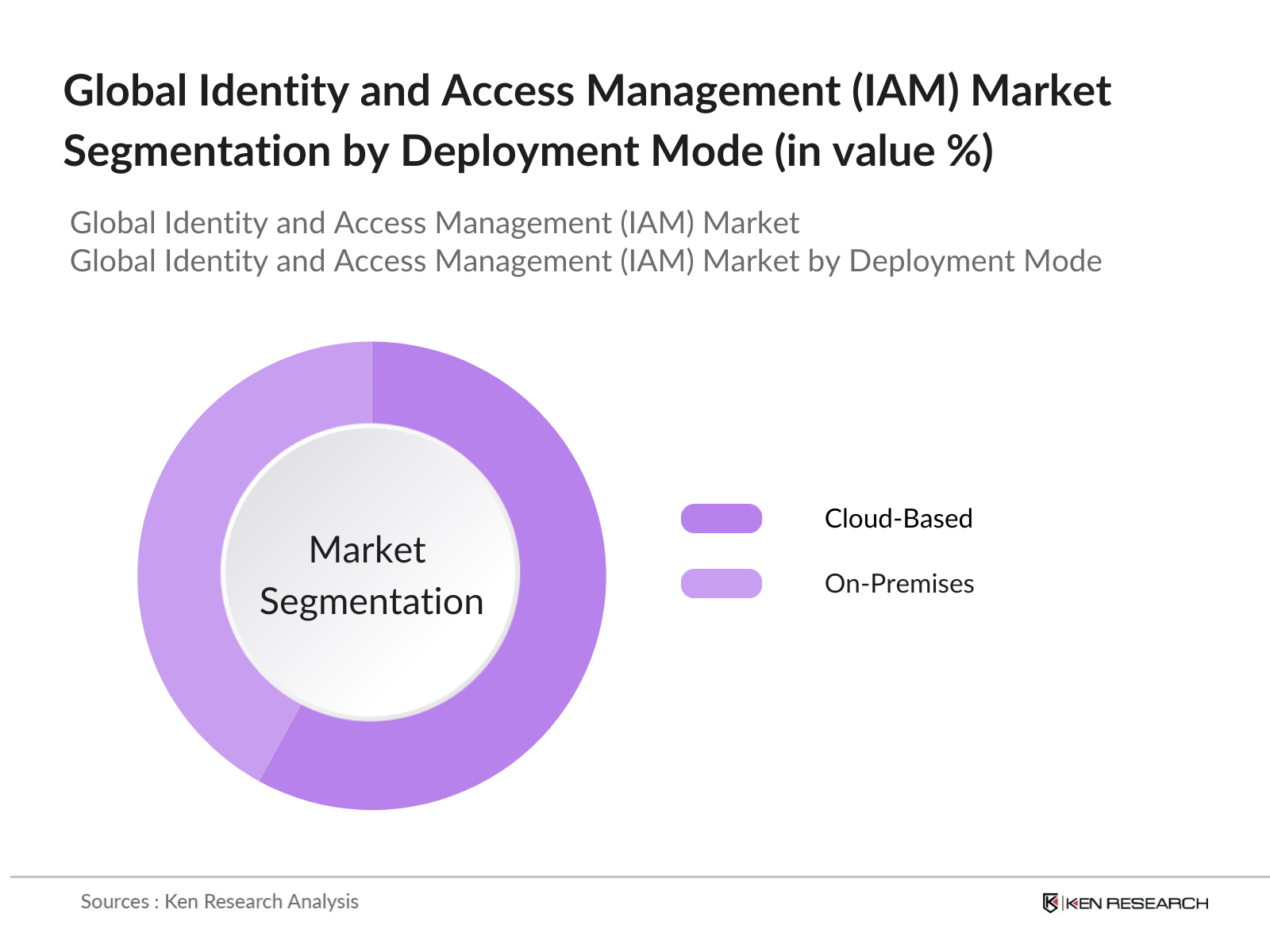
By Deployment Mode: The global IAM market is segmented by deployment mode into on-premises and cloud-based solutions. Cloud-based IAM solutions hold a dominant market share due to their scalability, flexibility, and lower upfront costs. Cloud platforms allow businesses to manage digital identities from remote locations, which has become particularly relevant with the rise of remote working environments. Moreover, the integration of IAM with cloud service providers such as AWS, Azure, and Google Cloud has made cloud deployment more attractive to enterprises.
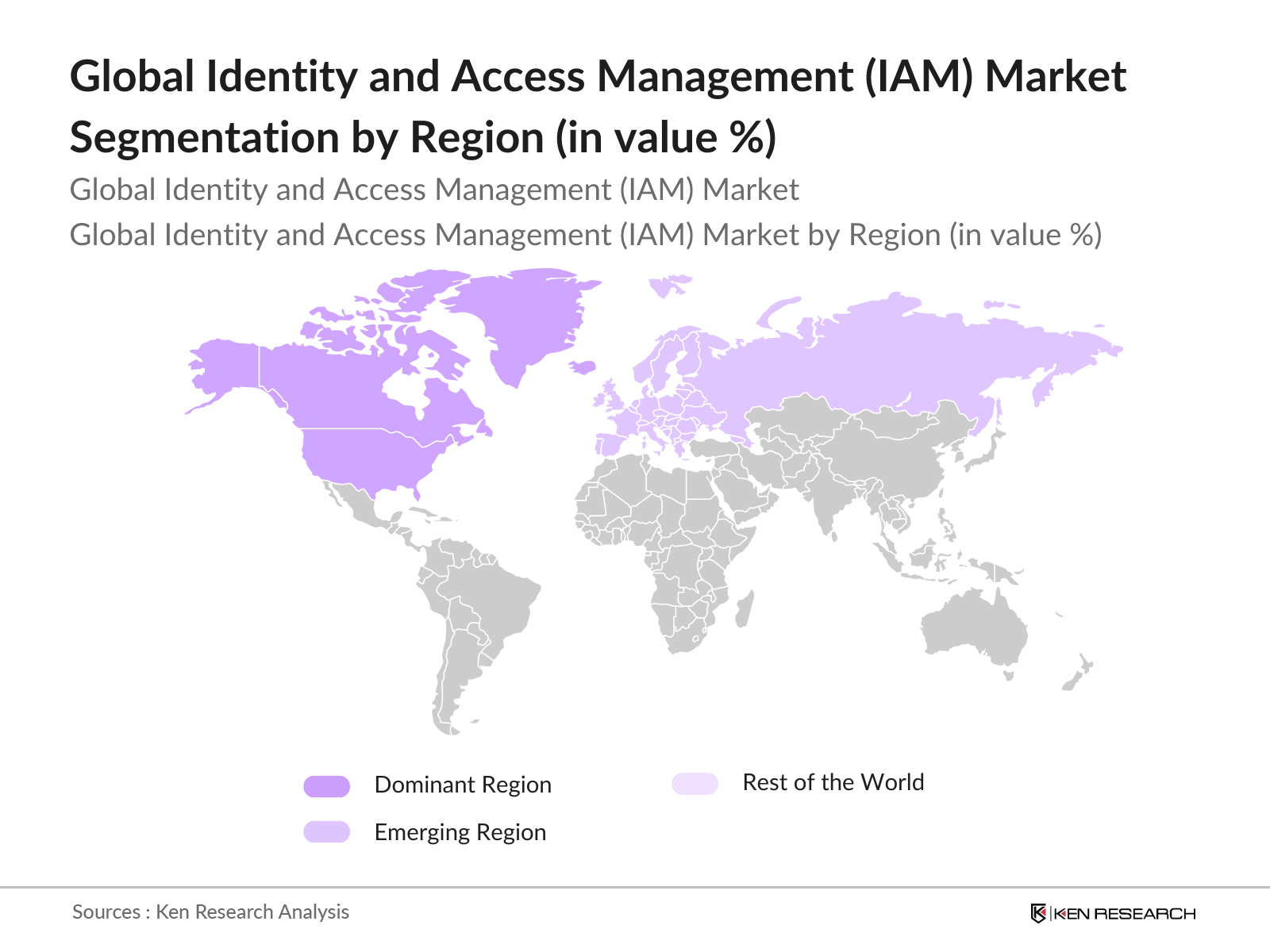
 By Region: The global IAM market is segmented by region into North America, Europe, Asia-Pacific, Middle East & Africa, and Latin America. North America leads the market, primarily due to the high concentration of key IAM providers, strong regulatory frameworks, and increased awareness regarding cybersecurity. Europe, driven by GDPR and other data protection mandates, follows closely. Asia-Pacific, though still growing, is emerging as a key region due to the rapid digital transformation across industries and increasing adoption of IAM solutions in countries such as India, China, and Japan.
By Region: The global IAM market is segmented by region into North America, Europe, Asia-Pacific, Middle East & Africa, and Latin America. North America leads the market, primarily due to the high concentration of key IAM providers, strong regulatory frameworks, and increased awareness regarding cybersecurity. Europe, driven by GDPR and other data protection mandates, follows closely. Asia-Pacific, though still growing, is emerging as a key region due to the rapid digital transformation across industries and increasing adoption of IAM solutions in countries such as India, China, and Japan.
 Global Identity and Access Management (IAM) Market Competitive Landscape
Global Identity and Access Management (IAM) Market Competitive Landscape
The Global IAM market is highly competitive, with key players actively investing in innovation and strategic partnerships. The consolidation of top global companies and the entry of new players underline the competitive nature of this market. Leading vendors like Microsoft and IBM continue to dominate the market, offering comprehensive IAM platforms, while niche players focus on providing specialized solutions like Privileged Access Management (PAM) and Biometric Authentication.
|
Company |
Establishment Year |
Headquarters |
Product Portfolio |
Revenue (2023) |
No. of Employees |
Market Share |
Regional Presence |
R&D Investments |
|
Microsoft Corporation |
1975 |
Redmond, Washington, USA |
||||||
|
IBM Corporation |
1911 |
Armonk, New York, USA |
||||||
|
Oracle Corporation |
1977 |
Austin, Texas, USA |
||||||
|
Ping Identity Corporation |
2002 |
Denver, Colorado, USA |
||||||
|
SailPoint Technologies |
2005 |
Austin, Texas, USA |
Global Identity and Access Management (IAM) Market Analysis
Market Growth Drivers
- Increase in Cybersecurity Threats: The surge in cybersecurity incidents has pushed the demand for Identity and Access Management (IAM) solutions. In 2023 alone, over 1.1 billion cyberattacks were reported globally, highlighting the critical need for robust IAM systems to safeguard sensitive information. The World Bank notes that cybercrime-related costs amounted to over $6 trillion in 2022, forcing governments and corporations to adopt stringent security measures, including IAM solutions. This urgency for stronger cybersecurity protections is becoming one of the key drivers for IAM adoption across industries.
- Government Regulations on Data Security: Stringent government regulations are further driving the need for IAM solutions. Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) require companies to implement robust security frameworks, including identity management protocols. In 2022, over 450,000 data breaches were recorded in Europe, emphasizing the importance of complying with data protection laws. Countries like the USA have introduced similar cybersecurity standards, pushing businesses to adopt IAM solutions to avoid hefty fines.
- Expansion of Digital Transformation Initiatives: Governments and corporations are accelerating digital transformation initiatives to enhance operational efficiency and customer experiences. According to the World Bank, over $2.5 trillion was allocated toward global digital transformation initiatives in 2023, with a significant portion earmarked for cybersecurity measures such as IAM. These initiatives are reshaping industries like finance, healthcare, and retail, where the integration of IAM systems plays a crucial role in ensuring secure access to digital services and platforms.
Market Challenges
- High Implementation Costs: The costs associated with implementing IAM solutions can be prohibitive, especially for small and medium enterprises (SMEs). The average cost of deploying a robust IAM system in large enterprises ranges from $2 million to $5 million, according to data from government IT spending reports in 2023. This significant expense creates a barrier for smaller organizations looking to invest in identity management solutions, which can slow down the adoption of these technologies despite the growing need for them.
- Lack of Skilled Workforce for IAM Solutions: A shortage of skilled professionals trained in implementing and managing IAM systems is another significant challenge. According to the IMF, the global cybersecurity workforce gap reached 3.5 million in 2023, with a large portion of this shortage in IAM-specific expertise. This talent gap is particularly challenging for businesses looking to maintain compliance with stringent security regulations and ensure efficient operation of IAM systems.
Global Identity and Access Management (IAM) Market Future Outlook
Over the next five years, the Global IAM market is expected to witness steady growth, driven by factors such as the increasing prevalence of cyber threats, rapid adoption of cloud services, and the rising need for efficient digital identity management. Key sectors like BFSI, healthcare, and retail will continue to prioritize IAM solutions to ensure data protection and compliance with stringent regulations. Furthermore, advancements in artificial intelligence and blockchain technologies are set to revolutionize IAM, offering more secure and efficient methods for identity verification and access control.
Market Opportunities:
- Integration with Zero Trust Security Models: The Zero Trust security model, which requires continuous verification of users, is gaining traction in the IAM space. In 2023, the U.S. Department of Defense mandated Zero Trust adoption for its contractors, reflecting a global shift toward this security framework. As companies move away from traditional perimeter-based security models, the integration of IAM with Zero Trust architectures will be a critical trend shaping the industry.
- Emergence of Blockchain-Based Identity Management: Blockchain technology is being explored as a secure and decentralized approach to identity management. Governments and corporations are investing in blockchain projects to enhance the security and efficiency of identity verification. In 2023, the global blockchain investment exceeded $250 billion, with identity management solutions representing a significant share. Blockchains ability to provide secure, tamper-proof identity verification could revolutionize the IAM market in the coming years.
Scope of the Report
|
By Deployment Mode |
On-Premises Cloud-Based |
|
By Component |
Software Services |
|
By End-User Industry |
BFSI Healthcare Retail Government IT & Telecom |
|
By Authentication Type |
Single-Factor Authentication Multi-Factor Authentication Biometric Authentication |
|
By Region |
North America Europe Asia-Pacific Middle East & Africa Latin America |
Products
Key Target Audience
IAM Software Vendors
BFSI Sector
Healthcare Providers
Retail Sector
Government and Regulatory Bodies (e.g., GDPR, CCPA)
IT and Telecom Companies
Investments and Venture Capitalist Firms
Cloud Service Providers
Companies
Players Mention in the Report
Microsoft Corporation
IBM Corporation
Oracle Corporation
Ping Identity Corporation
SailPoint Technologies Holdings, Inc.
Broadcom Inc.
Okta Inc.
OneLogin, Inc.
Centrify Corporation
RSA Security LLC
ForgeRock, Inc.
HID Global Corporation
Auth0, Inc.
CyberArk Software Ltd.
SecureAuth Corporation
Table of Contents
01. Global Identity and Access Management Market Overview
1.1 Definition and Scope
1.2 Market Taxonomy
1.3 Market Growth Rate
1.4 Market Segmentation Overview
02. Global Identity and Access Management Market Size (In USD Bn)
2.1 Historical Market Size
2.2 Year-On-Year Growth Analysis
2.3 Key Market Developments and Milestones
03. Global Identity and Access Management Market Analysis
3.1 Growth Drivers
3.1.1 Increase in Cybersecurity Threats
3.1.2 Rising Adoption of Cloud-Based Solutions
3.1.3 Government Regulations on Data Security
3.1.4 Expansion of Digital Transformation Initiatives
3.2 Market Challenges
3.2.1 High Implementation Costs
3.2.2 Complex Integration with Legacy Systems
3.2.3 Lack of Skilled Workforce for IAM Solutions
3.3 Opportunities
3.3.1 Increasing Demand for Multi-Factor Authentication
3.3.2 Growth in IAM Solutions for SMEs
3.3.3 Advancements in AI and Machine Learning for Identity Management
3.4 Trends
3.4.1 Integration with Zero Trust Security Models
3.4.2 Emergence of Blockchain-based Identity Management
3.4.3 Growing Use of Biometric Authentication
3.5 Government Regulation
3.5.1 Data Protection Laws (GDPR, CCPA, HIPAA)
3.5.2 Cybersecurity Frameworks and Standards
3.5.3 Compliance with National Security Regulations
3.6 SWOT Analysis
3.7 Stakeholder Ecosystem
3.8 Porters Five Forces
3.9 Competition Ecosystem
04. Global Identity and Access Management Market Segmentation
4.1 By Deployment Mode (In Value %)
4.1.1 On-Premises
4.1.2 Cloud-Based
4.2 By Component (In Value %)
4.2.1 Software
4.2.2 Services
4.3 By End-User Industry (In Value %)
4.3.1 BFSI
4.3.2 Healthcare
4.3.3 Retail
4.3.4 Government
4.3.5 IT & Telecom
4.4 By Authentication Type (In Value %)
4.4.1 Single-Factor Authentication
4.4.2 Multi-Factor Authentication
4.4.3 Biometric Authentication
4.5 By Region (In Value %)
4.5.1 North America
4.5.2 Europe
4.5.3 Asia-Pacific
4.5.4 Middle East & Africa
4.5.5 Latin America
05. Global Identity and Access Management Market Competitive Analysis
5.1 Detailed Profiles of Major Companies
5.1.1 Microsoft Corporation
5.1.2 IBM Corporation
5.1.3 Oracle Corporation
5.1.4 Broadcom Inc.
5.1.5 Okta Inc.
5.1.6 Ping Identity Corporation
5.1.7 SailPoint Technologies Holdings, Inc.
5.1.8 OneLogin, Inc.
5.1.9 Centrify Corporation
5.1.10 RSA Security LLC
5.1.11 ForgeRock, Inc.
5.1.12 HID Global Corporation
5.1.13 Auth0, Inc.
5.1.14 CyberArk Software Ltd.
5.1.15 SecureAuth Corporation
5.2 Cross Comparison Parameters (Headquarters, No. of Employees, Inception Year, Revenue, Market Share, Regional Presence, Product Portfolio, Partnerships)
5.3 Market Share Analysis
5.4 Strategic Initiatives
5.5 Mergers and Acquisitions
5.6 Investment Analysis
5.7 Venture Capital Funding
5.8 Government Grants
5.9 Private Equity Investments
06. Global Identity and Access Management Market Regulatory Framework
6.1 Data Privacy Laws and Regulations
6.2 Security Standards and Certifications
6.3 Regulatory Bodies and Enforcement Agencies
07. Global Identity and Access Management Future Market Size (In USD Bn)
7.1 Future Market Size Projections
7.2 Key Factors Driving Future Market Growth
08. Global Identity and Access Management Future Market Segmentation
8.1 By Deployment Mode (In Value %)
8.2 By Component (In Value %)
8.3 By End-User Industry (In Value %)
8.4 By Authentication Type (In Value %)
8.5 By Region (In Value %)
09. Global Identity and Access Management Market Analysts Recommendations
9.1 TAM/SAM/SOM Analysis
9.2 Customer Cohort Analysis
9.3 Marketing Initiatives
9.4 White Space Opportunity Analysis
Disclaimer
Contact Us
Research Methodology
Step 1: Identification of Key Variables
The initial phase involves constructing an ecosystem map that includes all major stakeholders in the IAM market. This step is based on extensive desk research utilizing a combination of proprietary databases and secondary sources. The primary objective is to identify critical variables influencing the IAM market, such as technological adoption, regulatory environment, and demand shifts.
Step 2: Market Analysis and Construction
During this phase, historical data regarding the IAM market is compiled and analyzed. This includes evaluating the adoption rates of IAM solutions, market penetration by segment, and the associated revenue generation. Additional factors such as the impact of regulations like GDPR and CCPA are also considered to understand the overall market dynamics.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses developed during the analysis phase are validated through consultations with industry experts and company representatives. These consultations provide operational and financial insights that help refine the market data and ensure accuracy.
Step 4: Research Synthesis and Final Output
The final phase involves direct engagement with IAM solution providers and end-user companies to validate and complement the data obtained. This ensures the final report offers a comprehensive and accurate analysis of the IAM market.
Frequently Asked Questions
01. How big is the Global Identity and Access Management Market?
The Global Identity and Access Management market was valued at USD 18.09 billion, driven by the growing demand for secure digital identity management solutions and compliance with regulatory standards.
02. What are the challenges in the IAM Market?
Challenges in the IAM market include high implementation costs, integration with legacy systems, and the lack of skilled professionals capable of managing advanced IAM technologies.
03. Who are the major players in the IAM Market?
Key players in the IAM market include Microsoft, IBM, Oracle, Ping Identity, and SailPoint Technologies. These companies dominate the market due to their robust IAM platforms, global presence, and continuous investment in R&D.
04. What are the growth drivers of the IAM Market?
The IAM market is driven by increasing cybersecurity threats, the rise of cloud adoption, and stringent government regulations such as GDPR and CCPA, which mandate secure identity management practices.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















