
Indonesia SOC as a Service Market Outlook to 2030
Region:Asia
Author(s):Sanjeev
Product Code:KROD2515
December 2024
92
About the Report
Indonesia SOC as a Service Market Overview
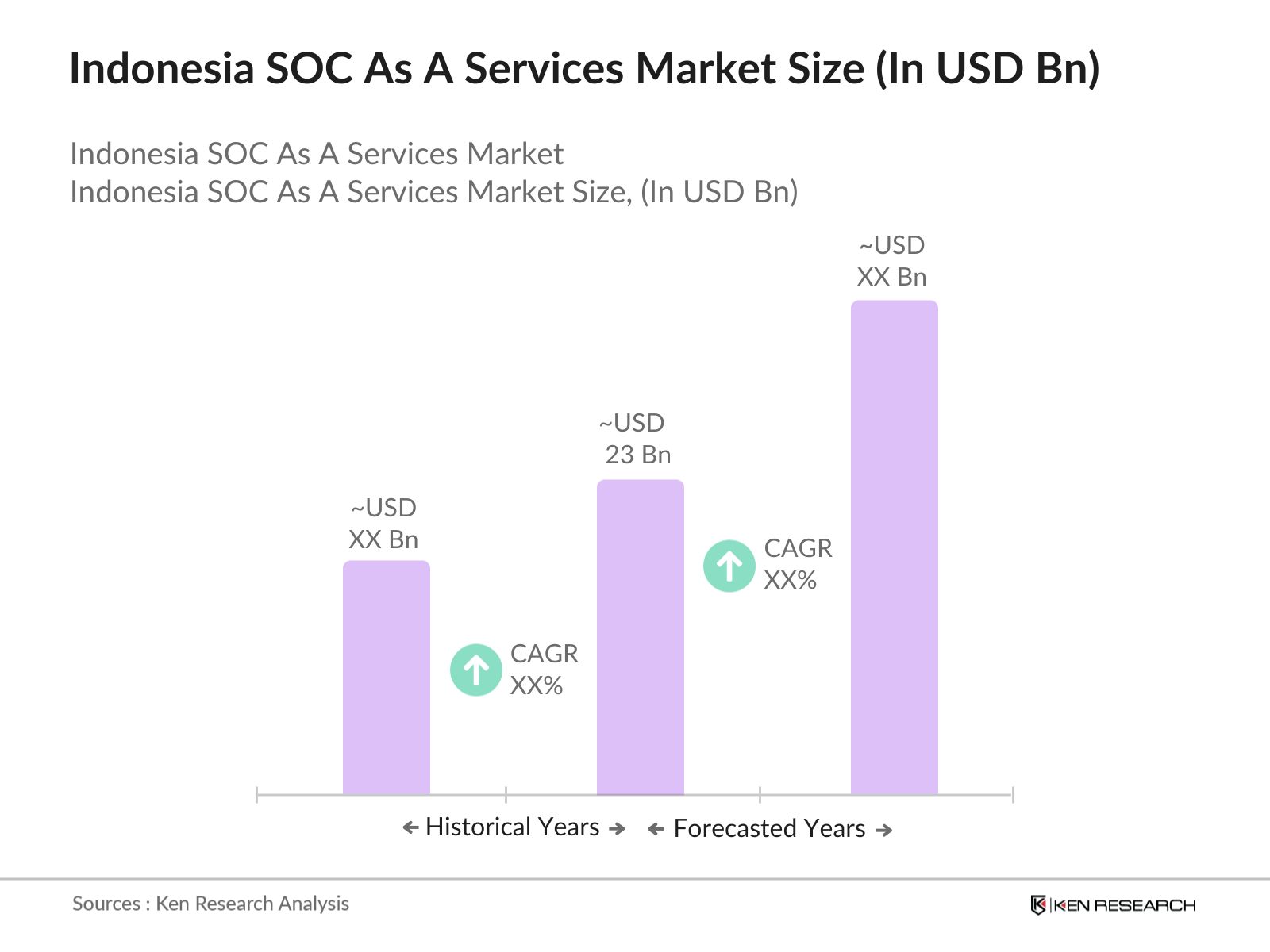
- The Indonesia SOC as a Service market is valued at USD 23 billion, with growth driven by an increasing frequency of cybersecurity incidents, rising digital adoption, and proactive government measures aimed at securing digital infrastructures. This growth is supported by substantial investments from large organizations and SMEs alike, as they seek advanced cybersecurity solutions to mitigate risks posed by emerging threats.
- Java and Sumatra dominate the market due to their high digital penetration rates and concentration of industries that prioritize cybersecurity. Java, in particular, leads the market with numerous financial and tech companies based in cities like Jakarta, which prioritize robust cybersecurity measures to protect critical data assets, while Sumatras manufacturing and industrial hubs emphasize secure SOC services to guard against cyber threats.
- Indonesias cybersecurity regulations, enforced by the National Cyber and Crypto Agency, require compliance with the 2021 Cybersecurity Bill, mandating organizations to adopt robust cybersecurity measures Link. This law has made SOC as a Service a critical requirement for businesses aiming to comply with national standards. By enforcing cybersecurity compliance, the government is fostering a more secure digital ecosystem, further driving demand for SOC solutions that help organizations meet legal obligations.
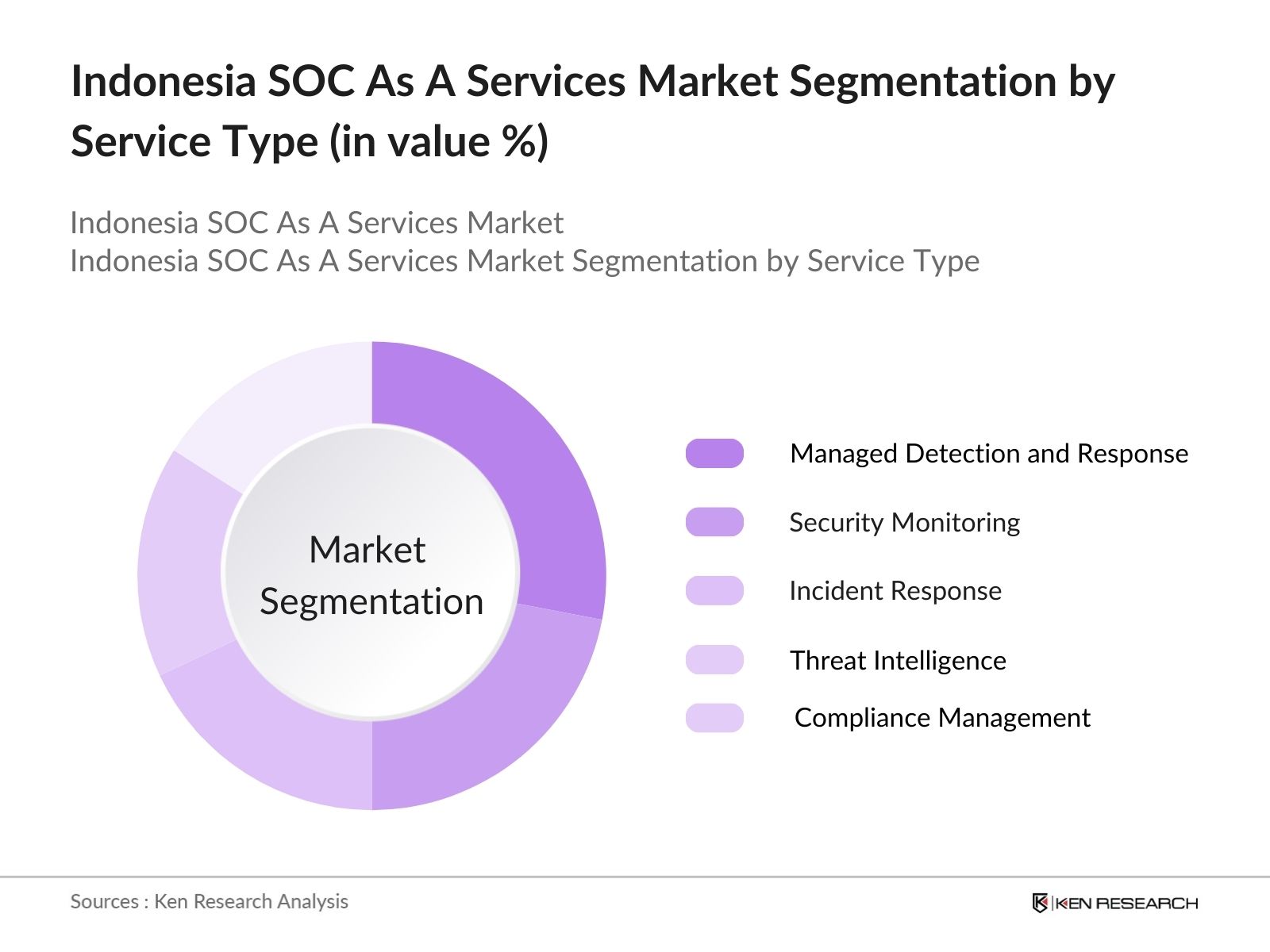
Indonesia SOC as a Service Market Segmentation
- By Service Type: The Indonesia SOC as a Service market is segmented by service type into managed detection and response, security monitoring, incident response, threat intelligence, and compliance management. Managed detection and response currently hold the largest market share due to its effectiveness in providing 24/7 threat detection, with many organizations in the finance and retail sectors adopting these services to preemptively identify and neutralize potential threats.
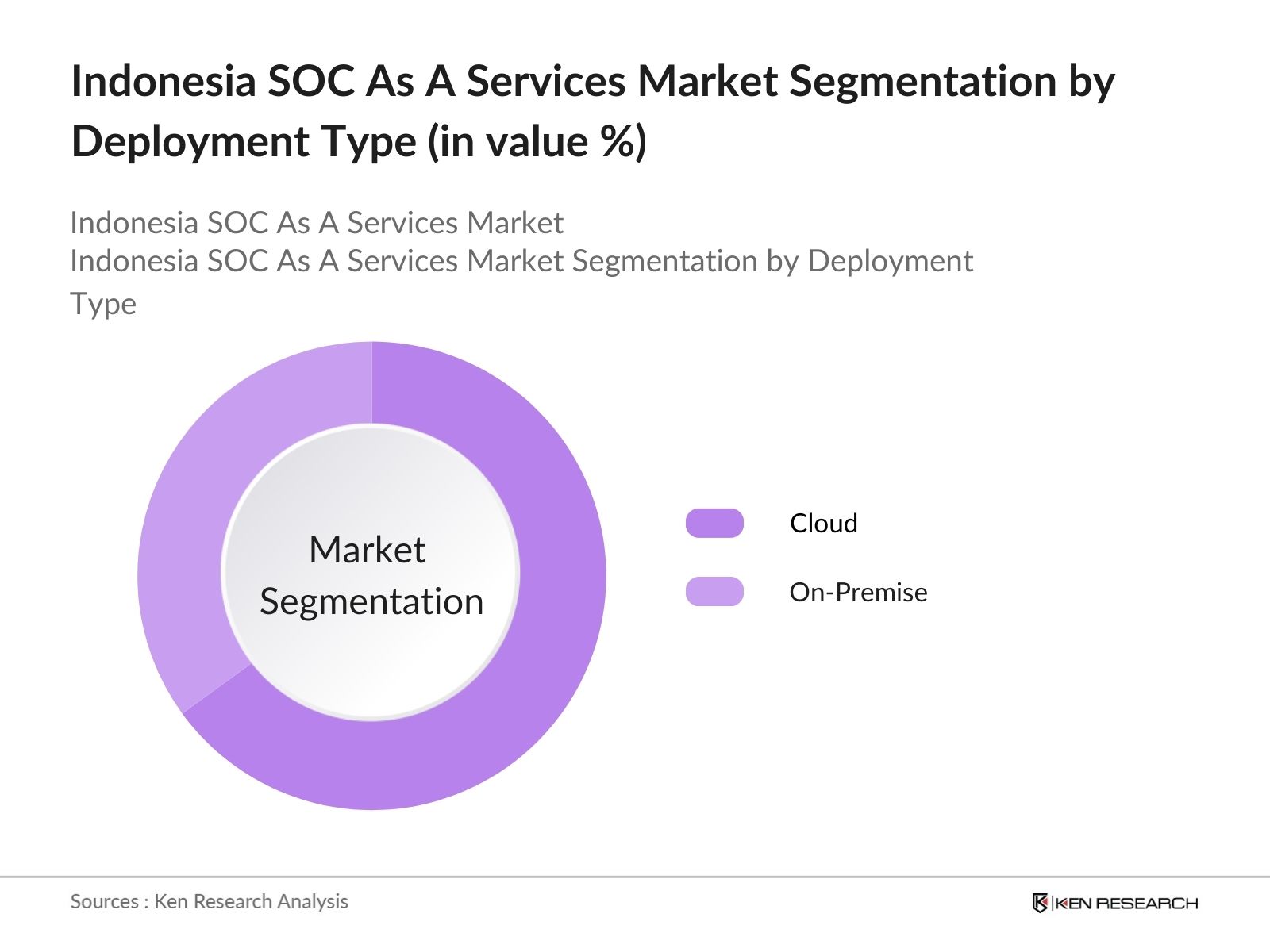
- By Deployment Type: The market is segmented by deployment type into cloud and on-premise solutions. Cloud-based SOC solutions dominate due to their flexibility and scalability, which appeal to both large enterprises and SMEs in Indonesia. The demand for cloud solutions is further fueled by lower upfront costs, ease of deployment, and compatibility with remote work environments, which many companies have transitioned to in recent years.
Indonesia SOC as a Service Market Competitive Landscape
The Indonesia SOC as a Service market is led by a blend of international and regional players, whose established presence and diversified service portfolios give them a competitive edge. Leading companies like IBM and Cisco, along with local players, dominate the market, driven by their expertise in cybersecurity and the strong partnerships they have established with Indonesian businesses.
Indonesia SOC as a Service Market Analysis
Growth Drivers
- Increasing Cybersecurity Threats: Indonesia has seen a marked increase in cybersecurity threats, with over 200 million detected cyberattacks in 2023, a significant surge from previous years, according to the National Cyber and Crypto Agency of Indonesia (BSSN) Link. This surge is attributed to the rapid growth of the digital economy, driven by increased internet penetration, which reached 212 million users in 2024, as reported by Indonesias Ministry of Communication and Information Technology Link. Rising attacks on key sectors, especially in finance and healthcare, highlight the urgent need for enhanced Security Operations Center (SOC) solutions to prevent data breaches and maintain digital security.
- Rapid Digital Transformation: Indonesias digital economy is projected to be one of the largest in Southeast Asia, growing significantly in recent years, backed by government support and private sector investment. With more than 25 million SMEs adopting digital platforms as of 2024, as per data from the Ministry of Cooperatives and SMEs Link, there is an increasing demand for SOC services to support secure digital operations. The continuous adoption of digital tools among SMEs and large corporations alike has created an environment where SOC services are critical for maintaining cybersecurity and ensuring data integrity.
- Government Initiatives for Cybersecurity: The Indonesian government has introduced various initiatives to bolster cybersecurity, including the implementation of the 2021 Cybersecurity Bill, aimed at strengthening the nations defenses against digital threats Link. In 2024, the government allocated over $10 million to cybersecurity frameworks, focusing on digital infrastructure protection across public and private sectors, per data from the Ministry of Finance Link. These initiatives create a supportive ecosystem for SOC as a Service providers to assist organizations in meeting new security compliance and standards.
Market Challenges
- High Operational Costs: Implementing and managing SOC services can be costly, with operational expenses heightened by Indonesias higher digital infrastructure costs compared to regional averages. In 2024, average monthly expenses for cybersecurity infrastructure in large enterprises were reported to be $50,000, as noted by the Ministry of Finance Link. This high expenditure challenges small and medium enterprises (SMEs), which are unable to afford these services. High operational costs therefore act as a deterrent to the widespread adoption of SOC solutions, especially for SMEs in Indonesia.
- Data Privacy Concerns: Data privacy remains a significant challenge for SOC providers, especially with the introduction of Indonesia's Personal Data Protection Law in 2022. Compliance costs associated with these regulations are substantial; for instance, the Ministry of Communication and Information Technology reported an average compliance cost of $100,000 for large enterprises in 2023 Link. These stringent requirements, while protecting consumer rights, can make SOC services less accessible for organizations struggling to meet compliance standards, slowing down market growth.
Indonesia SOC as a Service Market Future Outlook
Over the next several years, the Indonesia SOC as a Service market is expected to expand, driven by the increasing digital transformation in various sectors, from banking to manufacturing. Continuous advancements in AI and machine learning within SOC solutions are projected to enhance the capabilities of threat detection and incident response, making them more efficient and adaptive to evolving cyber threats. Additionally, increased government support and collaboration with international cybersecurity firms are anticipated to bolster market growth.
Market Opportunities
- Expansion into SMEs: Indonesias SME sector, comprising 64 million businesses, has witnessed a significant shift toward digitalization, with over 25 million SMEs online in 2024, as per data from the Ministry of Cooperatives and SMEs Link. With rising cybersecurity threats, SOC as a Service providers have an opportunity to target these SMEs by offering scalable, cost-effective solutions that cater to smaller budgets. The expanding digital footprint of SMEs indicates a promising market for tailored SOC solutions that address security needs without excessive costs.
- Advancements in AI-Driven SOC Solutions: The application of AI in SOC services is gaining momentum, with the government investing approximately $15 million in AI-based cybersecurity solutions in 2024, according to the Ministry of Research and Technology Link. AI-powered SOCs enable faster threat detection and response, making SOC services more effective for diverse industries. SOC providers incorporating AI-driven solutions can offer enhanced value to Indonesian businesses, especially those in finance and healthcare, where data security is critical.
Scope of the Report
|
Managed Detection and Response Security Monitoring Incident Response Threat Intelligence Compliance Management |
|
|
By Deployment Type |
Cloud On-Premise |
|
By Organization Size |
Large Enterprises Small and Medium Enterprises (SMEs) |
|
By Distribution Channel |
BFSI Healthcare Retail IT & Telecommunications Government |
|
By Region |
North East West South |
Products
Key Target Audience
Large-scale Enterprises in Financial Services
Small and Medium-sized Enterprises (SMEs)
Cloud Solution Providers
Government and Regulatory Bodies (e.g., Kominfo)
Telecommunications Industry Leaders
E-commerce and Retail Firms
Healthcare Providers and Hospitals
Investor and Venture Capitalist Firms
Companies
Major Players in the Indonesia SOC as a Service Market
IBM Corporation
Cisco Systems, Inc.
Fortinet, Inc.
Trend Micro Inc.
AT&T Cybersecurity
RSA Security LLC
Secureworks, Inc.
Palo Alto Networks, Inc.
Darktrace Limited
CrowdStrike Holdings, Inc.
FireEye, Inc.
Symantec Corporation
Check Point Software Technologies Ltd.
Splunk Inc.
Rapid7, Inc.
Table of Contents
1. Indonesia SOC as a Service Market Overview
1.1 Definition and Scope
1.2 Market Taxonomy
1.3 Market Penetration Rate
1.4 Market Segmentation Overview
2. Indonesia SOC as a Service Market Size (In USD Mn)
2.1 Historical Market Size
2.2 Year-On-Year Growth Analysis
2.3 Key Market Developments and Milestones
3. Indonesia SOC as a Service Market Analysis
3.1 Growth Drivers
3.1.1 Increasing Cybersecurity Threats
3.1.2 Rapid Digital Transformation
3.1.3 Government Initiatives for Cybersecurity
3.1.4 Rising Adoption of Cloud-based Solutions
3.2 Market Challenges
3.2.1 High Operational Costs
3.2.2 Data Privacy Concerns
3.2.3 Shortage of Skilled Cybersecurity Professionals
3.3 Opportunities
3.3.1 Expansion into SMEs
3.3.2 Advancements in AI-Driven SOC Solutions
3.3.3 Integration with Incident Response Services
3.4 Trends
3.4.1 Adoption of Automation in SOC Operations
3.4.2 Integration with Threat Intelligence Platforms
3.4.3 Remote SOC Deployment Models
3.5 Government Regulation
3.5.1 Cybersecurity Law Compliance
3.5.2 Data Protection Regulations
3.5.3 Government Cybersecurity Frameworks
3.6 SWOT Analysis
3.7 Stakeholder Ecosystem
3.8 Porters Five Forces Analysis
3.9 Competition Ecosystem
4. Indonesia SOC as a Service Market Segmentation
4.1 By Service Type (In Value %)
4.1.1 Managed Detection and Response
4.1.2 Security Monitoring
4.1.3 Incident Response
4.1.4 Threat Intelligence
4.1.5 Compliance Management
4.2 By Deployment Type (In Value %)
4.2.1 Cloud
4.2.2 On-Premise
4.3 By Organization Size (In Value %)
4.3.1 Large Enterprises
4.3.2 Small and Medium Enterprises (SMEs)
4.4 By End-User Industry (In Value %)
4.4.1 BFSI
4.4.2 Healthcare
4.4.3 Retail
4.4.4 IT & Telecommunications
4.4.5 Government
4.5 By Region (In Value %)
4.5.1 North
4.5.2 East
4.5.3 West
4.5.4 South
5. Indonesia SOC as a Service Market Competitive Analysis
5.1 Detailed Profiles of Major Companies
5.1.1 IBM Corporation
5.1.2 Cisco Systems, Inc.
5.1.3 Palo Alto Networks, Inc.
5.1.4 Fortinet, Inc.
5.1.5 Trend Micro Inc.
5.1.6 Check Point Software Technologies Ltd.
5.1.7 AT&T Cybersecurity
5.1.8 RSA Security LLC
5.1.9 Secureworks, Inc.
5.1.10 Splunk Inc.
5.1.11 FireEye, Inc.
5.1.12 CrowdStrike Holdings, Inc.
5.1.13 Symantec Corporation
5.1.14 Darktrace Limited
5.1.15 Rapid7, Inc.
5.2 Cross Comparison Parameters (Market Share, Revenue, Regional Presence, Product Portfolio, Customer Base, Partnerships, Certifications, Threat Detection Speed)
5.3 Market Share Analysis
5.4 Strategic Initiatives
5.5 Mergers and Acquisitions
5.6 Investment Analysis
5.7 Venture Capital Funding
5.8 Government Contracts and Tenders
5.9 Private Equity Investments
6. Indonesia SOC as a Service Market Regulatory Framework
6.1 Cybersecurity Standards and Guidelines
6.2 Compliance Requirements and Certifications
6.3 Data Sovereignty and Privacy Regulations
7. Indonesia SOC as a Service Future Market Size (In USD Mn)
7.1 Future Market Size Projections
7.2 Key Factors Driving Future Market Growth
8. Indonesia SOC as a Service Future Market Segmentation
8.1 By Service Type (In Value %)
8.2 By Deployment Type (In Value %)
8.3 By Organization Size (In Value %)
8.4 By End-User Industry (In Value %)
8.5 By Region (In Value %)
9. Indonesia SOC as a Service Market Analysts Recommendations
9.1 Market Entry Strategies
9.2 Potential Strategic Partnerships
9.3 White Space Opportunity Analysis
9.4 Market Penetration Tactics
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
The initial phase involved mapping all relevant stakeholders within the Indonesia SOC as a Service market, encompassing service providers, regulatory bodies, and end-users. Key variables such as deployment models, service adoption rates, and cybersecurity needs were identified through extensive desk research.
Step 2: Market Analysis and Data Compilation
This phase consisted of collecting and analyzing historical data related to the SOC as a Service market in Indonesia, focusing on service deployment rates and regional adoption patterns. Market dynamics were assessed through qualitative and quantitative data from trusted proprietary databases and government publications.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses were refined through expert interviews and consultations with cybersecurity industry professionals, providing key insights into SOC service preferences, operational challenges, and deployment trends. These expert inputs were critical in validating market projections and competitive strategies.
Step 4: Research Synthesis and Final Output
The final phase synthesized insights and data gathered from various sources, including SOC service providers and key industry experts, ensuring a reliable and comprehensive analysis. This approach validated the robustness of the findings and provided a holistic view of the market's current and future trends.
Frequently Asked Questions
01. How big is the Indonesia SOC as a Service Market?
The Indonesia SOC as a Service market is valued at USD 23 billion, driven by rising cybersecurity concerns and increased digitalization across sectors.
02. What challenges does the Indonesia SOC as a Service Market face?
Challenges include the high costs of implementing SOC solutions, data privacy concerns, and a shortage of skilled cybersecurity professionals, which affect market penetration.
03. Who are the key players in the Indonesia SOC as a Service Market?
Key players include IBM Corporation, Cisco Systems, Fortinet, and Trend Micro, dominating due to their established presence, service portfolios, and strong client bases.
04. What drives growth in the Indonesia SOC as a Service Market?
Growth is primarily driven by the increase in cyber threats, government cybersecurity initiatives, and the rising adoption of cloud-based SOC services among businesses.
05. What future trends are expected in the Indonesia SOC as a Service Market?
Trends include the integration of AI for predictive threat detection, automation in SOC operations, and increasing demand for managed SOC services among SMEs looking for cost-effective cybersecurity solutions.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















