
MEA Network Security Market Outlook to 2030
Region:Global
Author(s):Meenakshi Bisht
Product Code:KROD7168
December 2024
98
About the Report
MEA Network Security Market Overview
- The Middle East and Africa (MEA) network security market is valued at USD 1.73 billion, based on a five-year historical analysis. This growth is driven by the increasing frequency and complexity of cyber threats, compelling organizations to invest in robust security solutions. The proliferation of digital transformation initiatives and the adoption of cloud services have further heightened the demand for advanced network security measures.
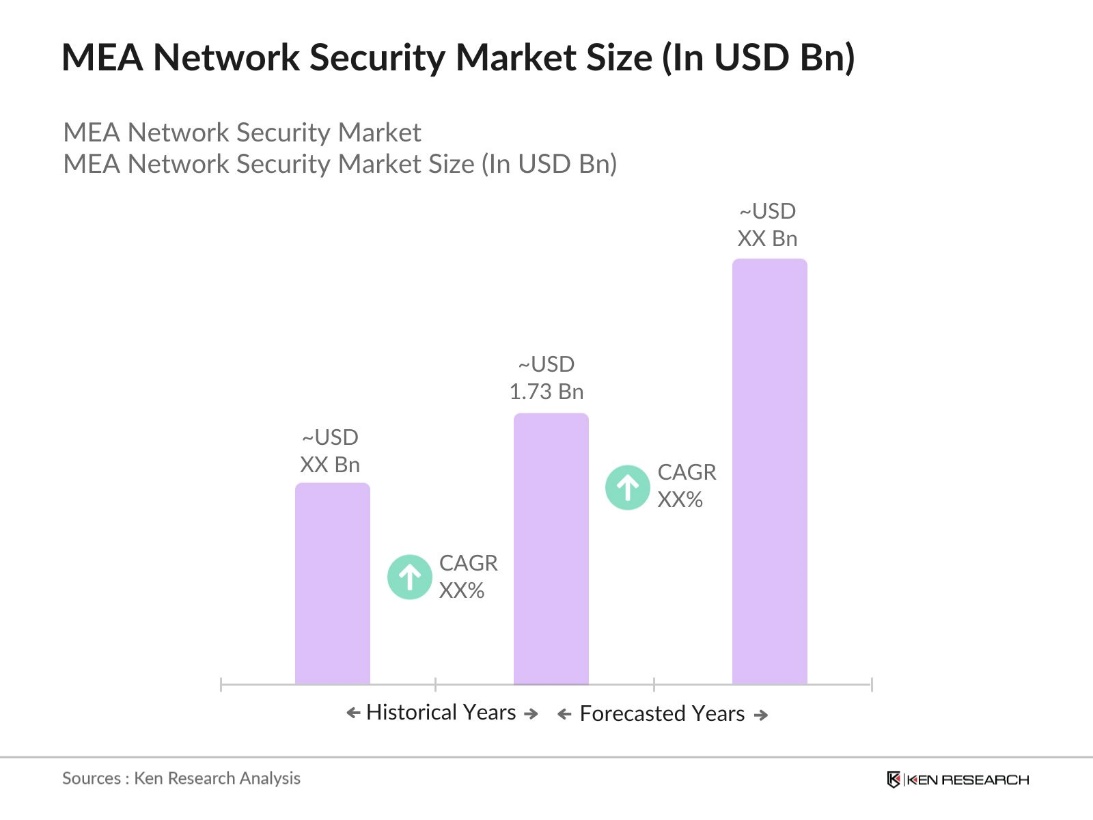
- Countries such as the United Arab Emirates (UAE), Saudi Arabia, and South Africa dominate the MEA network security market. Their dominance is attributed to substantial investments in digital infrastructure, proactive government policies promoting cybersecurity, and a high concentration of enterprises requiring sophisticated security solutions. These nations have established themselves as regional hubs for technology and innovation, thereby attracting significant market activity.
- MEA countries are rolling out national cybersecurity strategies to coordinate public and private sector defense initiatives. As of 2023, over 12 African nations have adopted national strategies, with investments in infrastructure and talent development. These strategies drive demand for security technologies, making cybersecurity an essential component of national digital policies.
MEA Network Security Market Segmentation
By Component: The market is segmented by component into solutions and services. Within this segmentation, solutions hold a dominant market share due to their critical role in safeguarding organizational networks against evolving cyber threats. Organizations prioritize implementing robust security solutions such as firewalls, intrusion detection systems (IDS), and unified threat management (UTM) systems to protect their digital assets.
By Deployment Mode: The market is segmented by deployment mode into on-premises and cloud-based solutions. Cloud-based deployment is gaining significant traction, driven by the flexibility, scalability, and cost-effectiveness it offers. Organizations are increasingly adopting cloud-based security solutions to accommodate remote work environments and to streamline security management across distributed networks.
MEA Network Security Market Competitive Landscape
The MEA network security market is characterized by the presence of both global and regional players, contributing to a competitive landscape. Key companies are focusing on strategic partnerships, product innovations, and regional expansions to strengthen their market positions.
MEA Network Security Industry Analysis
Growth Drivers
- Increasing Cyber Threats: The Middle East and Africa (MEA) region has experienced an upsurge in cyberattacks, with reported cases rising significantly in 2023. The highest average number of cyberattacks per week per organization in the second quarter of 2023, reflecting a 23% increase compared to the previous year. Higher digital connectivity exposes vulnerabilities across critical infrastructures, intensifying the demand for network security measures.
- Digital Transformation Initiatives: MEA nations have accelerated digital transformation initiatives, including increased investment in cloud computing and digital financial services. The World Bank reports that as of December 2022, there were 22 active projects and three pipeline projects focused on GovTech solutions, with total commitments amounting to approximately $6.9 billion, of which $2.2 billion was specifically allocated to GovTech solutions. This digital shift has driven cybersecurity investment to safeguard critical infrastructure.
- Regulatory Compliance Requirements: Regulatory requirements across MEA are enforcing stronger cybersecurity standards. For instance, the UAEs National Cybersecurity Strategy mandates data protection protocols, and Saudi Arabia's SAMA Cybersecurity Framework targets financial institutions. This regulatory shift is driving demand for network security solutions as organizations adapt to meet these standards and integrate robust cybersecurity measures into their digital infrastructures.
Market Challenges
- High Implementation Costs: Implementing comprehensive network security solutions involves substantial costs, which can be particularly burdensome for smaller enterprises. For many organizations with limited budgets, the high expenses associated with cybersecurity make it difficult to adopt robust protections. This financial barrier limits the reach of network security providers and presents challenges to achieving widespread cybersecurity across the region.
- Shortage of Skilled Cybersecurity Professionals: The MEA region faces a significant shortage of cybersecurity professionals, which hampers effective security implementation across sectors. Limited training infrastructure and talent retention challenges contribute to this skills gap, making it difficult for the industry to meet the growing cybersecurity demands driven by digital transformation in the region.
MEA Network Security Market Future Outlook
Over the next five years, the MEA network security market is expected to experience significant growth, driven by continuous government support, advancements in security technologies, and increasing awareness of cybersecurity threats among organizations. The adoption of artificial intelligence and machine learning in security solutions is anticipated to enhance threat detection and response capabilities. Additionally, the expansion of cloud services and the Internet of Things (IoT) will create new opportunities and challenges, necessitating advanced security measures.
Market Opportunities
- Adoption of Cloud-Based Security Solutions: In the MEA region, cloud-based security solutions are gaining traction as more organizations migrate data and operations to the cloud. This shift opens up opportunities for scalable, adaptable security measures, allowing businesses to leverage virtualized platforms that align with the demands of cloud environments. The trend underscores a market transition toward cloud-native security solutions that can provide flexible, efficient protection across digital infrastructures.
- Integration of AI and Machine Learning: The integration of AI and machine learning in network security is creating significant opportunities in MEA, with these technologies enhancing threat detection and predictive analytics capabilities. AI-driven security tools enable more proactive, adaptive defenses, making network security management more efficient. As businesses seek advanced solutions to address evolving threats, the use of AI and machine learning supports a growing demand for innovative, intelligent cybersecurity strategies.
Scope of the Report
|
Component |
Solutions (Firewall, IDS/IPS, DLP, UTM, NAC, Secure Web Gateways, Others) Services (Professional Services - Consulting, Implementation, Training & Education, Support & Maintenance; Managed Services) |
|
Deployment Mode |
On-Premises Cloud-Based |
|
Organization Size |
Small and Medium Enterprises (SMEs) Large Enterprises |
|
Industry Vertical |
BFSI Government & Defense Healthcare IT & Telecommunications Retail Manufacturing Energy & Utilities Others |
|
Region |
United Arab Emirates (UAE) Saudi Arabia South Africa Rest of Middle East and Africa |
Products
Key Target Audience
Network Security Solution Providers
Managed Security Service Providers (MSSPs)
Telecommunications Companies
Energy and Utility Companies
Government and Regulatory Bodies (e.g., National Cybersecurity Authorities)
Investors and Venture Capitalist Firms
Banks and Financial Institutions
Companies
Players Mentioned in the Report
Cisco Systems, Inc.
Check Point Software Technologies Ltd.
Fortinet, Inc.
Palo Alto Networks, Inc.
IBM Corporation
Juniper Networks, Inc.
Sophos Group plc
Trend Micro Incorporated
McAfee, LLC
Kaspersky Lab
Table of Contents
1. MEA Network Security Market Overview
1.1. Definition and Scope
1.2. Market Taxonomy
1.3. Market Growth Rate
1.4. Market Segmentation Overview
2. MEA Network Security Market Size (In USD Mn)
2.1. Historical Market Size
2.2. Year-On-Year Growth Analysis
2.3. Key Market Developments and Milestones
3. MEA Network Security Market Analysis
3.1. Growth Drivers
3.1.1. Increasing Cyber Threats
3.1.2. Digital Transformation Initiatives
3.1.3. Regulatory Compliance Requirements
3.1.4. Proliferation of IoT Devices
3.2. Market Challenges
3.2.1. High Implementation Costs
3.2.2. Shortage of Skilled Cybersecurity Professionals
3.2.3. Complexity of Network Infrastructures
3.3. Opportunities
3.3.1. Adoption of Cloud-Based Security Solutions
3.3.2. Integration of AI and Machine Learning
3.3.3. Expansion into Emerging Markets
3.4. Trends
3.4.1. Zero Trust Security Models
3.4.2. Managed Security Services Growth
3.4.3. Emphasis on Endpoint Security
3.5. Government Regulations
3.5.1. Data Protection Laws
3.5.2. Cybersecurity Frameworks
3.5.3. National Cybersecurity Strategies
3.5.4. Public-Private Partnerships
3.6. SWOT Analysis
3.7. Stakeholder Ecosystem
3.8. Porters Five Forces Analysis
3.9. Competitive Landscape
4. MEA Network Security Market Segmentation
4.1. By Component (In Value %)
4.1.1. Solutions
4.1.1.1. Firewall
4.1.1.2. Intrusion Detection Systems (IDS)/Intrusion Prevention Systems (IPS)
4.1.1.3. Data Loss Prevention (DLP)
4.1.1.4. Unified Threat Management (UTM)
4.1.1.5. Network Access Control (NAC)
4.1.1.6. Secure Web Gateways
4.1.1.7. Others
4.1.2. Services
4.1.2.1. Professional Services
4.1.2.1.1. Consulting
4.1.2.1.2. Implementation
4.1.2.1.3. Training and Education
4.1.2.1.4. Support and Maintenance
4.1.2.2. Managed Services
4.2. By Deployment Mode (In Value %)
4.2.1. On-Premises
4.2.2. Cloud-Based
4.3. By Organization Size (In Value %)
4.3.1. Small and Medium Enterprises (SMEs)
4.3.2. Large Enterprises
4.4. By Industry Vertical (In Value %)
4.4.1. Banking, Financial Services, and Insurance (BFSI)
4.4.2. Government and Defense
4.4.3. Healthcare
4.4.4. IT and Telecommunications
4.4.5. Retail
4.4.6. Manufacturing
4.4.7. Energy and Utilities
4.4.8. Others
4.5. By Region (In Value %)
4.5.1. United Arab Emirates (UAE)
4.5.2. Saudi Arabia
4.5.3. South Africa
4.5.4. Rest of Middle East and Africa
5. MEA Network Security Market Competitive Analysis
5.1. Detailed Profiles of Major Companies
5.1.1. Cisco Systems, Inc.
5.1.2. Check Point Software Technologies Ltd.
5.1.3. Fortinet, Inc.
5.1.4. Palo Alto Networks, Inc.
5.1.5. IBM Corporation
5.1.6. Juniper Networks, Inc.
5.1.7. Sophos Group plc
5.1.8. Trend Micro Incorporated
5.1.9. McAfee, LLC
5.1.10. Kaspersky Lab
5.1.11. Huawei Technologies Co., Ltd.
5.1.12. F5 Networks, Inc.
5.1.13. Barracuda Networks, Inc.
5.1.14. SonicWall Inc.
5.1.15. WatchGuard Technologies, Inc.
5.2. Cross Comparison Parameters (Revenue, Market Share, Product Portfolio, Regional Presence, Strategic Initiatives, R&D Investment, Number of Employees, Year Established)
5.3. Market Share Analysis
5.4. Strategic Initiatives
5.5. Mergers and Acquisitions
5.6. Investment Analysis
5.6.1. Venture Capital Funding
5.6.2. Government Grants
5.6.3. Private Equity Investments
6. MEA Network Security Market Regulatory Framework
6.1. Data Protection and Privacy Laws
6.2. Cybersecurity Compliance Standards
6.3. Certification Processes
6.4. Industry-Specific Regulations
7. MEA Network Security Future Market Size (In USD Mn)
7.1. Future Market Size Projections
7.2. Key Factors Driving Future Market Growth
8. MEA Network Security Future Market Segmentation
8.1. By Component (In Value %)
8.2. By Deployment Mode (In Value %)
8.3. By Organization Size (In Value %)
8.4. By Industry Vertical (In Value %)
8.5. By Region (In Value %)
9. MEA Network Security Market Analysts Recommendations
9.1. Total Addressable Market (TAM), Serviceable Available Market (SAM), Serviceable Obtainable Market (SOM) Analysis
9.2. Customer Cohort Analysis
9.3. Marketing and Channel Strategy
9.4. Opportunity Assessment and White Space Analysis
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
The initial phase involves constructing an ecosystem map encompassing all major stakeholders within the MEA Network Security Market. This step is underpinned by extensive desk research, utilizing a combination of secondary and proprietary databases to gather comprehensive industry-level information. The primary objective is to identify and define the critical variables that influence market dynamics.
Step 2: Market Analysis and Construction
In this phase, we compile and analyze historical data pertaining to the MEA Network Security Market. This includes assessing market penetration, the ratio of marketplaces to service providers, and the resultant revenue generation. Furthermore, an evaluation of service quality statistics is conducted to ensure the reliability and accuracy of the revenue estimates.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses are developed and subsequently validated through computer-assisted telephone interviews (CATIs) with industry experts representing a diverse array of companies. These consultations provide valuable operational and financial insights directly from industry practitioners, which are instrumental in refining and corroborating the market data.
Step 4: Research Synthesis and Final Output
The final phase involves direct engagement with multiple network security solution providers to acquire detailed insights into product segments, sales performance, consumer preferences, and other pertinent factors. This interaction serves to verify and complement the statistics derived from the bottom-up approach, thereby ensuring a comprehensive, accurate, and validated analysis of the MEA Network Security Market.
Frequently Asked Questions
01. How big is the MEA Network Security Market?
The MEA network security market is valued at USD 1.73 billion, based on a five-year historical analysis. Additionally, there is a need for continuous adaptation to evolving cyber threats, which places strain on organizations resources.
02. What are the challenges in the MEA Network Security Market?
The MEA network security market faces challenges such as a shortage of skilled cybersecurity professionals, high initial implementation costs, and the complexity of integrating advanced security solutions into diverse network infrastructures.
03. Who are the major players in the MEA Network Security Market?
Key players in the MEA network security market include Cisco Systems, Inc., Check Point Software Technologies Ltd., Fortinet, Inc., Palo Alto Networks, Inc., and IBM Corporation. These companies dominate due to their extensive product portfolios, strong brand presence, and strategic partnerships within the region.
04. What are the growth drivers of the MEA Network Security Market?
The MEA network security market is driven by increasing cyber threats, digital transformation across industries, regulatory compliance requirements, and the proliferation of IoT devices. Organizations across sectors are prioritizing network security to protect their digital assets and comply with government-mandated cybersecurity standards.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















