
U.S. Security Market Outlook 2030
Region:North America
Author(s):Shivani Mehra
Product Code:KROD11464
November 2024
99
About the Report
U.S. Security Market Overview
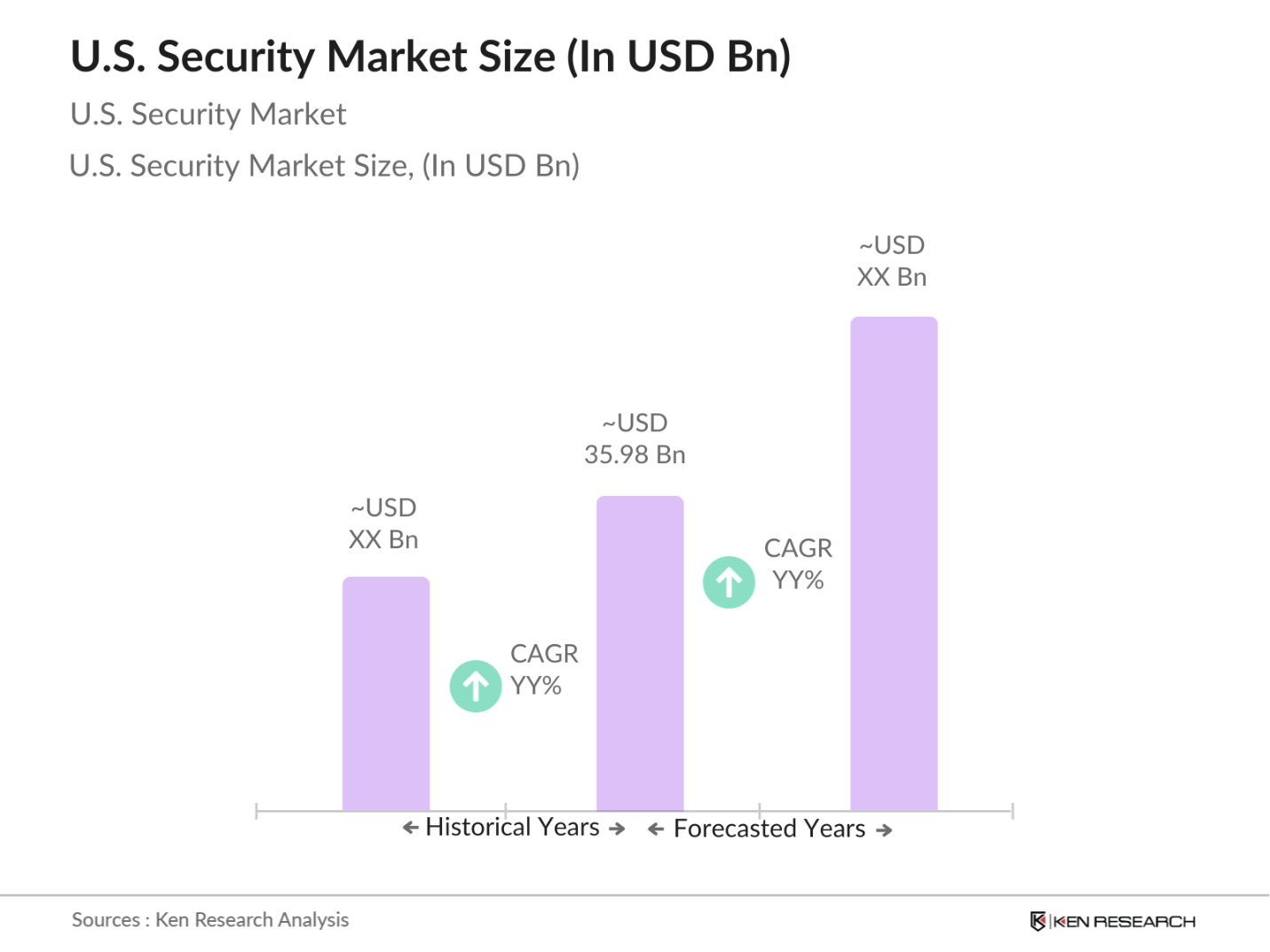
- The U.S. security market is valued at approximately USD 35.98 billion, reflecting the significant investments made in cybersecurity and physical security solutions. This market growth is primarily driven by the increasing threats posed by cybercriminals and the rise in regulatory requirements demanding robust security measures across various industries. As organizations prioritize safeguarding their digital assets and infrastructure, the demand for advanced security technologies continues to surge.
- The dominant regions in the U.S. security market include major metropolitan areas like New York, San Francisco, and Washington D.C. These cities are at the forefront due to their dense population, high concentration of businesses, and governmental agencies that require sophisticated security solutions. Moreover, the presence of leading technology firms and security providers in these regions further cements their dominance in the market.
- U.S. government initiatives to establish cybersecurity frameworks play a crucial role in shaping the security landscape. The National Cybersecurity Strategy emphasizes the adoption of the NIST Cybersecurity Framework, which provides guidelines for managing cybersecurity risks. In 2022, many organizations reported aligning their security practices with these frameworks, underscoring their significance in enhancing cybersecurity resilience. The governments commitment to improving cybersecurity posture through standardized frameworks reinforces the importance of regulatory compliance, fostering a more secure environment for businesses and consumers alike.
U.S. Security Market Segmentation
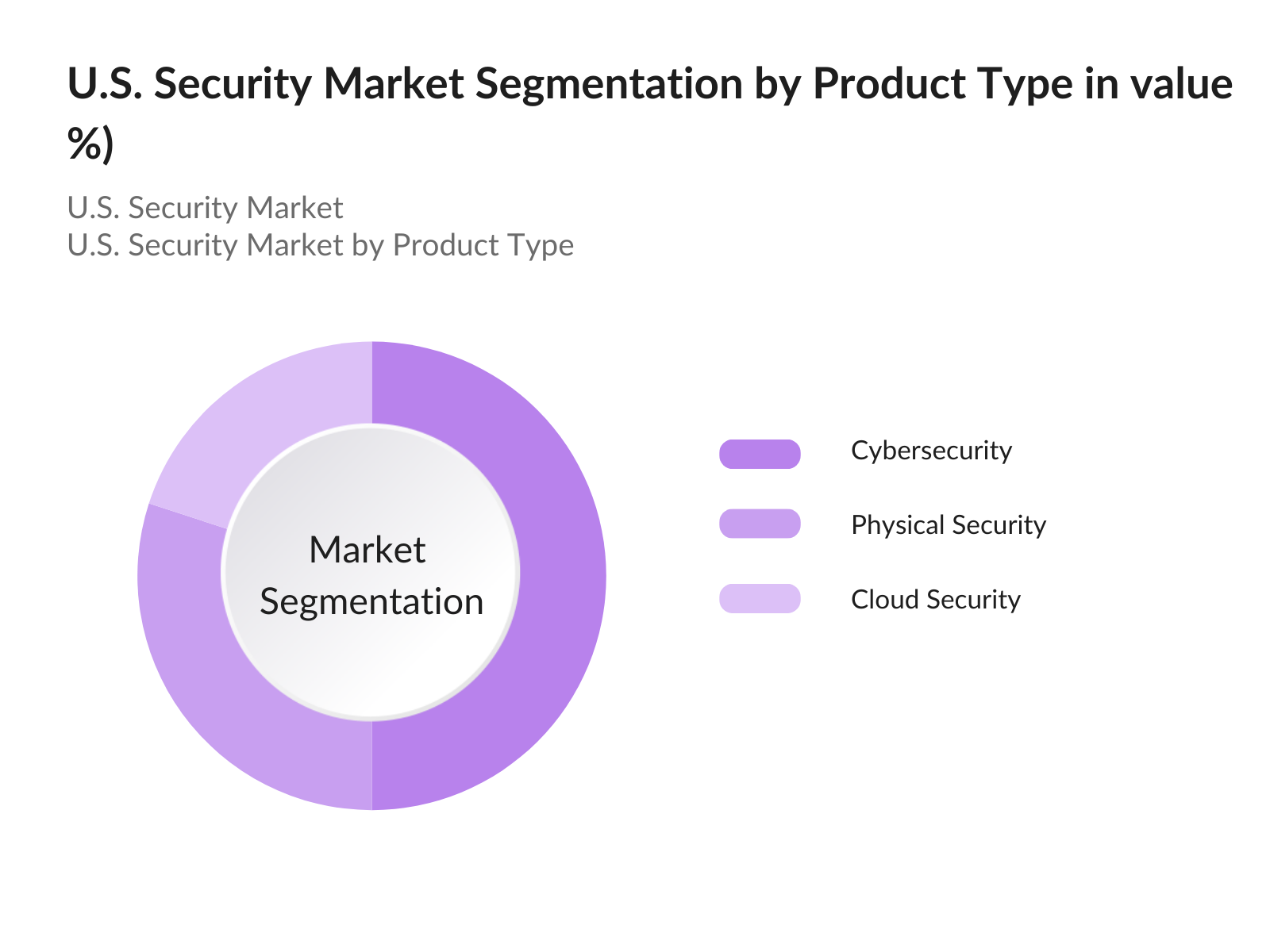
- By Product Type: The U.S. security market is segmented by product type into cybersecurity, physical security, and cloud security. Among these segments, cybersecurity holds a dominant market share due to the escalating frequency of cyberattacks and data breaches affecting organizations across various sectors. Businesses are increasingly adopting comprehensive cybersecurity frameworks, investing in solutions such as firewalls, intrusion detection systems, and endpoint protection. The necessity to protect sensitive data and maintain compliance with regulatory standards drives the growth of this segment, leading to significant advancements in cybersecurity technologies and a robust market presence.
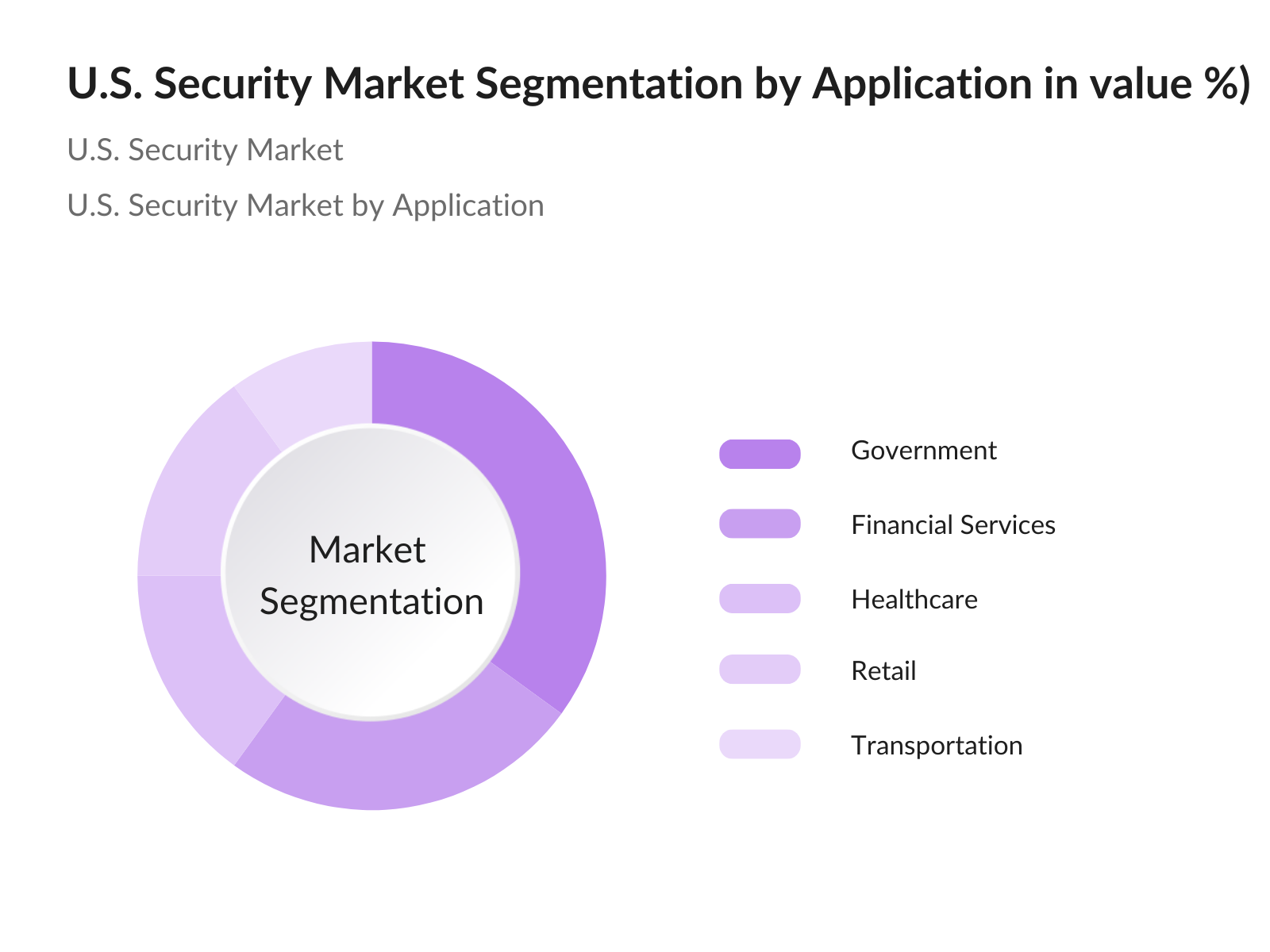
- By Application: The U.S. security market is also segmented by application into government, financial services, healthcare, retail, and transportation. The government segment is particularly prominent, primarily due to the necessity for national security and the protection of critical infrastructure. Government agencies invest heavily in security solutions to combat potential threats, enhance surveillance capabilities, and ensure public safety. This continuous investment in advanced security technologies fosters a strong growth trajectory for the government application segment, solidifying its dominant position in the overall market.
U.S. Security Market Competitive Landscape
The U.S. security market is characterized by a competitive landscape dominated by several key players. Companies such as Cisco Systems, IBM Corporation, Palo Alto Networks, Fortinet, and ADT Inc. are recognized for their robust security solutions and innovative technologies. The presence of these major players highlights the competitive dynamics of the market, where constant innovation and strategic partnerships play a critical role in maintaining market leadership.
|
Company Name |
Establishment Year |
Headquarters |
Product Range |
Market Focus |
Revenue |
|
Cisco Systems |
1984 |
San Jose, CA |
- |
- |
- |
|
IBM Corporation |
1911 |
Armonk, NY |
- |
- |
- |
|
Palo Alto Networks |
2005 |
Santa Clara, CA |
- |
- |
- |
|
Fortinet |
2000 |
Sunnyvale, CA |
- |
- |
- |
|
ADT Inc. |
1874 |
Boca Raton, FL |
- |
- |
- |
U.S. Security Market Analysis
Market Growth Drivers
- Increased Cyber Threats: The U.S. has witnessed a significant surge in cyber threats, with the FBI's Internet Crime Complaint Center reporting over 800,000 cybercrime complaints in 2022, resulting in losses exceeding $6.9 billion. The escalation of ransomware attacks, targeting critical infrastructure, has intensified the need for robust security solutions. Notably, the 2024 Cybersecurity Strategy emphasizes a collective defense approach to mitigate risks.
- Regulatory Compliance Requirements: Regulatory compliance continues to drive the U.S. security market, as organizations strive to meet standards set by frameworks like the GDPR and HIPAA. In 2022, many companies reported increased compliance costs due to evolving regulations, emphasizing the necessity for effective security measures. The introduction of stricter data protection laws and compliance mandates has led to heightened investments in security solutions.
- Technological Advancements: The U.S. security market is significantly influenced by rapid technological advancements, particularly in AI and machine learning. In 2023, a notable number of security professionals utilized AI-driven solutions for threat detection and response, reflecting a shift towards more sophisticated security measures. The integration of machine learning algorithms enhances the ability to identify and mitigate threats in real-time. Additionally, advancements in encryption technologies are expected to bolster data protection strategies, with global investment in encryption projected to be substantial by 2025.
Market Challenges:
- High Implementation Costs: The high implementation costs associated with security solutions pose significant challenges for organizations, particularly for small to medium-sized enterprises (SMEs). A 2022 study indicated that SMEs spend an average of $7,000 annually on cybersecurity measures, which can strain their budgets. The cost of advanced security technologies, such as next-generation firewalls and intrusion detection systems, further exacerbates this challenge. Additionally, ongoing maintenance and updates contribute to the financial burden.
- Skill Shortages in Security Personnel: The U.S. faces a critical shortage of skilled security personnel, impacting the effectiveness of security measures. As of 2023, over 700,000 cybersecurity positions remained unfilled, highlighting the talent gap within the industry. This shortage poses challenges for organizations in adequately managing and responding to security incidents. The lack of qualified professionals not only increases operational risks but also strains existing personnel, leading to potential burnout.
U.S. Security Market Future Outlook
Over the next five years, the U.S. security market is expected to exhibit robust growth driven by increasing investments in advanced security solutions and the continuous evolution of cybersecurity threats. The emphasis on compliance with stringent regulations and the growing need for integrated security systems will propel market expansion. Additionally, the rise of artificial intelligence and machine learning technologies will enhance the effectiveness of security measures, paving the way for innovative security solutions.
Market Opportunities:
- Proliferation of IoT Security Devices: The proliferation of Internet of Things (IoT) devices is reshaping the security landscape, creating new challenges and opportunities. As of 2022, over 15 billion IoT devices were connected globally, and this number is expected to exceed 25 billion by 2025. The integration of IoT devices in various sectors, including healthcare, transportation, and manufacturing, necessitates robust security measures to protect against vulnerabilities.
- Adoption of Zero Trust Security Models: The adoption of zero trust security models is gaining momentum as organizations recognize the need for enhanced security postures. In 2023, approximately of enterprises reported implementing zero trust principles as part of their cybersecurity strategies. This shift emphasizes the importance of verifying every access request, regardless of the user's location. The zero trust approach is particularly relevant in the context of remote work and cloud adoption, where traditional perimeter-based security measures are insufficient.
Scope of the Report
|
By Product Type |
Static Volumetric Displays Swept-Volume Displays Multi-Planar Volumetric Displays |
|
By Display Technology |
Digital Light Processing (DLP) Liquid Crystal Display (LCD) Light Emitting Diode (LED) |
|
By Application |
Medical Imaging AR/VR Advertising and Marketing Engineering and Design |
|
By End-User |
Healthcare, Automotive, Aerospace & Defense Entertainment and Media Education |
|
By Region |
North-East Midwest West Coast Southern States |
Products
Key Target Audience
Government and Regulatory Bodies (e.g., DHS, NSA)
Financial Institutions
Healthcare Organizations
Retail Corporations
Transportation Agencies
Manufacturing Industries
Telecommunications Providers
Investments and Venture Capitalist Firms
Companies
Players mentioned in the market
Cisco Systems
IBM Corporation
Palo Alto Networks
Fortinet
ADT Inc.
Check Point Software Technologies
McAfee Corp.
FireEye, Inc.
Nortek Security & Control
Brinks Home Security
Honeywell International
Tyco Integrated Security
Axis Communications
Verint Systems
Johnson Controls International
Table of Contents
1. U.S. Security Market Overview
1.1. Definition and Scope
1.2. Market Taxonomy
1.3. Market Growth Rate
1.4. Market Segmentation Overview
2. U.S. Security Market Size (In USD Bn)
2.1. Historical Market Size
2.2. Year-On-Year Growth Analysis
2.3. Key Market Developments and Milestones
3. U.S. Security Market Analysis
3.1. Growth Drivers
3.1.1. Increased Cyber Threats
3.1.2. Regulatory Compliance Requirements
3.1.3. Technological Advancements
3.1.4. Heightened Security Awareness
3.2. Market Challenges
3.2.1. High Implementation Costs
3.2.2. Integration Complexities
3.2.3. Skill Shortages in Security Personnel
3.3. Opportunities
3.3.1. Expansion of Cloud Security Solutions
3.3.2. Growth in Managed Security Services
3.3.3. Increasing Investment in Physical Security Systems
3.4. Trends
3.4.1. Shift Towards AI and Machine Learning in Security
3.4.2. Proliferation of IoT Security Devices
3.4.3. Adoption of Zero Trust Security Models
3.5. Government Regulation
3.5.1. Cybersecurity Frameworks
3.5.2. Data Protection Laws
3.5.3. Industry-Specific Compliance Mandates
3.6. SWOT Analysis
3.7. Stakeholder Ecosystem
3.8. Porters Five Forces
3.9. Competition Ecosystem
4. U.S. Security Market Segmentation
4.1. By Security Type (In Value %)
4.1.1. Cybersecurity
4.1.2. Physical Security
4.1.3. Cloud Security
4.2. By Application (In Value %)
4.2.1. Government
4.2.2. Financial Services
4.2.3. Healthcare
4.2.4. Retail
4.2.5. Transportation
4.3. By End-User (In Value %)
4.3.1. Small and Medium Enterprises
4.3.2. Large Enterprises
4.4. By Technology (In Value %)
4.4.1. Biometrics
4.4.2. Surveillance Systems
4.4.3. Access Control Systems
4.5. By Region (In Value %)
4.5.1. Northeast
4.5.2. Midwest
4.5.3. South
4.5.4. West
5. U.S. Security Market Competitive Analysis
5.1. Detailed Profiles of Major Companies
5.1.1. Cisco Systems, Inc.
5.1.2. IBM Corporation
5.1.3. Palo Alto Networks, Inc.
5.1.4. McAfee Corp.
5.1.5. Fortinet, Inc.
5.1.6. Check Point Software Technologies Ltd.
5.1.7. FireEye, Inc.
5.1.8. ADT Inc.
5.1.9. Axis Communications AB
5.1.10. Honeywell International Inc.
5.1.11. Johnson Controls International PLC
5.1.12. Nortek Security & Control
5.1.13. Brinks Home Security
5.1.14. Tyco Integrated Security
5.1.15. Verint Systems Inc.
5.2. Cross Comparison Parameters (No. of Employees, Headquarters, Inception Year, Revenue, Product Portfolio, Market Presence, Key Partnerships, Technological Innovations)
5.3. Market Share Analysis
5.4. Strategic Initiatives
5.5. Mergers and Acquisitions
5.6. Investment Analysis
5.7. Venture Capital Funding
5.8. Government Grants
5.9. Private Equity Investments
6. U.S. Security Market Regulatory Framework
6.1. Cybersecurity Standards
6.2. Compliance Requirements
6.3. Certification Processes
7. U.S. Security Market Future Market Size (In USD Bn)
7.1. Future Market Size Projections
7.2. Key Factors Driving Future Market Growth
8. U.S. Security Market Future Segmentation
8.1. By Security Type (In Value %)
8.2. By Application (In Value %)
8.3. By End-User (In Value %)
8.4. By Technology (In Value %)
8.5. By Region (In Value %)
9. U.S. Security Market Analysts Recommendations
9.1. TAM/SAM/SOM Analysis
9.2. Customer Cohort Analysis
9.3. Marketing Initiatives
9.4. White Space Opportunity Analysis
Research Methodology
Step 1: Identification of Key Variables
The initial phase involves constructing an ecosystem map encompassing all major stakeholders within the U.S. security market. This step is underpinned by extensive desk research, utilizing a combination of secondary and proprietary databases to gather comprehensive industry-level information. The primary objective is to identify and define the critical variables that influence market dynamics.
Step 2: Market Analysis and Construction
In this phase, we compile and analyze historical data pertaining to the U.S. security market. This includes assessing market penetration, the ratio of marketplaces to service providers, and the resultant revenue generation. Furthermore, an evaluation of service quality statistics will be conducted to ensure the reliability and accuracy of the revenue estimates.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses will be developed and subsequently validated through computer-assisted telephone interviews (CATIs) with industry experts representing a diverse array of companies. These consultations provide valuable operational and financial insights directly from industry practitioners, which will be instrumental in refining and corroborating the market data.
Step 4: Research Synthesis and Final Output
The final phase involves direct engagement with multiple security solution providers to acquire detailed insights into product segments, sales performance, consumer preferences, and other pertinent factors. This interaction will serve to verify and complement the statistics derived from the bottom-up approach, thereby ensuring a comprehensive, accurate, and validated analysis of the U.S. security market.
Frequently Asked Questions
01. How big is the U.S. Security Market?
The U.S. security market is valued at USD 35.98 billion, driven by increasing cyber threats and regulatory requirements demanding robust security measures across various industries.
02. What are the challenges in the U.S. Security Market?
Challenges include the high costs associated with implementing advanced security solutions, the complexities of integrating multiple security systems, and the persistent shortage of skilled security personnel.
03. Who are the major players in the U.S. Security Market?
Key players in the market include Cisco Systems, IBM Corporation, Palo Alto Networks, Fortinet, and ADT Inc., which dominate due to their extensive product offerings and established brand presence.
04. What are the growth drivers of the U.S. Security Market?
The market is propelled by factors such as the rising frequency of cyberattacks, increasing investments in advanced security technologies, and the need for compliance with stringent regulatory frameworks.
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















