
USA Identity and Access Management Market Outlook
Region:North America
Author(s):Shambhavi
Product Code:KROD4325
December 2024
85
About the Report
U.S. Identity and Access Management Market Overview
- The U.S. Identity and Access Management (IAM) market is valued at approximately USD 12.8 billion in 2023, primarily driven by the rise of digital transformation across sectors, coupled with heightened cybersecurity concerns. The increased adoption of IAM solutions can be attributed to growing regulatory requirements, especially in sectors such as finance and healthcare. Furthermore, the expanding use of cloud technologies and remote work have necessitated stronger identity controls to prevent unauthorized access, making IAM solutions essential for secure access management across digital environments.
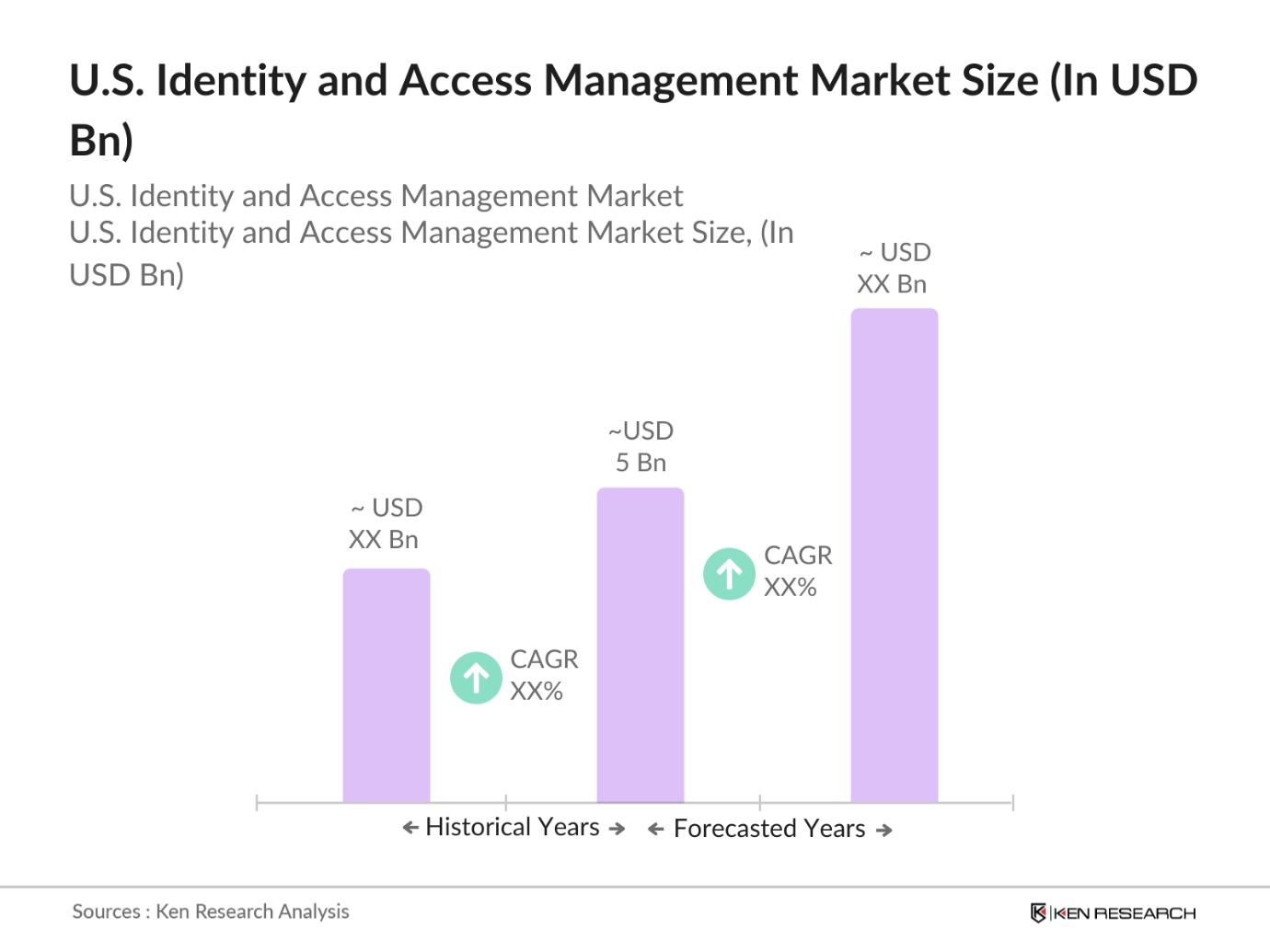
- The U.S. IAM market finds substantial traction in major technology-driven hubs, notably cities like San Francisco, New York, and Washington D.C. This concentration stems from the high presence of technology firms, financial institutions, and government bodies that prioritize robust cybersecurity measures. San Francisco, as a tech epicenter, leads the demand for IAM due to numerous high-tech companies needing complex security layers, while Washington D.C. demonstrates strong demand due to federal agencies and stringent regulatory frameworks governing data protection and privacy.
- Enacted to enforce strict cybersecurity standards across federal agencies, FISMA mandates the adoption of secure IAM solutions. Recent amendments in 2023 required increased reporting for IAM implementations, with federal agencies allocating an average of $10 million each to upgrade their IAM infrastructure, underscoring government commitment to tightening access management.
U.S. Identity and Access Management Market Segmentation
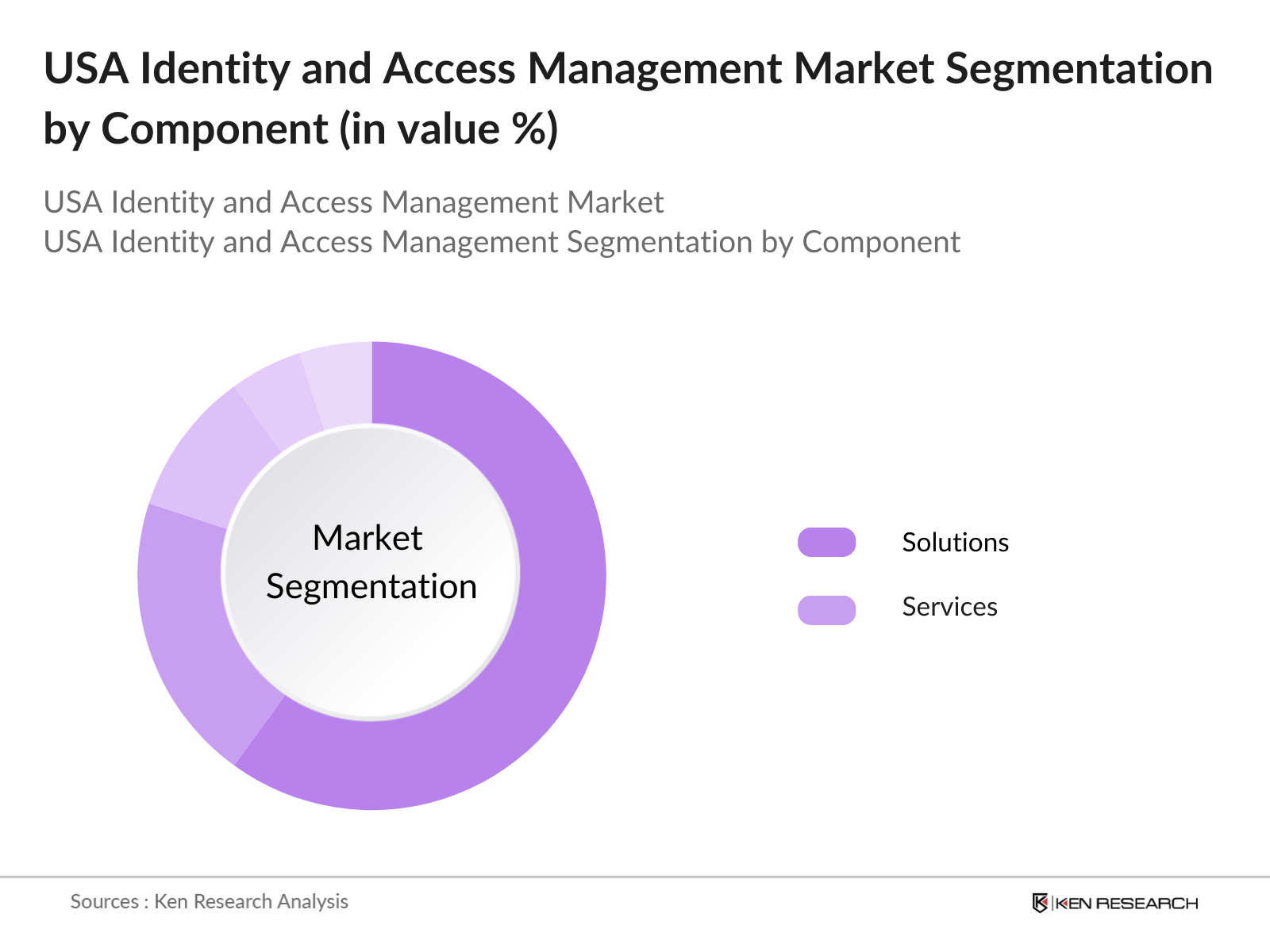
By Component: The U.S. IAM market is segmented by component into solutions and services. Within this segmentation, solutions hold a prominent market share due to the necessity for multifaceted IAM tools such as single sign-on (SSO), multi-factor authentication (MFA), and user provisioning. Companies across various sectors rely on these solutions to secure access across cloud and on-premise systems, ensuring compliance with stringent data security standards. SSO, in particular, has gained traction as it simplifies user access management while reducing administrative overheads, making it an indispensable tool in large enterprises.
By Deployment Mode: The IAM market is also segmented by deployment mode, comprising on-premise and cloud-based solutions. Cloud-based IAM solutions dominate this segment due to the flexibility and scalability they offer, which aligns with the increased adoption of cloud applications across industries. Businesses are progressively moving toward cloud environments to facilitate remote work and digital transformation initiatives, further driving the demand for cloud-based IAM. This shift toward cloud adoption is reinforced by the cost-efficiency and ease of integration that cloud IAM solutions offer, making them the preferred choice among U.S. enterprises.

U.S. Identity and Access Management Market Competitive Landscape
The U.S. IAM market is led by a mix of global and domestic players, focusing on comprehensive IAM solutions to address diverse security challenges. Key players have continued to invest in innovation and advanced IAM technologies to differentiate in this competitive market.
The competitive landscape reflects a consolidation where a few major players dominate, driven by advancements in IAM solutions and the integration of AI for enhanced identity verification.
U.S. Identity and Access Management Market Analysis
Growth Drivers
- Expansion of Cloud Services: The shift to cloud-based infrastructure in the U.S. is intensifying the demand for IAM solutions due to increased remote access needs. In 2023, U.S. companies invested nearly $380 billion in cloud services, with over 90% of enterprises relying on multi-cloud environments. This cloud adoption necessitates robust IAM for managing access across cloud platforms, with security agencies confirming that 62% of cloud data breaches are linked to inadequate IAM practices, stressing the importance of strengthened IAM solutions.
- Stringent Data Protection Regulations: With laws like the CCPA and GDPR compliance requirements impacting U.S. businesses, IAM has become a regulatory necessity. In 2023, Californias updated CCPA amendments increased the penalties for data breaches, with fines reaching up to $7,500 per individual violation, prompting companies to adopt IAM for better compliance. Additionally, GDPRs influence on U.S. multinationals has escalated IAM integration to safeguard against fines, which surpassed $1 billion globally in regulatory penalties due to non-compliance in 2023.
- Growing Remote Workforce: In 2023, approximately 58 million U.S. workers engaged in remote or hybrid work, underscoring the need for secure access management across distributed environments. The Department of Labor highlights that remote work policies are expected to stabilize, with enterprises investing in IAM systems to control secure access, prevent unauthorized entry, and protect corporate data from vulnerabilities heightened by decentralized access.
Challenges
- Integration with Legacy Systems: A significant challenge in the IAM market is the integration with legacy systems still prevalent in 54% of U.S. corporations, especially within banking and healthcare sectors. These outdated infrastructures complicate IAM implementation, requiring specialized solutions and raising costs by an estimated 25% for organizations reliant on outdated platforms. This legacy dependency also prolongs IAM deployment times, creating delays in achieving secure access management.
- Budget Constraints: Implementing advanced IAM solutions involves high initial investments, with cost-related obstacles impacting nearly 40% of small and mid-sized U.S. enterprises, which cite budgetary concerns as a primary barrier. Government funding for cybersecurity was recorded at $11 billion in 2023; however, for smaller entities, adopting advanced IAM solutions without financial subsidies remains challenging, especially in non-regulated industries.
U.S. Identity and Access Management Market Future Outlook
The U.S. IAM market is expected to experience sustained growth over the coming years, fueled by increasing digital adoption and stringent regulatory compliance demands. As more companies transition to cloud-based infrastructures, the role of IAM solutions in ensuring secure access management across dispersed environments will be pivotal. Emerging technologies such as AI and machine learning are anticipated to play a central role in automating and enhancing IAM functionalities, particularly in fraud detection and behavioral analytics.
Opportunities
- Adoption of AI and Machine Learning: AI-driven IAM solutions enhance predictive threat analysis and real-time access decisions, improving security. As of 2023, AI integration in IAM saw an investment of $15 billion, supporting capabilities like automated threat detection and adaptive authentication. AI-driven IAM is projected to streamline identity verification, providing growth opportunities for solution providers in sectors like finance and healthcare that face high threat levels.
- Expansion into IoT Devices: The U.S. IoT market, valued at $212 billion in 2023, reflects increased demand for IAM solutions as IoT devices grow in industrial and healthcare settings. Managing secure access across IoT environments is critical, with 78 million active IoT devices in the U.S. requiring robust IAM solutions to protect against unauthorized access, creating lucrative opportunities for IAM providers.
Scope of the Report
|
Solution Type |
Single Sign-On (SSO) Multi-Factor Authentication (MFA) Identity Governance and Administration (IGA) Privileged Access Management (PAM) Directory Services |
|
Deployment Model |
Cloud-Based On-Premises Hybrid |
|
Organization Size |
Small and Medium Enterprises (SMEs) Large Enterprises |
|
Industry |
BFSI Healthcare IT and Telecom Retail Government |
|
Region |
North West South East |
Products
Key Target Audience
Large Enterprises
Small and Medium Enterprises (SMEs)
Government and Regulatory Bodies (e.g., National Institute of Standards and Technology)
Financial Institutions
Healthcare Providers
Cloud Service Providers
Telecommunication Companies
Investors and Venture Capitalist Firms
Companies
Major Players in the U.S. IAM Market
Okta, Inc.
Microsoft Corporation
IBM Corporation
Oracle Corporation
CyberArk Software
Ping Identity Corporation
SailPoint Technologies
ForgeRock Inc.
One Identity
Broadcom Inc.
Micro Focus
SecureAuth Corporation
HID Global
RSA Security LLC
Symantec Corporation
Table of Contents
U.S. Identity and Access Management Market Overview
1.1. Definition and Scope
1.2. Market Taxonomy
1.3. Market Growth Rate
1.4. Market Segmentation Overview
U.S. Identity and Access Management Market Size (In USD Bn)
2.1. Historical Market Size
2.2. Year-On-Year Growth Analysis
2.3. Key Market Developments and Milestones
U.S. Identity and Access Management Market Analysis
3.1. Growth Drivers [Adoption Rate, Cloud Integration, Cybersecurity Demand, Regulatory Compliance]
3.1.1. Increasing Cybersecurity Threats
3.1.2. Expansion of Cloud Services
3.1.3. Stringent Data Protection Regulations
3.1.4. Growing Remote Workforce
3.2. Market Challenges [Integration Complexity, High Implementation Costs, Skill Shortages]
3.2.1. Integration with Legacy Systems
3.2.2. Budget Constraints
3.2.3. Limited Skilled Professionals
3.3. Opportunities [Technological Advancements, AI Integration, IoT Expansion]
3.3.1. Adoption of AI and Machine Learning
3.3.2. Expansion into IoT Devices
3.3.3. Enhanced Mobile Security Solutions
3.4. Trends [Zero Trust Architecture, Biometrics, Multi-Factor Authentication]
3.4.1. Zero Trust Security Models
3.4.2. Increased Use of Biometric Authentication
3.4.3. Adoption of Multi-Factor Authentication
3.5. Government Regulation [FISMA, GDPR Compliance, CCPA]
3.5.1. Federal Information Security Management Act (FISMA)
3.5.2. General Data Protection Regulation (GDPR) Compliance
3.5.3. California Consumer Privacy Act (CCPA)
3.5.4. National Institute of Standards and Technology (NIST) Guidelines
3.6. SWOT Analysis
3.7. Stakeholder Ecosystem
3.8. Porters Five Forces
3.9. Competition Ecosystem
U.S. Identity and Access Management Market Segmentation
4.1. By Solution Type (In Value %)
4.1.1. Single Sign-On (SSO)
4.1.2. Multi-Factor Authentication (MFA)
4.1.3. Identity Governance and Administration (IGA)
4.1.4. Privileged Access Management (PAM)
4.1.5. Directory Services
4.2. By Deployment Model (In Value %)
4.2.1. Cloud-Based
4.2.2. On-Premises
4.2.3. Hybrid
4.3. By Organization Size (In Value %)
4.3.1. Small and Medium Enterprises (SMEs)
4.3.2. Large Enterprises
4.4. By Industry (In Value %)
4.4.1. BFSI
4.4.2. Healthcare
4.4.3. IT and Telecom
4.4.4. Retail
4.4.5. Government
4.5. By Region (In Value %)
4.5.1. North
4.5.2. West
4.5.3. South
4.5.4. East
U.S. Identity and Access Management Market Competitive Analysis
5.1. Detailed Profiles of Major Companies
5.1.1. Microsoft Corporation
5.1.2. IBM Corporation
5.1.3. Okta, Inc.
5.1.4. Ping Identity
5.1.5. Oracle Corporation
5.1.6. CyberArk Software Ltd.
5.1.7. SailPoint Technologies Holdings, Inc.
5.1.8. RSA Security LLC
5.1.9. ForgeRock, Inc.
5.1.10. OneLogin, Inc.
5.1.11. Centrify Corporation
5.1.12. Auth0, Inc.
5.1.13. Duo Security (Cisco)
5.1.14. Thales Group
5.1.15. Hitachi ID Systems
5.2. Cross Comparison Parameters [Number of Employees, Headquarters, Inception Year, Revenue, Product Portfolio, Market Share, R&D Investment, Geographic Presence]
5.3. Market Share Analysis
5.4. Strategic Initiatives
5.5. Mergers and Acquisitions
5.6. Investment Analysis
5.7. Venture Capital Funding
5.8. Government Grants
5.9. Private Equity Investments
U.S. Identity and Access Management Market Regulatory Framework
6.1. Data Protection Laws
6.2. Compliance Requirements
6.3. Certification Processes
U.S. Identity and Access Management Future Market Size (In USD Bn)
7.1. Future Market Size Projections
7.2. Key Factors Driving Future Market Growth
U.S. Identity and Access Management Future Market Segmentation
8.1. By Solution Type (In Value %)
8.1.1. Single Sign-On (SSO)
8.1.2. Multi-Factor Authentication (MFA)
8.1.3. Identity Governance and Administration (IGA)
8.1.4. Privileged Access Management (PAM)
8.1.5. Directory Services
8.2. By Deployment Model (In Value %)
8.2.1. Cloud-Based
8.2.2. On-Premises
8.2.3. Hybrid
8.3. By Organization Size (In Value %)
8.3.1. Small and Medium Enterprises (SMEs)
8.3.2. Large Enterprises
8.4. By Industry (In Value %)
8.4.1. BFSI
8.4.2. Healthcare
8.4.3. IT and Telecom
8.4.4. Retail
8.4.5. Government
8.5. By Region (In Value %)
8.5.1. Northeast
8.5.2. Midwest
8.5.3. South
8.5.4. West
U.S. Identity and Access Management Market Analysts Recommendations
9.1. TAM/SAM/SOM Analysis
9.2. Customer Cohort Analysis
9.3. Marketing Initiatives
9.4. White Space Opportunity Analysis
Disclaimer Contact UsResearch Methodology
Step 1: Identification of Key Variables
In this initial phase, an ecosystem map covering all major players in the U.S. IAM market is created. Extensive desk research using secondary databases enables the identification of critical variables impacting IAM market dynamics.
Step 2: Market Analysis and Construction
This phase involves analyzing historical data to assess market penetration and evaluate sector-wise adoption rates. The assessment includes a review of industry growth trends and service provider ratios.
Step 3: Hypothesis Validation and Expert Consultation
Developed hypotheses are validated through computer-assisted telephone interviews with industry professionals. These consultations yield insights directly from operational managers and sector specialists.
Step 4: Research Synthesis and Final Output
The synthesis phase includes direct engagement with IAM solution providers to verify and complement initial data findings, ensuring a comprehensive and validated analysis of the U.S. IAM market.
Frequently Asked Questions
01. How big is the U.S. Identity and Access Management Market?
The U.S. Identity and Access Management market is valued at USD 12.8 billion, driven by heightened cybersecurity requirements and the increasing adoption of cloud-based solutions across industries.
02. What are the primary challenges in the U.S. IAM Market?
Key challenges include high implementation costs and integration complexities with existing infrastructure, as well as the need for continuous updates to keep pace with emerging cyber threats.
03. Who are the major players in the U.S. IAM Market?
The IAM market is led by prominent players like Okta, Microsoft, IBM, and CyberArk, who dominate through advanced security solutions and a strong emphasis on cloud-based IAM offerings.
04. What drives growth in the U.S. IAM Market?
Growth is primarily driven by regulatory requirements for data protection, increased adoption of remote work, and advancements in IAM technology that enhance security protocols.
05. Which segment holds the largest market share in the U.S. IAM Market?
Why Buy From Us?

What makes us stand out is that our consultants follows Robust, Refine and Result (RRR) methodology. i.e. Robust for clear definitions, approaches and sanity checking, Refine for differentiating respondents facts and opinions and Result for presenting data with story

We have set a benchmark in the industry by offering our clients with syndicated and customized market research reports featuring coverage of entire market as well as meticulous research and analyst insights.

While we don't replace traditional research, we flip the method upside down. Our dual approach of Top Bottom & Bottom Top ensures quality deliverable by not just verifying company fundamentals but also looking at the sector and macroeconomic factors.

With one step in the future, our research team constantly tries to show you the bigger picture. We help with some of the tough questions you may encounter along the way: How is the industry positioned? Best marketing channel? KPI's of competitors? By aligning every element, we help maximize success.

Our report gives you instant access to the answers and sources that other companies might choose to hide. We elaborate each steps of research methodology we have used and showcase you the sample size to earn your trust.

If you need any support, we are here! We pride ourselves on universe strength, data quality, and quick, friendly, and professional service.















