Cybersecurity in Digital India: Strategic Roadmap for a ₹25,000 Cr Risk Mitigation Opportunity
This POV explores India’s cybersecurity maturity with data-driven insights and strategic steps to secure digital infrastructure nationwide.





















Built for Leaders Across
- CIOs, CISOs, and IT Security Leaders in Government, BFSI, and Healthcare
- Founders & CTOs of Indian startups building digital infrastructure or SaaS platforms
- Policymakers and Infrastructure Heads in Smart Cities, UIDAI, and Public Sector Digitization
- Risk Officers and Strategic Planners in Cybersecurity Consulting or Cloud Deployment Roles
Need a Vertical-Specific Cyber Audit? Schedule a 1:1 Consultation
Executive Summary: India’s Cybersecurity Readiness At A Crossroads
With India’s digital services expected to reach USD 1.2 trillion by 2026, the cost of cyber threats is estimated to exceed ₹25,000 crore in economic damage by 2028. Despite the scale, preparedness remains scattered:
- 1391457 cyber security incidents reported to CERT-In in 2022
- BFSI, Healthcare, and Government sectors saw the largest spikes in attack surfaces
- Public awareness remains below 35%, especially on Zero Trust and digital hygiene
- Small and medium enterprises (SMEs) are disproportionately vulnerable due to low budgets and lack of standard frameworks
The need for a holistic, multi-layered cyber defense strategy has never been more urgent
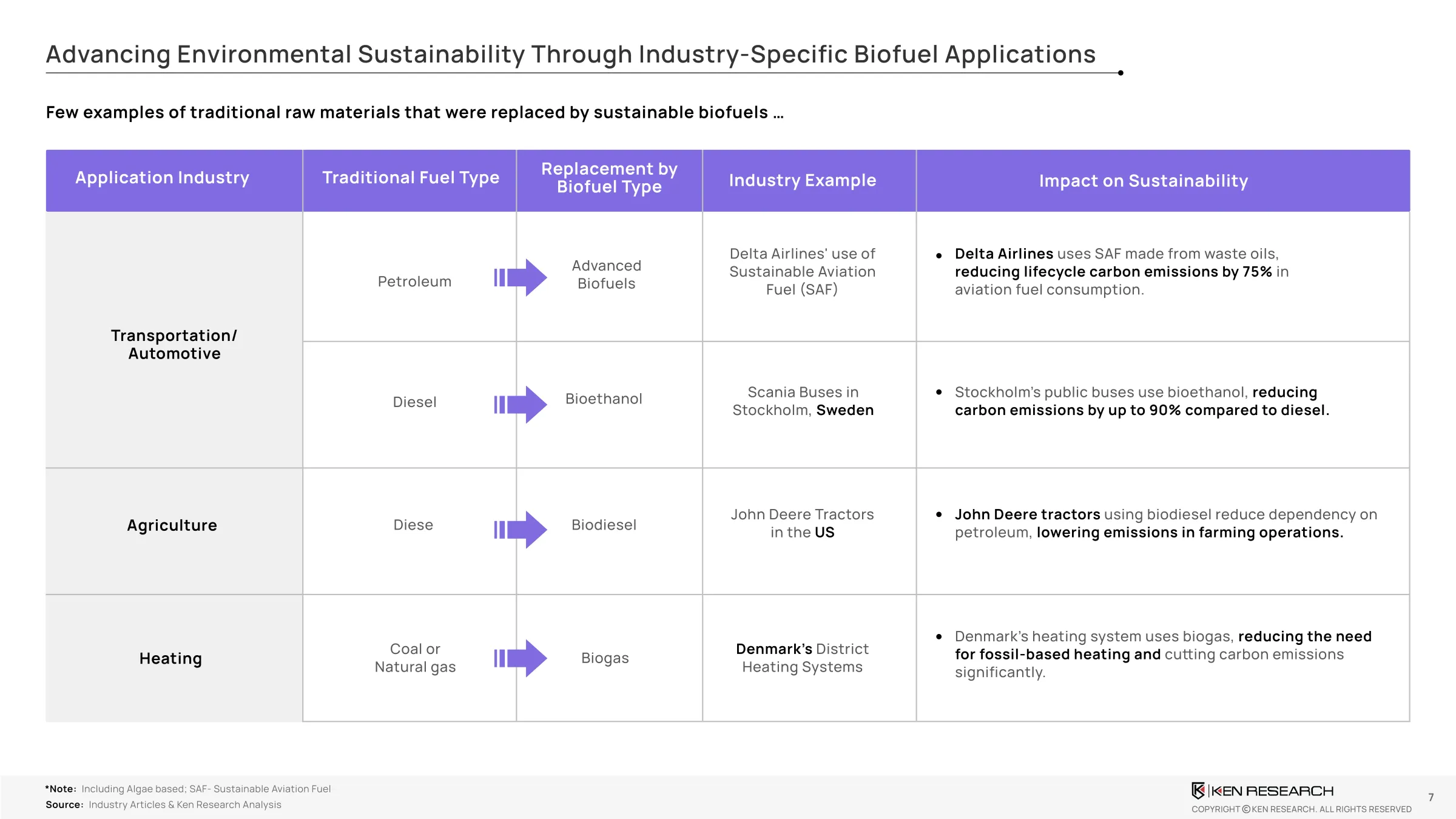
Download the Slide Deck to View India’s Sector-Wise Cybersecurity Benchmarks
Sectoral Cyber Risk Heatmap: Vulnerabilities and Priority Zones
India’s digitization isn’t evenly protected. Our cybersecurity risk heatmap identifies four sectors most at risk:
Government: Over 25% of critical infra attacks target identity, citizen databases, and land recordsHealthcare: Ransomware doubled YoY due to low maturity and siloed digital operationsBFSI: APIs and mobile banking apps contribute to over 60% of breachesSmart Cities & IoT: Unsecured endpoints and legacy devices make urban infra an easy target
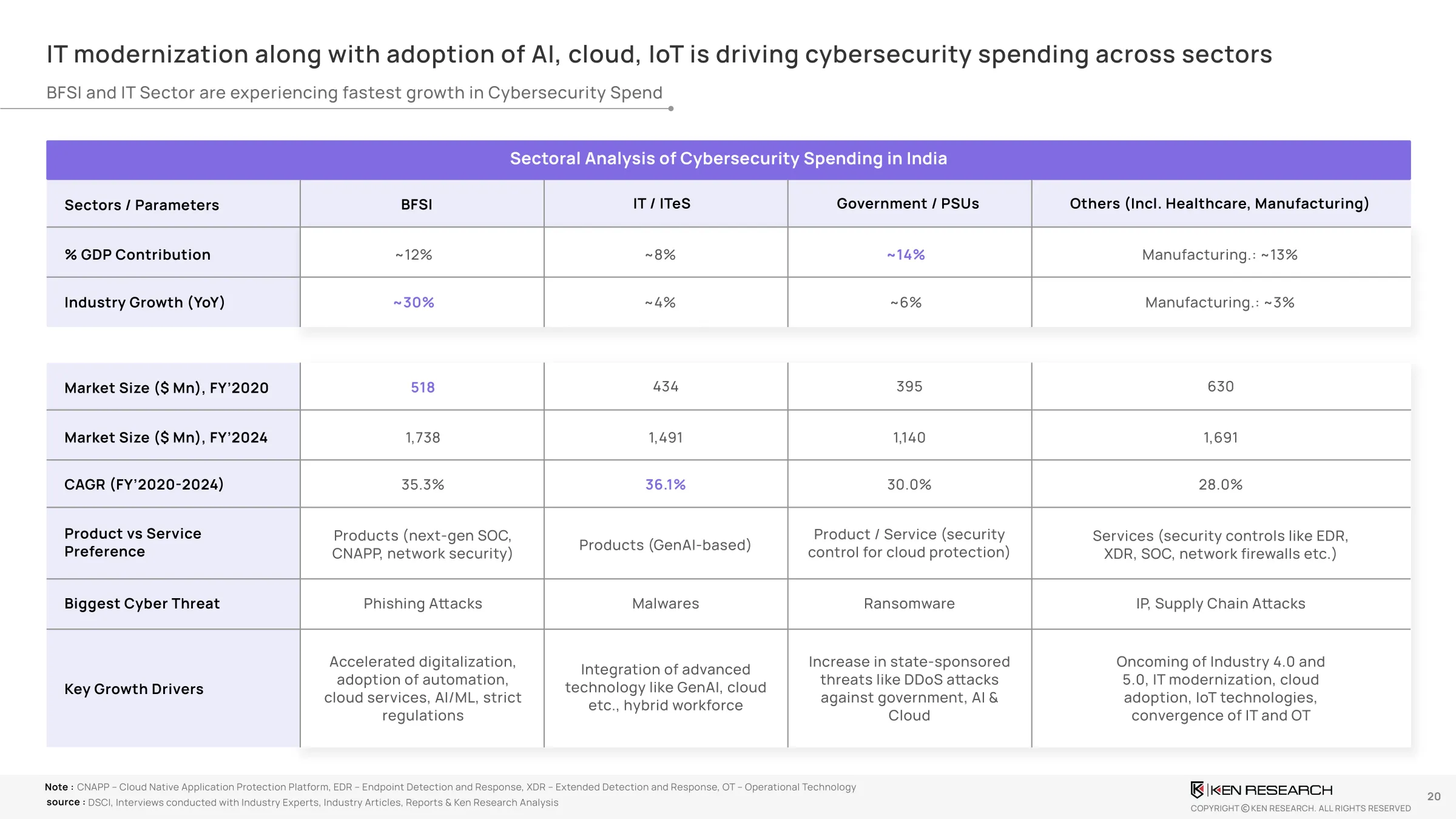
Emerging Trends And Technology Shifts
Zero Trust Architecture (ZTA): Less than 20% of organizations have implemented ZTA protocolsAI-Powered Threat Detection: While 62% of breaches go undetected for over 200 days, AI based anomaly detection reduces it by 40% on averageCybersecurity-as-a-Service (CaaS): Startups and SMBs are rapidly adopting subscription-based defense stacksRegulatory Push: India’s CERT-In and Digital Personal Data Protection Act are pushing compliance as a boardroom metric
Request Our Tech & Regulation Tracker for 2024–2026 Rollouts
India’s Cyber Maturity Scorecard (2023–2024)
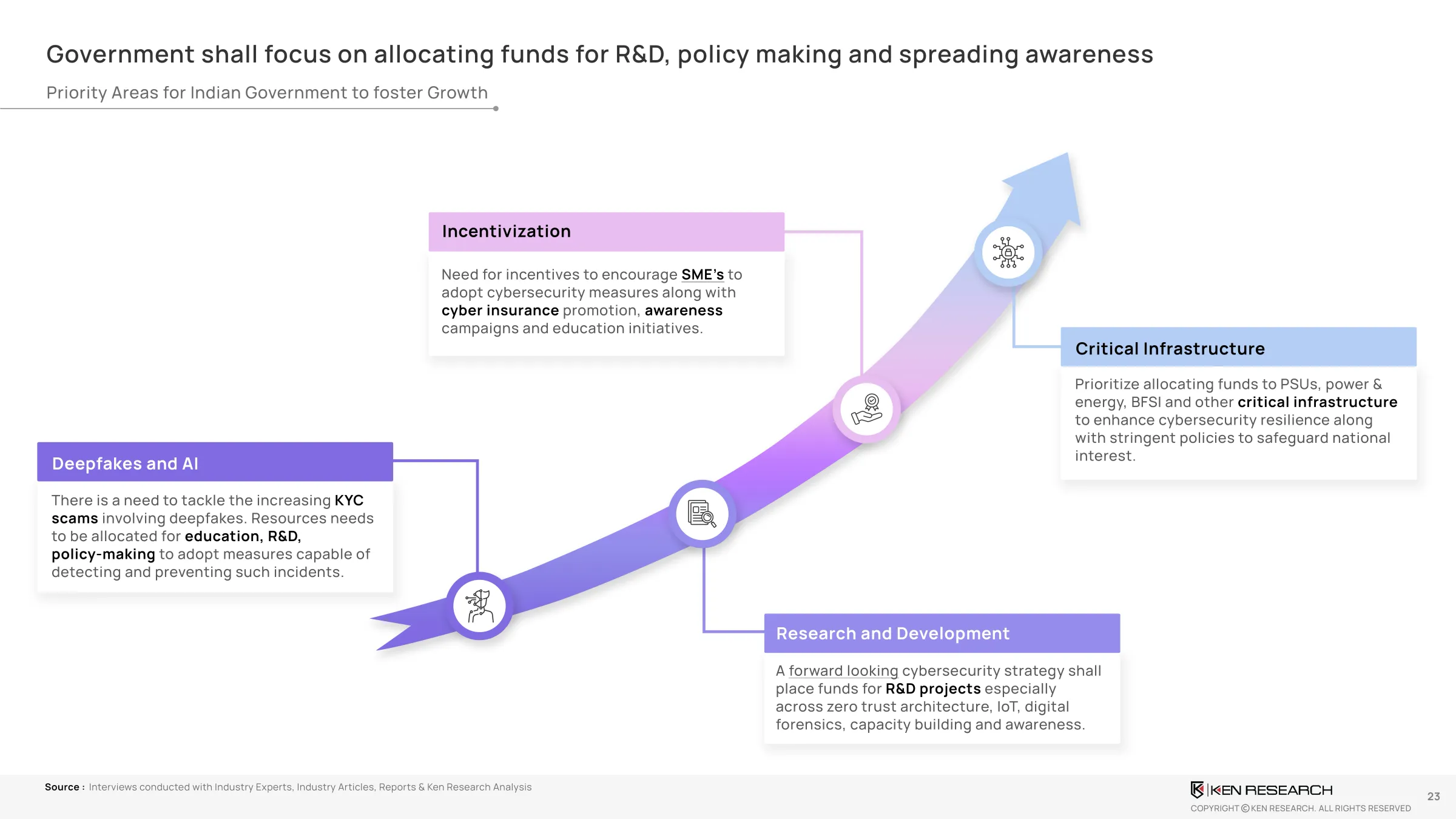
Strategic Framework for National Cyber Resilience
To enable scalable and sector-agnostic readiness, we propose a 5-layered framework:
- Perimeter & Endpoint Hardening: With secure BYOD and routine patch audits
- ZTA Implementation: Identity-first access with continuous validation
- AI-Driven Monitoring: For anomaly detection, behavior profiling, and SIEM integrations
- Employee Awareness & Training: Cyber drills, phishing simulations, and incident reportingSOPs
- Board-Level Governance: Cyber risk to be treated as core operational risk
Want to Customize This Framework for Your Enterprise? Book a Strategy Session
How Ken Research Can Help
Ken Research enables government, enterprise, and startups to assess, audit, and advance their cybersecurity maturity with:
- Gap Analysis & Sector Benchmarking
- Incident Readiness Drills & War Games
- ZTA & Identity Control Rollout Playbooks
- Tech + Regulation Heatmaps for India 2024–2026
FAQ's
Still Got Questions? Connect Via Mail
What is the current scale of India’s digital economy and its cyber risk?
India’s digital ecosystem is valued at over USD 1.2 trillion, while cyber threat damage is projected to cross ₹25,000 crore by 2028 if mitigation is not prioritized.
Which sectors are most exposed to cyber threats in India?
Government, Healthcare, BFSI, and IoT-enabled Smart Cities are currently the most at-risk sectors.
How prepared is India in terms of Zero Trust implementation?
As of 2024, less than 20% of public and private organizations have adopted robust Zero Trust protocols.
What frameworks exist to assess cyber readiness?
Ken Research applies a 5-Layered Cyber Readiness Framework including endpoint hardening, ZTA, AI monitoring, training, and governance.
Is AI helping reduce breach detection time?
Yes. AI-based threat detection cuts down average breach detection time by up to 40% compared to traditional monitoring.















