Region:Middle East
Author(s):Rebecca
Product Code:KRAD6246
Pages:99
Published On:December 2025
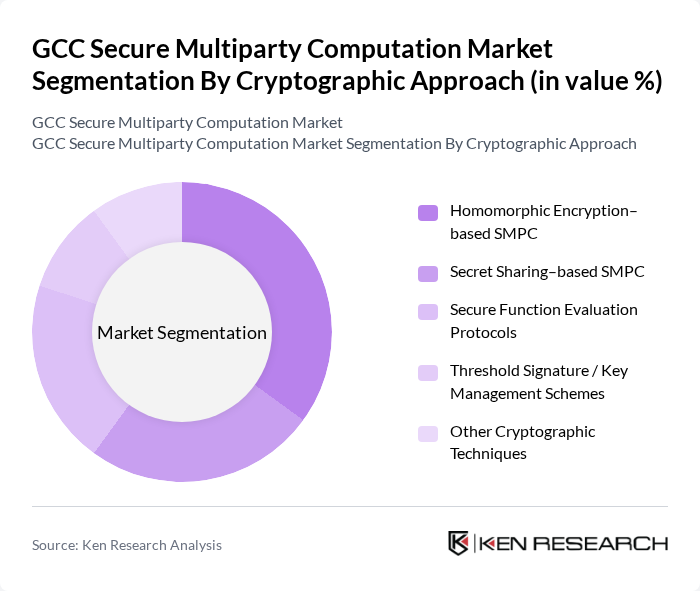
By Cryptographic Approach:The segmentation of the market by cryptographic approach includes various techniques that enhance the security and privacy of data during computation. The subsegments are Homomorphic Encryption–based SMPC, Secret Sharing–based SMPC, Secure Function Evaluation Protocols, Threshold Signature / Key Management Schemes, and Other Cryptographic Techniques. Among these, Homomorphic Encryption–based SMPC is gaining traction due to its ability to perform computations on encrypted data without needing to decrypt it first, thus ensuring data privacy. This approach is particularly favored in sectors like finance and healthcare, where sensitive data handling is critical.
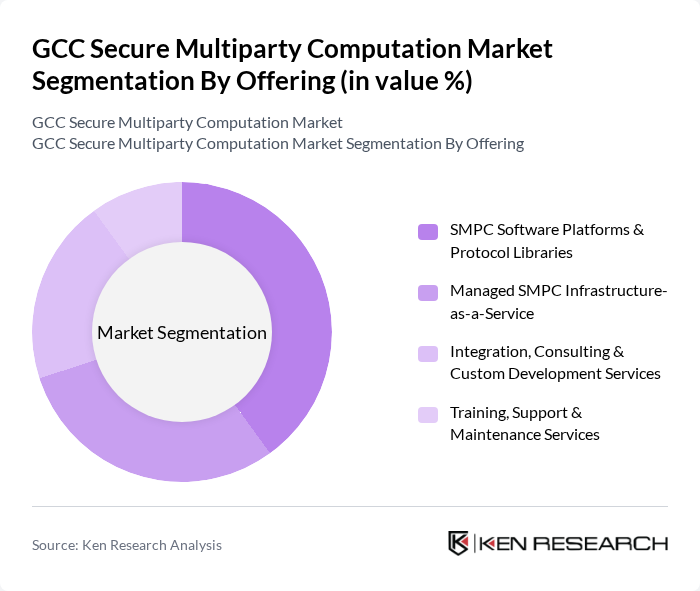
By Offering:The market segmentation by offering includes SMPC Software Platforms & Protocol Libraries, Managed SMPC Infrastructure-as-a-Service, Integration, Consulting & Custom Development Services, and Training, Support & Maintenance Services. The SMPC Software Platforms & Protocol Libraries segment is currently leading the market due to the increasing demand for ready-to-use solutions that facilitate secure multiparty computations. Organizations are increasingly opting for these platforms to streamline their operations while ensuring data privacy and compliance with regulations.
The GCC Secure Multiparty Computation Market is characterized by a dynamic mix of regional and international players. Leading participants such as IBM, Microsoft, Google (Google Cloud Platform), Intel, Amazon Web Services (AWS), Zama, Partisia, Enveil, Fireblocks, Sepior, Duality Technologies, Unbound Security (Checkpoint Software Technologies), Fortanix, CryptoExperts, Penta Security Systems contribute to innovation, geographic expansion, and service delivery in this space.
The GCC secure multiparty computation market is poised for significant growth as organizations increasingly prioritize data security and compliance. With the rise of AI and machine learning, the integration of these technologies into MPC solutions will enhance their effectiveness. Additionally, the expansion of decentralized finance (DeFi) will create new avenues for MPC applications, driving innovation. As businesses recognize the importance of ethical data practices, the demand for secure multiparty computation will continue to rise, shaping the future landscape of data security in the region.
| Segment | Sub-Segments |
|---|---|
| By Cryptographic Approach | Homomorphic Encryption–based SMPC Secret Sharing–based SMPC Secure Function Evaluation Protocols Threshold Signature / Key Management Schemes Other Cryptographic Techniques |
| By Offering | SMPC Software Platforms & Protocol Libraries Managed SMPC Infrastructure-as-a-Service Integration, Consulting & Custom Development Services Training, Support & Maintenance Services |
| By Application | Privacy-Preserving Analytics & Data Collaboration Secure Digital Asset & Key Management (Crypto Custody, DeFi) Privacy-Preserving Machine Learning & AI Model Training Fraud Detection, Risk Scoring & AML/KYC Secure Auctions, Bidding & Benchmarking Other Use Cases |
| By Deployment Model | On-Premises Public Cloud Private Cloud Hybrid & Multi-Cloud |
| By End-User Industry | Banking, Financial Services & Capital Markets Insurance & Takaful Healthcare & Life Sciences Government, Defense & Smart City Programs Telecommunications & ICT Service Providers Energy, Utilities & Industrial (Oil & Gas, Petrochemicals) Retail, E?commerce & Digital Platforms Other Enterprise verticals |
| By Organization Size | Large Enterprises Small & Medium Enterprises (SMEs) |
| By GCC Country | Saudi Arabia United Arab Emirates Qatar Kuwait Oman Bahrain |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Security Solutions | 100 | Chief Information Officers, Security Analysts |
| Healthcare Data Protection Strategies | 80 | IT Managers, Compliance Officers |
| Government Cybersecurity Initiatives | 70 | Policy Makers, IT Security Directors |
| Telecommunications Data Privacy Measures | 60 | Network Security Engineers, Operations Managers |
| Research and Development in Cryptography | 90 | Academic Researchers, Technology Developers |
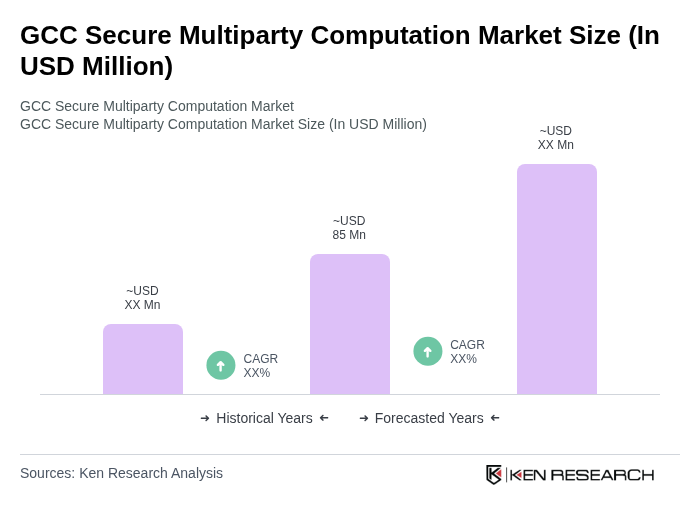
The GCC Secure Multiparty Computation market is valued at approximately USD 85 million, driven by increasing demand for data privacy and security solutions across sectors like finance, healthcare, and government.