Region:North America
Author(s):Rebecca
Product Code:KRAC3271
Pages:84
Published On:October 2025
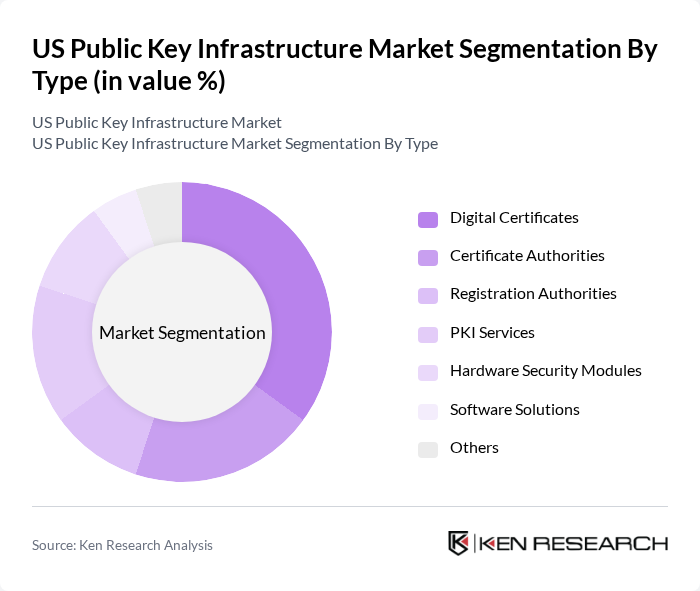
By Type:The market can be segmented into various types, including Digital Certificates, Certificate Authorities, Registration Authorities, PKI Services, Hardware Security Modules, Software Solutions, and Others. Among these, Digital Certificates are leading the market due to their essential role in establishing secure communications and transactions over the internet. The increasing reliance on e-commerce, remote work, and online services has significantly boosted the demand for digital certificates, making them a critical component of the PKI ecosystem. The solutions segment, which includes digital certificates and certificate authorities, accounts for the largest share, reflecting the priority placed on secure authentication and encryption .
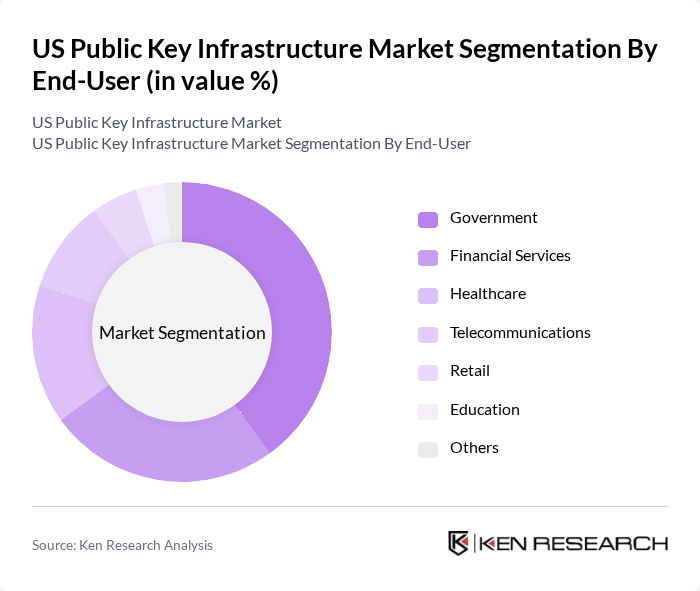
By End-User:The end-user segmentation includes Government, Financial Services, Healthcare, Telecommunications, Retail, Education, and Others. The Government sector is the dominant end-user, driven by stringent regulations and the need for secure communication channels. Government agencies are increasingly adopting PKI solutions to protect sensitive data and ensure secure transactions, particularly in areas such as defense, public safety, and citizen services. Financial services and healthcare sectors also show strong adoption due to regulatory compliance requirements and the need for robust data protection .
The US Public Key Infrastructure Market is characterized by a dynamic mix of regional and international players. Leading participants such as DigiCert, Inc., GlobalSign, Inc., Entrust Datacard Corporation, Sectigo Limited, Thales Group, IdenTrust, Inc., Microsoft Corporation, Amazon Web Services, Inc., IBM Corporation, RSA Security LLC, Venafi, Inc., Keyfactor, Inc., Google LLC, NEC Corporation, NTT DATA Group Corporation contribute to innovation, geographic expansion, and service delivery in this space.
The US Public Key Infrastructure market is poised for significant evolution, driven by technological advancements and increasing regulatory pressures. As organizations adopt decentralized identity management and integrate artificial intelligence into security protocols, the landscape will shift towards more user-centric solutions. The rise of mobile PKI solutions will further enhance accessibility and convenience, catering to the growing demand for secure digital interactions. These trends indicate a robust future for PKI, emphasizing the need for continuous innovation and adaptation in security practices.
| Segment | Sub-Segments |
|---|---|
| By Type | Digital Certificates Certificate Authorities Registration Authorities PKI Services Hardware Security Modules Software Solutions Others |
| By End-User | Government Financial Services Healthcare Telecommunications Retail Education Others |
| By Application | Secure Email Secure Web Access Digital Signatures Data Encryption Identity Management Others |
| By Component | Hardware Software Services |
| By Sales Channel | Direct Sales Distributors Online Sales Resellers |
| By Distribution Mode | Online Distribution Offline Distribution |
| By Policy Support | Government Subsidies Tax Incentives Grants for Cybersecurity Initiatives Others |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services PKI Implementation | 100 | IT Security Managers, Compliance Officers |
| Healthcare Data Protection Strategies | 60 | Chief Information Security Officers, Data Privacy Officers |
| Government Agency Cybersecurity Protocols | 50 | Cybersecurity Analysts, IT Directors |
| Enterprise PKI Adoption Trends | 90 | Network Administrators, IT Managers |
| Cloud Service Provider PKI Solutions | 40 | Cloud Security Architects, Security Engineers |
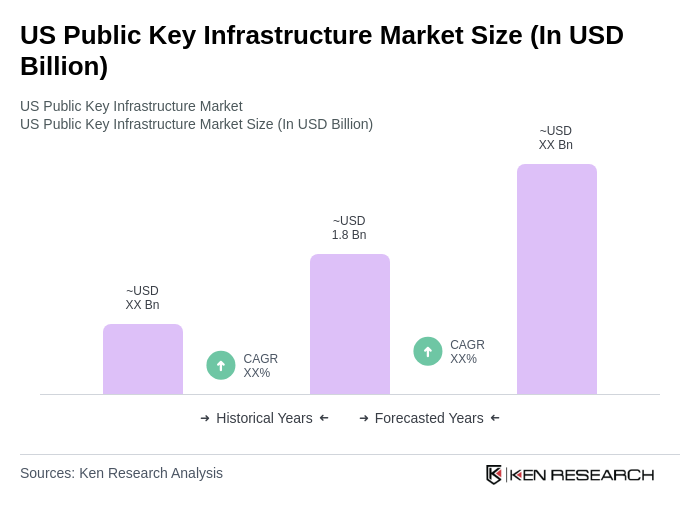
The US Public Key Infrastructure (PKI) market is valued at approximately USD 1.8 billion, reflecting a significant investment by organizations in secure digital communications, driven by increasing cyber threats and the adoption of cloud-based services.