Region:North America
Author(s):Geetanshi
Product Code:KRAA3704
Pages:87
Published On:September 2025
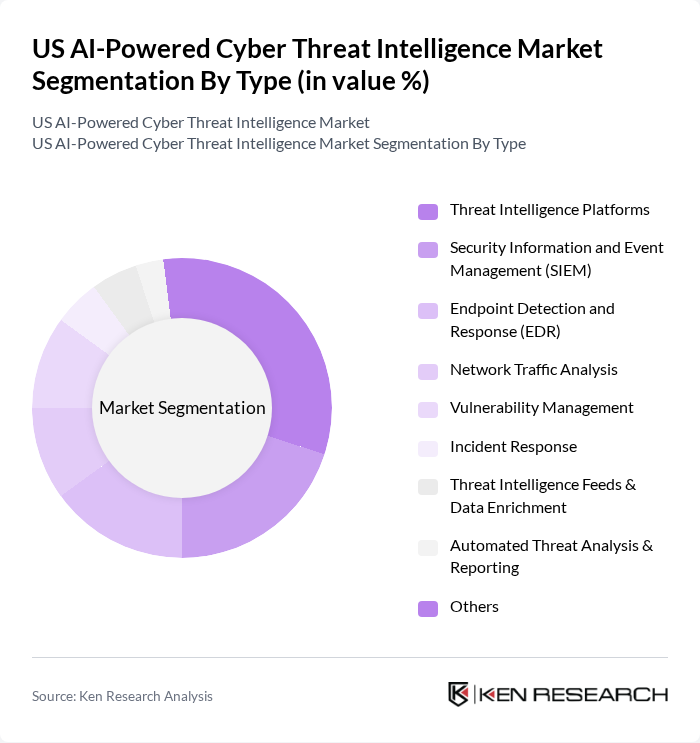
By Type:The market is segmented into various types of AI-powered cyber threat intelligence solutions, including Threat Intelligence Platforms, Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), Network Traffic Analysis, Vulnerability Management, Incident Response, Threat Intelligence Feeds, User and Entity Behavior Analytics (UEBA), and Others. Each of these sub-segments plays a crucial role in enhancing cybersecurity measures across different industries. Threat Intelligence Platforms and SIEM solutions are particularly prominent, enabling real-time detection, automated response, and actionable insights for organizations facing advanced persistent threats and ransomware attacks. Endpoint Detection and Response (EDR) and Network Traffic Analysis are increasingly integrated with AI to improve anomaly detection and reduce response times .
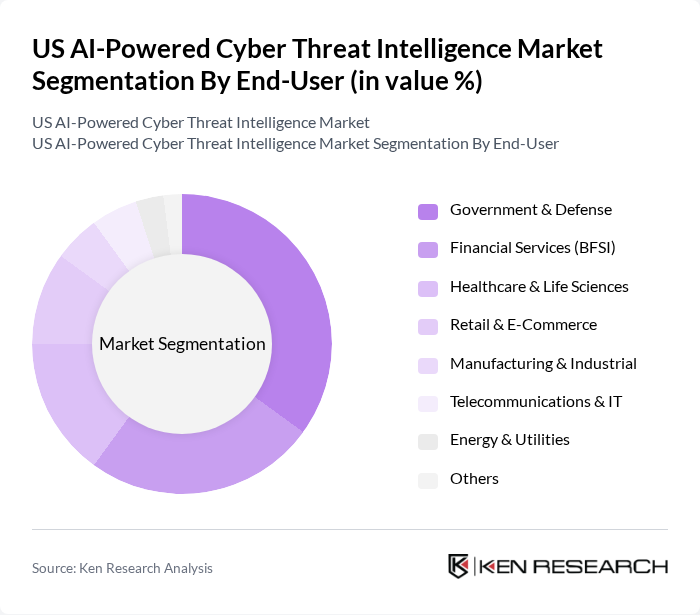
By End-User:The end-user segmentation includes Government & Defense, Banking, Financial Services & Insurance (BFSI), Healthcare & Life Sciences, Retail & E-commerce, Manufacturing, Energy & Utilities, Telecommunications, and Others. Each sector has unique cybersecurity needs, driving the demand for tailored AI-powered solutions to mitigate risks and enhance security protocols. Government & Defense and BFSI sectors account for the largest share, reflecting the critical need for advanced threat intelligence and compliance with evolving regulations. Healthcare and Retail sectors are rapidly increasing adoption due to heightened risks of data breaches and ransomware attacks .
The US AI-Powered Cyber Threat Intelligence Market is characterized by a dynamic mix of regional and international players. Leading participants such as IBM Corporation, Cisco Systems, Inc., Palo Alto Networks, Inc., Mandiant (A Google Company), CrowdStrike Holdings, Inc., Trellix (formerly McAfee Enterprise & FireEye), Check Point Software Technologies Ltd., Splunk Inc., Fortinet, Inc., ThreatConnect, Inc., Recorded Future, Inc., Digital Shadows Ltd., RiskIQ, Inc. (A Microsoft Company), Verint Systems Inc., Cybereason Inc., SentinelOne, Inc., Anomali, Inc., IntSights Cyber Intelligence Ltd. (A Rapid7 Company), Kaspersky Lab, Proofpoint, Inc. contribute to innovation, geographic expansion, and service delivery in this space. These companies leverage AI-powered analytics, cloud-native threat feeds, and industry-specific solutions to address evolving cyber risks and regulatory requirements, solidifying the US market’s leadership in threat intelligence .
As the landscape of cyber threats continues to evolve, the demand for AI-powered cyber threat intelligence solutions is expected to intensify. Organizations will increasingly prioritize investments in advanced technologies to enhance their cybersecurity posture. The integration of machine learning and automation will play a pivotal role in improving threat detection and response capabilities. Furthermore, the rise of managed security service providers (MSSPs) will facilitate access to sophisticated cybersecurity solutions, enabling businesses to better navigate the complexities of the digital threat environment.
| Segment | Sub-Segments |
|---|---|
| By Type | Threat Intelligence Platforms Security Information and Event Management (SIEM) Endpoint Detection and Response (EDR) Network Traffic Analysis Vulnerability Management Incident Response Threat Intelligence Feeds User and Entity Behavior Analytics (UEBA) Others |
| By End-User | Government & Defense Banking, Financial Services & Insurance (BFSI) Healthcare & Life Sciences Retail & E-commerce Manufacturing Energy & Utilities Telecommunications Others |
| By Deployment Mode | On-Premises Cloud-Based Hybrid |
| By Service Type | Consulting Services Managed Services Training and Support Integration & Implementation |
| By Industry Vertical | BFSI Government and Defense Energy and Utilities Healthcare Retail IT & Telecom Others |
| By Geography | US (by State/Region) Canada Mexico |
| By Pricing Model | Subscription-Based Pay-Per-Use License Fee Freemium/Trial |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Cybersecurity | 100 | Chief Information Security Officers, IT Security Managers |
| Healthcare AI Threat Intelligence | 60 | Healthcare IT Directors, Compliance Officers |
| Government Cyber Defense Strategies | 50 | Government Cybersecurity Officials, Policy Makers |
| Retail Sector Cybersecurity Solutions | 70 | IT Managers, Risk Management Officers |
| Manufacturing Industry Cyber Threats | 55 | Operations Managers, Cybersecurity Analysts |
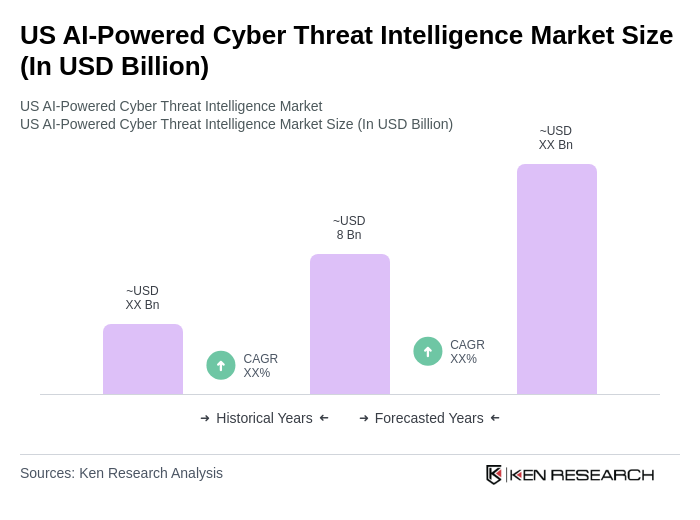
The US AI-Powered Cyber Threat Intelligence Market is valued at approximately USD 8 billion, reflecting significant growth driven by the increasing frequency and sophistication of cyber threats and the rising adoption of AI technologies in cybersecurity solutions.