Region:Middle East
Author(s):Shubham
Product Code:KRAC0736
Pages:86
Published On:August 2025
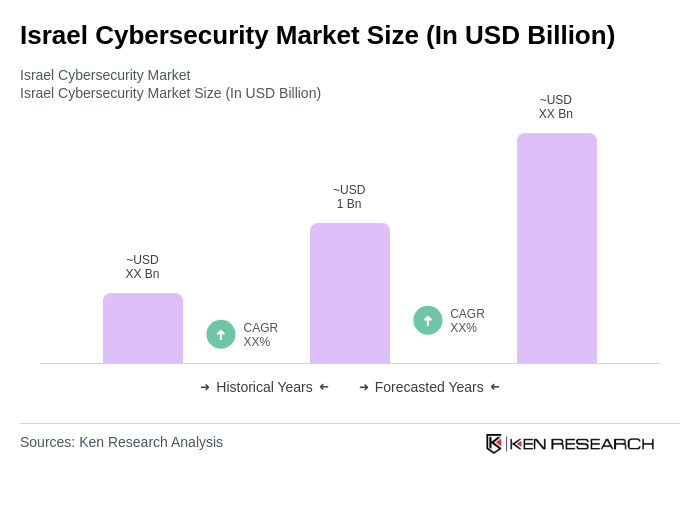
By Type:The segmentation of the market by type includes various subsegments that cater to different aspects of cybersecurity. The primary subsegments are Network Security, Application Security, Endpoint and Extended Detection & Response, Cloud Security, Data Security, Identity and Privileged Access Management, Email and Content Security, OT/IoT and Automotive Security, Threat Intelligence, and Others. Among these, Network Security is currently the leading subsegment due to the increasing need for organizations to protect their networks from sophisticated cyber threats. Recent enterprise priorities in Israel also show elevated demand in cloud security (CSPM/CNAPP), identity and privileged access, and threat detection/response, aligned with rapid cloud adoption and complex hybrid environments.
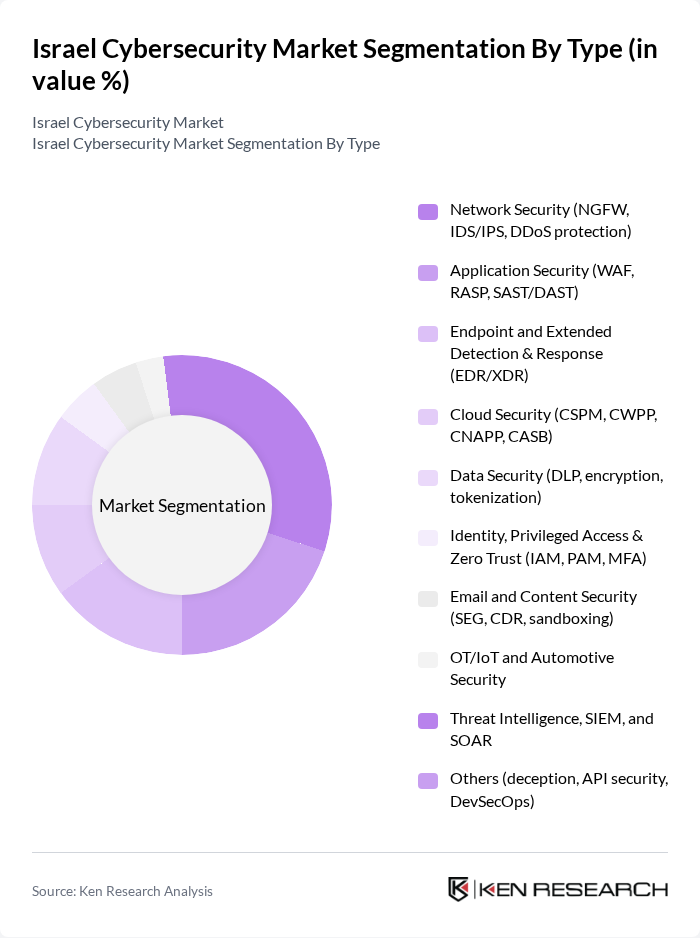
By End-User:The market segmentation by end-user includes various sectors such as Government and Public Sector, Banking, Financial Services and Insurance (BFSI), Healthcare and Life Sciences, Retail and E-commerce, IT & Telecommunications, Manufacturing & Industrial, Defense and Homeland Security, Energy & Utilities, Education & Research, and Others. The BFSI sector is the dominant end-user due to its critical need for robust cybersecurity measures to protect sensitive financial data and comply with regulatory requirements. Public sector and defense/homeland security are also significant demand centers, reflecting Israel’s national security posture and critical infrastructure protection priorities.
The Israel Cybersecurity Market is characterized by a dynamic mix of regional and international players. Leading participants such as Check Point Software Technologies Ltd., CyberArk Software Ltd., Radware Ltd., Palo Alto Networks, Inc., Fortinet, Inc., Imperva, Inc., SentinelOne, Inc., NSO Group Technologies Ltd., Snyk Ltd., Aqua Security Software Ltd., Votiro Technologies Ltd., Cato Networks Ltd., Cybereason Inc., Argus Cyber Security Ltd., Morphisec Ltd., Armis Security Ltd., Claroty Ltd., Wiz, Inc., Guardicore Ltd. (now Akamai Enterprise Security), Perimeter 81 Ltd. contribute to innovation, geographic expansion, and service delivery in this space.
The Israel cybersecurity market is poised for significant evolution, driven by technological advancements and increasing regulatory pressures. As organizations prioritize cybersecurity, the adoption of managed security services and zero trust models will become more prevalent. Additionally, the integration of AI and machine learning in cybersecurity solutions will enhance threat detection and response capabilities. The market is expected to witness a surge in innovative startups, further contributing to a dynamic and competitive landscape in the coming years.
| Segment | Sub-Segments |
|---|---|
| By Type | Network Security (NGFW, IDS/IPS, DDoS protection) Application Security (WAF, RASP, SAST/DAST) Endpoint and Extended Detection & Response (EDR/XDR) Cloud Security (CSPM, CWPP, CNAPP, CASB) Data Security (DLP, encryption, tokenization) Identity, Privileged Access & Zero Trust (IAM, PAM, MFA) Email and Content Security (SEG, CDR, sandboxing) OT/IoT and Automotive Security Threat Intelligence, SIEM, and SOAR Others (deception, API security, DevSecOps) |
| By End-User | Government and Public Sector Banking, Financial Services and Insurance (BFSI) Healthcare and Life Sciences Retail and E?commerce IT & Telecommunications Manufacturing & Industrial (including critical OT) Defense and Homeland Security Energy & Utilities Education & Research Others (media, agriculture tech, smart cities) |
| By Industry Vertical | Defense & Aerospace Energy (power grid, oil & gas, water) Transportation & Mobility (aviation, rail, automotive) Education & Public Research Technology, Software & Cloud Financial Services Others (media, logistics, agriculture) |
| By Deployment Mode | On-Premises Cloud-Based (public, private, multicloud) Hybrid |
| By Service Type | Consulting & Advisory (risk, compliance, architecture) Managed Security Services (MSSP, MDR) Professional Services (integration, incident response) Training and Education |
| By Sales Channel | Direct Sales Value-Added Resellers & Distributors Online & Marketplace Channels |
| By Policy Support | INCD Programs & Government Grants Tax Incentives & R&D Credits Public-Private Partnerships and National Initiatives |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Sector Cybersecurity | 120 | CISOs, IT Security Managers |
| Healthcare Cybersecurity Solutions | 90 | Compliance Officers, IT Directors |
| Government Cybersecurity Initiatives | 70 | Policy Makers, Cybersecurity Analysts |
| SME Cybersecurity Practices | 100 | Business Owners, IT Administrators |
| Cybersecurity Startups Insights | 60 | Founders, Product Managers |
The Israel Cybersecurity Market is valued at approximately USD 1 billion, driven by increasing cyber threats, digital transformation, and significant investments from enterprises and the government in advanced security measures across critical sectors.