Region:Middle East
Author(s):Dev
Product Code:KRAA8209
Pages:89
Published On:November 2025
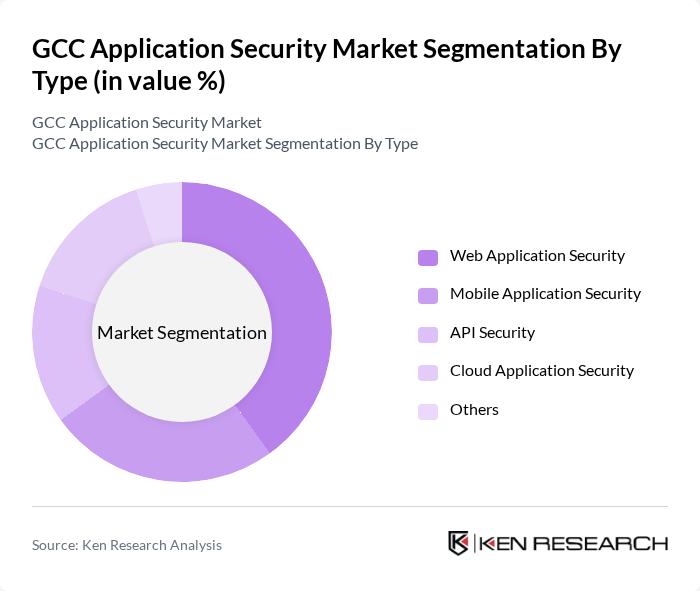
By Type:The market is segmented into Web Application Security, Mobile Application Security, API Security, Cloud Application Security, and Others. Web Application Security remains the leading segment due to the region’s heavy reliance on web-based platforms and the surge in cyberattacks targeting web applications. Organizations are prioritizing web application security to address vulnerabilities such as cross-site scripting, SQL injection, and to comply with evolving regulatory standards.
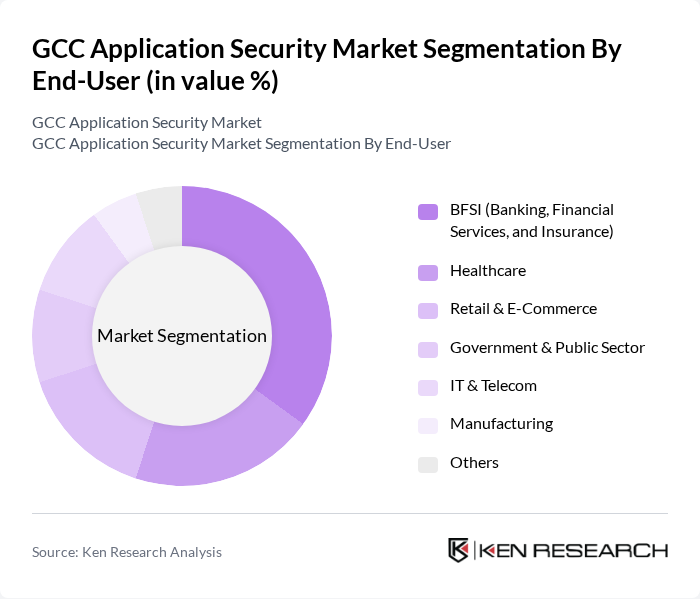
By End-User:The end-user segmentation includes BFSI (Banking, Financial Services, and Insurance), Healthcare, Retail & E-Commerce, Government & Public Sector, IT & Telecom, Manufacturing, and Others. The BFSI sector is the dominant segment, driven by stringent regulatory requirements, high-value data, and the need to mitigate risks associated with financial fraud and data breaches. Financial institutions in the GCC are increasingly adopting multi-layered application security solutions to comply with sector-specific standards and protect customer assets.
The GCC Application Security Market is characterized by a dynamic mix of regional and international players. Leading participants such as Checkmarx, Veracode, Fortify (Micro Focus), Synopsys, Snyk, Rapid7, Qualys, IBM Security, Cisco, Palo Alto Networks, Trend Micro, McAfee, CrowdStrike, RSA Security, Help AG (Etisalat Digital), Spire Solutions, DarkMatter, Paladion (Atos), DTS Solution, and Injazat contribute to innovation, geographic expansion, and service delivery in this space.
The GCC application security market is poised for significant evolution, driven by technological advancements and increasing awareness of cybersecurity risks. As organizations adopt DevSecOps practices, the integration of security into the software development lifecycle will become standard. Additionally, the rise of AI-driven security solutions will enhance threat detection and response capabilities. With regulatory pressures intensifying, businesses will prioritize compliance, leading to a more robust application security landscape in the region, fostering innovation and resilience against cyber threats.
| Segment | Sub-Segments |
|---|---|
| By Type | Web Application Security Mobile Application Security API Security Cloud Application Security Others |
| By End-User | BFSI (Banking, Financial Services, and Insurance) Healthcare Retail & E-Commerce Government & Public Sector IT & Telecom Manufacturing Others |
| By Deployment Model | On-Premises Cloud-Based Hybrid Others |
| By Industry Vertical | BFSI IT & Telecom Healthcare Retail & E-Commerce Government Manufacturing Education Others |
| By Security Type | Application Security Network Security Endpoint Security Data Security Cloud Security Others |
| By Service Type | Consulting Services Managed Services Training and Education Implementation & Integration Support & Maintenance Others |
| By Region | Saudi Arabia United Arab Emirates Qatar Kuwait Oman Bahrain Others |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Application Security | 100 | IT Security Managers, Compliance Officers |
| Healthcare Software Security | 80 | Application Developers, IT Directors |
| Retail E-commerce Security | 60 | Cybersecurity Analysts, Operations Managers |
| Government Digital Services Security | 50 | Policy Makers, IT Security Consultants |
| Telecommunications Application Security | 70 | Network Security Engineers, Risk Management Officers |
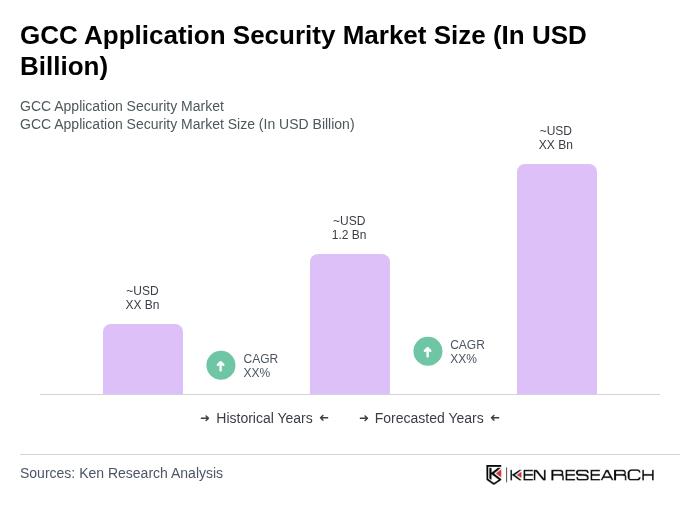
The GCC Application Security Market is valued at approximately USD 1.2 billion, driven by increasing cyber threats, the adoption of cloud and mobile applications, and regulatory requirements for data protection.