Region:Middle East
Author(s):Rebecca
Product Code:KRAD4388
Pages:97
Published On:December 2025
By Type:The market is segmented into various types of cybersecurity services, including Network Security, Endpoint & IoT Security, Application Security, Cloud Security, Data Security & Privacy, Identity and Access Management, and Infrastructure Protection. Each of these segments plays a crucial role in addressing specific security needs of organizations.
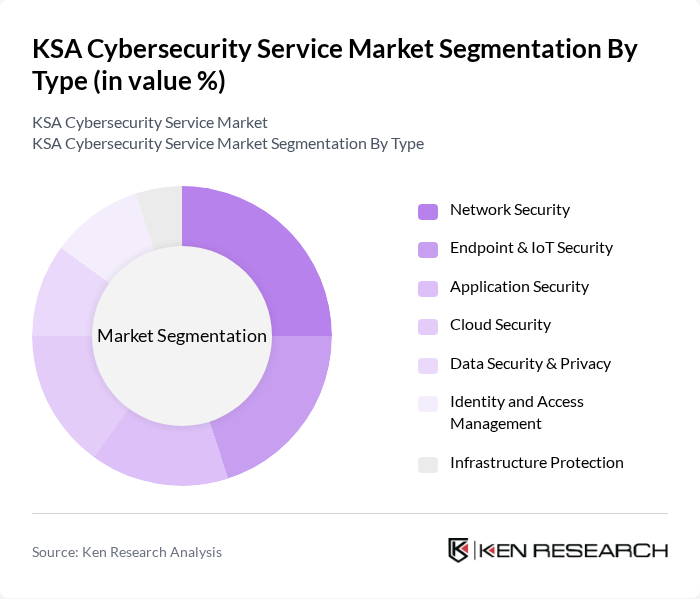
The leading sub-segment in the market is Network Security, which is crucial for protecting organizational networks from unauthorized access and cyber threats. The increasing number of cyberattacks targeting network vulnerabilities has heightened the demand for robust network security solutions. Organizations are investing heavily in advanced firewalls, intrusion detection systems, and secure access technologies to safeguard their networks, making this segment a priority for cybersecurity investments.
By End-User:The market is segmented by end-users, including BFSI (Banking, Financial Services & Insurance), Healthcare, IT & Telecommunications, Government & Defense, Retail, and Energy and Utilities. Each sector has unique cybersecurity needs based on the sensitivity of the data they handle and the regulatory requirements they must meet.
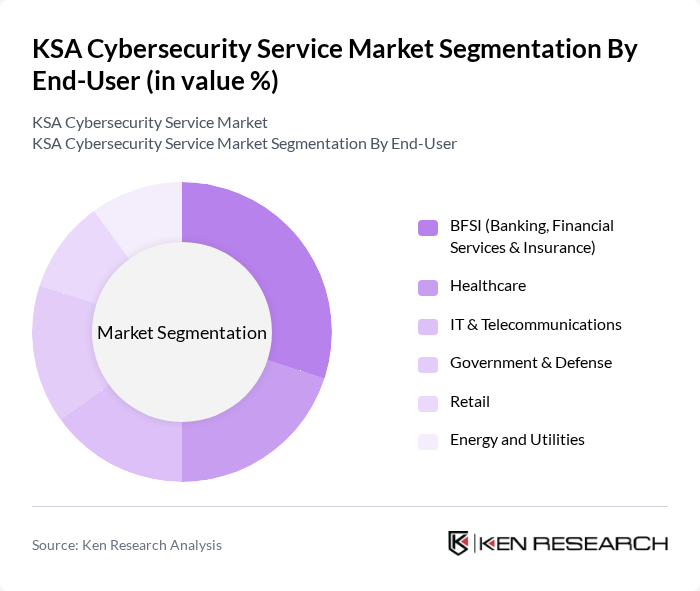
The BFSI sector is the dominant end-user in the market, driven by the critical need for data protection and compliance with stringent regulations. Financial institutions are prime targets for cyberattacks, necessitating advanced security measures to protect sensitive customer information and financial transactions. As a result, investments in cybersecurity solutions within this sector are substantial, making it a key driver of market growth.
The KSA Cybersecurity Service Market is characterized by a dynamic mix of regional and international players. Leading participants such as STC Cybersecurity, DarkMatter, Cisco Systems, Palo Alto Networks, IBM Security, Fortinet, Check Point Software Technologies, Trend Micro, McAfee, CrowdStrike, Broadcom Inc., Sophos, Proofpoint, LogRhythm, BAE Systems PLC contribute to innovation, geographic expansion, and service delivery in this space.
The KSA cybersecurity service market is poised for significant growth, driven by increasing cyber threats and government support. As organizations prioritize cybersecurity, the integration of advanced technologies such as AI and machine learning will become more prevalent. Additionally, the collaboration between local firms and international cybersecurity experts will enhance the overall security landscape. With a focus on compliance and risk management, the market is expected to evolve, adapting to emerging threats and fostering a culture of cybersecurity awareness across various sectors.
| Segment | Sub-Segments |
|---|---|
| By Type | Network Security Endpoint & IoT Security Application Security Cloud Security Data Security & Privacy Identity and Access Management Infrastructure Protection |
| By End-User | BFSI (Banking, Financial Services & Insurance) Healthcare IT & Telecommunications Government & Defense Retail Energy and Utilities |
| By Industry Vertical | BFSI Energy and Utilities Manufacturing Construction Transportation and Logistics |
| By Deployment Model | On-Premises Cloud-Based Hybrid |
| By Service Type | Professional Services Managed Security Services Incident Response Services Training and Awareness Services |
| By Region | Northern and Central Region Eastern Region Western Region Southern Region |
| By Organization Size | Large Enterprises Medium Enterprises Small Enterprises |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Sector Cybersecurity | 120 | IT Security Managers, Risk Assessment Officers |
| Healthcare Cybersecurity Solutions | 90 | Compliance Officers, IT Directors |
| Energy Sector Cyber Defense | 80 | Cybersecurity Analysts, Operations Managers |
| Government Cybersecurity Initiatives | 100 | Policy Makers, IT Governance Heads |
| SME Cybersecurity Needs | 70 | Business Owners, IT Consultants |
The KSA Cybersecurity Service Market is valued at approximately USD 4.70 billion, reflecting significant growth driven by increasing cyber threats and the government's commitment to enhancing national cybersecurity infrastructure under Vision 2030.