Region:Middle East
Author(s):Rebecca
Product Code:KRAC4616
Pages:82
Published On:October 2025
By Type:The market is segmented into various types of endpoint protection solutions, including Antivirus Software, Endpoint Detection and Response (EDR), Mobile Device Management (MDM), Data Loss Prevention (DLP), Threat Intelligence Platforms, Application Control, Encryption Solutions, and Others. Each of these sub-segments plays a crucial role in addressing specific security needs of organizations.
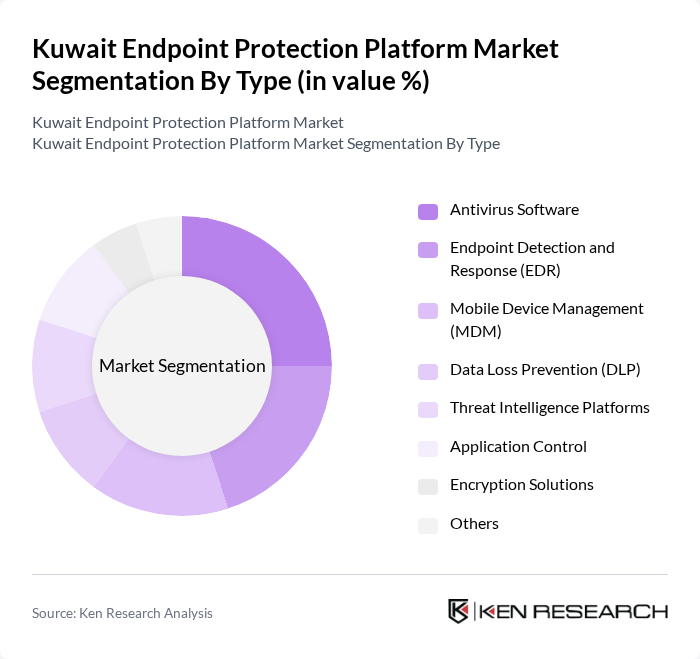
The Antivirus Software segment is currently dominating the market due to its widespread adoption among organizations of all sizes. Businesses prioritize basic protection against malware and viruses, making antivirus solutions a fundamental component of their cybersecurity strategy. The increasing number of cyber threats and the need for basic security measures drive the demand for antivirus software. Additionally, the ease of deployment and user-friendly interfaces contribute to its popularity among small and medium enterprises.
By End-User:The market is segmented by end-users, including Small and Medium Enterprises (SMEs), Large Enterprises, Government Agencies, Educational Institutions, and Healthcare Providers. Each end-user segment has unique security requirements and compliance standards that influence their choice of endpoint protection solutions.
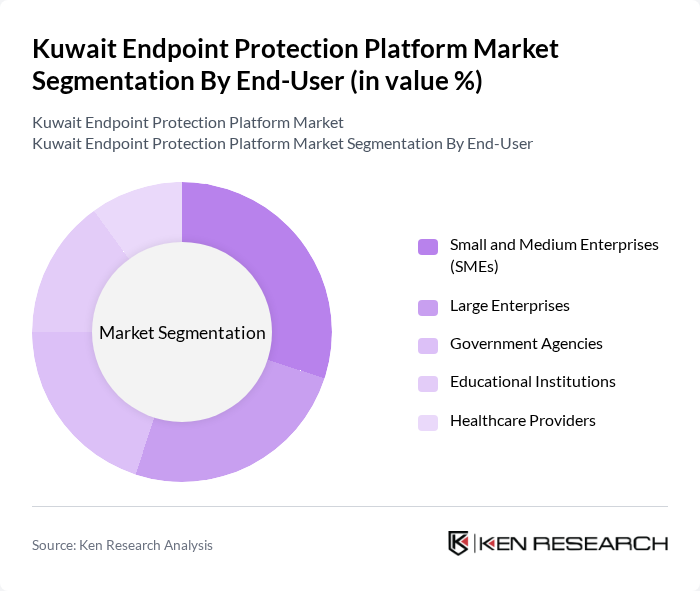
The Small and Medium Enterprises (SMEs) segment is leading the market as these organizations increasingly recognize the importance of cybersecurity in protecting their assets. SMEs are often targeted by cybercriminals due to their perceived vulnerabilities, prompting them to invest in endpoint protection solutions. The affordability and scalability of these solutions make them attractive to SMEs, driving their growth in the market.
The Kuwait Endpoint Protection Platform market is characterized by a dynamic mix of regional and international players. Leading participants such as McAfee LLC, Broadcom Inc. (Symantec Enterprise Division), Trend Micro Incorporated, Sophos Group plc, Kaspersky Lab, Bitdefender LLC, CrowdStrike Holdings, Inc., Palo Alto Networks, Inc., Check Point Software Technologies Ltd., Fortinet, Inc., Cisco Systems, Inc., Trellix (formerly FireEye and McAfee Enterprise), ESET, spol. s r.o., Webroot Inc., Avast Software s.r.o., Microsoft Corporation, ManageEngine (Zoho Corporation), Help AG (Etisalat Group), Gulf Business Machines (GBM), Trend Micro Gulf FZE contribute to innovation, geographic expansion, and service delivery in this space.
The future of the Kuwait Endpoint Protection Platform market appears promising, driven by the increasing integration of advanced technologies such as artificial intelligence and machine learning. As organizations prioritize cybersecurity, the demand for innovative solutions that offer real-time threat detection and response capabilities will rise. Additionally, the growing emphasis on regulatory compliance will further propel investments in endpoint protection, ensuring that businesses remain resilient against evolving cyber threats while safeguarding sensitive data.
| Segment | Sub-Segments |
|---|---|
| By Type | Antivirus Software Endpoint Detection and Response (EDR) Mobile Device Management (MDM) Data Loss Prevention (DLP) Threat Intelligence Platforms Application Control Encryption Solutions Others |
| By End-User | Small and Medium Enterprises (SMEs) Large Enterprises Government Agencies Educational Institutions Healthcare Providers |
| By Deployment Model | On-Premises Cloud-Based Hybrid |
| By Industry Vertical | Financial Services Healthcare Retail Manufacturing Oil & Gas Government & Defense Others |
| By Region | Central Kuwait Southern Kuwait Northern Kuwait Eastern Kuwait |
| By Sales Channel | Direct Sales Distributors Online Sales |
| By Pricing Model | Subscription-Based One-Time License Fee Freemium |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Cybersecurity | 60 | IT Security Managers, Compliance Officers |
| Healthcare Endpoint Protection | 40 | Healthcare IT Directors, Risk Management Officers |
| Government Sector Cybersecurity | 50 | Cybersecurity Analysts, IT Administrators |
| Retail Industry Security Solutions | 40 | Operations Managers, IT Support Staff |
| Telecommunications Endpoint Security | 50 | Network Security Engineers, Product Managers |
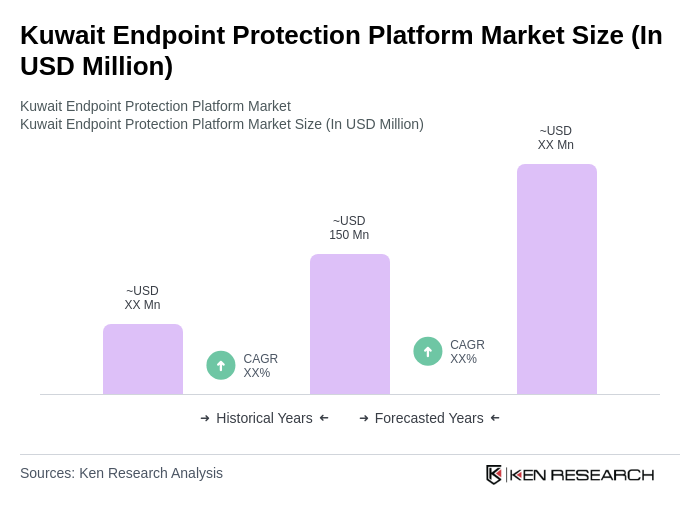
The Kuwait Endpoint Protection Platform market is valued at approximately USD 150 million, driven by increasing cyber threats, digital transformation initiatives, and heightened awareness of data security among businesses.