Region:Middle East
Author(s):Shubham
Product Code:KRAC8932
Pages:85
Published On:November 2025
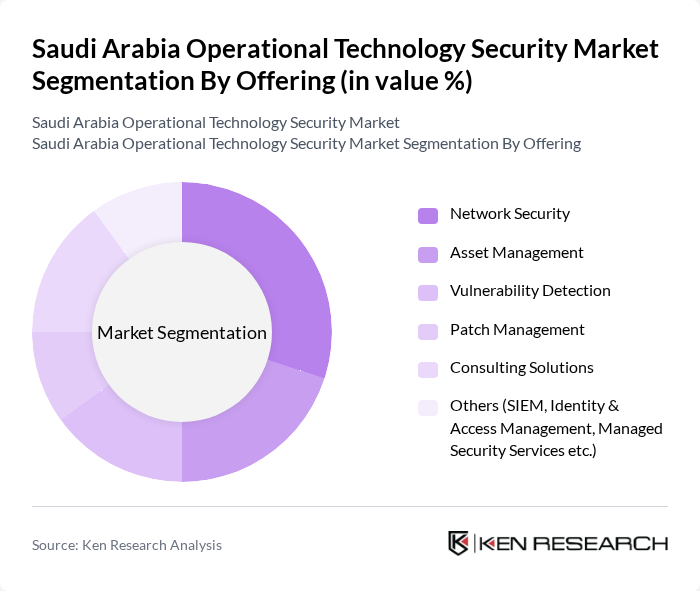
By Offering:The market is segmented into various offerings that address the evolving security requirements of organizations. The primary subsegments include Network Security, Asset Management, Vulnerability Detection, Patch Management, Consulting Solutions, and Others, such as SIEM, Identity & Access Management, and Managed Security Services. Network Security remains the dominant segment, driven by the convergence of IT and OT systems and the critical need to safeguard industrial networks against cyberattacks. Asset Management and Vulnerability Detection are also gaining traction as organizations seek to enhance visibility and proactively address security gaps in their operational environments .
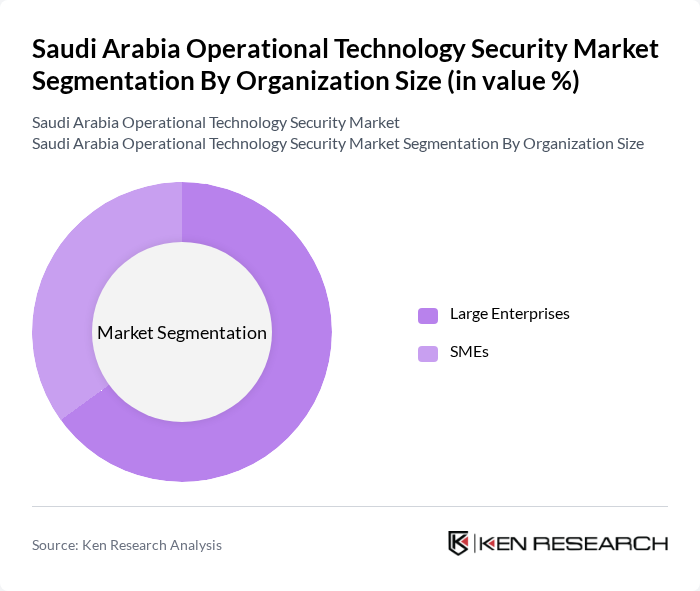
By Organization Size:The market is segmented by organization size into Large Enterprises and SMEs. Large Enterprises maintain a dominant market share, attributed to their greater financial resources and the complexity of their operational technology environments, which necessitate advanced security investments. SMEs are increasingly adopting OT security solutions, particularly as government incentives and service-based security models become more accessible, though they continue to face budgetary and resource constraints .
The Saudi Arabia Operational Technology Security Market is characterized by a dynamic mix of regional and international players. Leading participants such as Siemens AG, Honeywell International Inc., Schneider Electric SE, Rockwell Automation, Inc., ABB Ltd., Cisco Systems, Inc., Palo Alto Networks, Inc., Fortinet, Inc., Check Point Software Technologies Ltd., McAfee Corp., Trend Micro Incorporated, Trellix, Kaspersky Lab, CrowdStrike Holdings, Inc., Darktrace Ltd., Saudi Information Technology Company (SITE), Elm Company, STC Solutions, SABB Digital Security, CyberX (Microsoft) contribute to innovation, geographic expansion, and service delivery in this space.
The future of the operational technology security market in Saudi Arabia appears promising, driven by increasing digitalization and a heightened focus on cybersecurity. As organizations continue to adopt IoT and smart technologies, the integration of IT and OT security will become essential. Furthermore, the government's commitment to enhancing cybersecurity regulations will likely foster a more secure environment, encouraging investments in advanced security solutions and managed services, ultimately shaping a resilient operational technology landscape.
| Segment | Sub-Segments |
|---|---|
| By Offering | Network Security Asset Management Vulnerability Detection Patch Management Consulting Solutions Others (SIEM, Identity & Access Management, Managed Security Services etc.) |
| By Organization Size | Large Enterprises SMEs |
| By Deployment Mode | On-Premises Cloud-Based Hybrid Others |
| By Industry Vertical | Oil & Gas Energy & Power Manufacturing BFSI Transportation Healthcare Government Others (Chemicals, Water & Wastewater, Mining) |
| By Service Type | Consulting Services Implementation Services Managed Services Others |
| By Security Type | Physical Security Cybersecurity Operational Security Others |
| By Region | Central Region Eastern Region Western Region Southern Region |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Oil & Gas Sector Security Measures | 100 | IT Security Managers, Operations Directors |
| Manufacturing Industry Cybersecurity Practices | 80 | Plant Managers, Cybersecurity Analysts |
| Utilities Sector Operational Technology Security | 70 | Infrastructure Security Officers, Compliance Managers |
| Transportation Sector Cyber Risk Management | 60 | Logistics Coordinators, IT Risk Managers |
| Healthcare Industry Cybersecurity Strategies | 40 | Healthcare IT Directors, Security Compliance Officers |
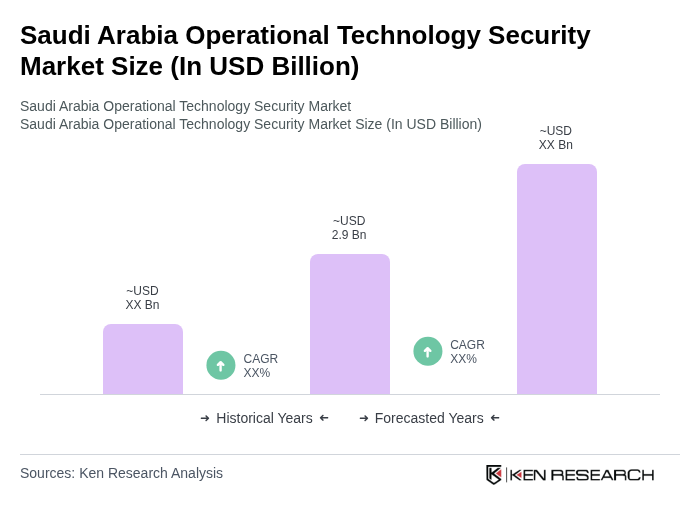
The Saudi Arabia Operational Technology Security Market is valued at approximately USD 2.9 billion, driven by the increasing adoption of IoT technologies and the need for enhanced security measures to protect critical infrastructure from cyber threats.