Region:Asia
Author(s):Dev
Product Code:KRAD5150
Pages:87
Published On:December 2025
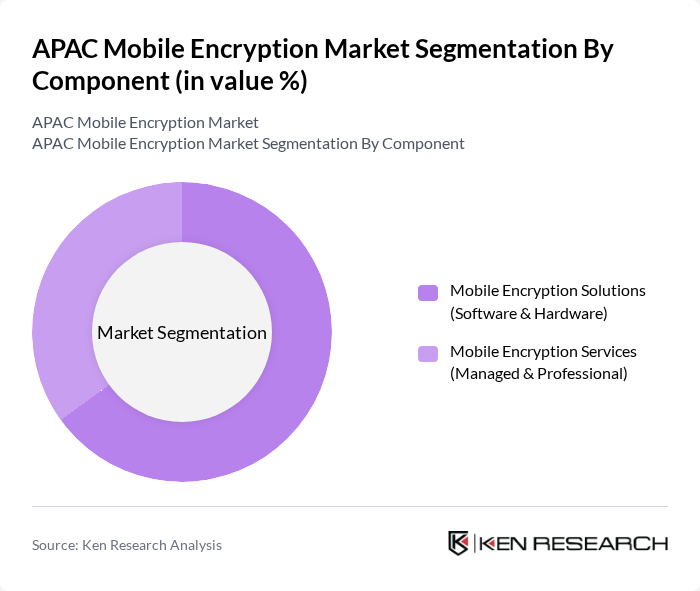
By Component:The market is segmented into Mobile Encryption Solutions (Software & Hardware) and Mobile Encryption Services (Managed & Professional). Mobile Encryption Solutions are increasingly favored due to their ability to provide comprehensive security features, while Mobile Encryption Services are gaining traction as organizations seek expert assistance in managing their encryption needs.
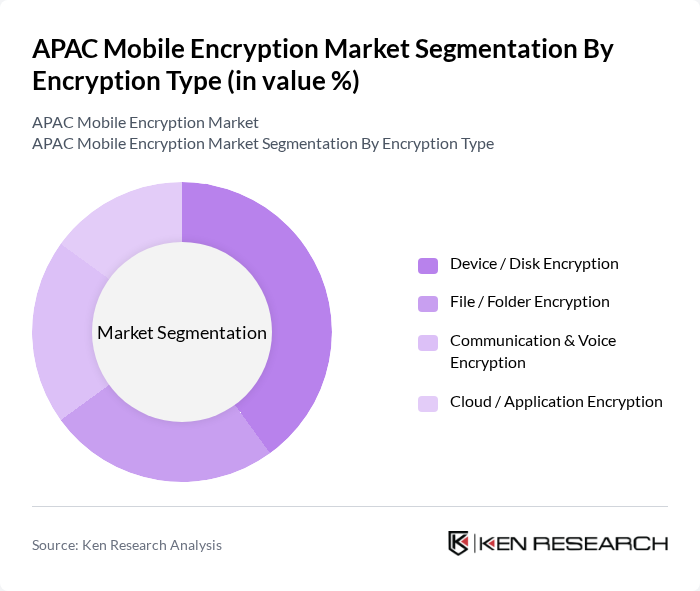
By Encryption Type:The market is categorized into Device / Disk Encryption, File / Folder Encryption, Communication & Voice Encryption, and Cloud / Application Encryption. Device / Disk Encryption is the leading segment, driven by the increasing use of mobile devices and the need to protect data stored on these devices. Communication & Voice Encryption is also gaining momentum as organizations prioritize secure communication channels.
The APAC Mobile Encryption Market is characterized by a dynamic mix of regional and international players. Leading participants such as BlackBerry Limited, Samsung Electronics Co., Ltd. (Samsung Knox), Apple Inc., Microsoft Corporation, Alphabet Inc. (Google / Android), Check Point Software Technologies Ltd., Thales Group, IBM Corporation, Cisco Systems, Inc., Fortinet, Inc., Sophos Group plc, ESET, spol. s r.o., Avast Software s.r.o., Ivanti, Inc. (MobileIron), Huawei Technologies Co., Ltd. contribute to innovation, geographic expansion, and service delivery in this space.
The APAC mobile encryption market is poised for significant evolution, driven by technological advancements and increasing security demands. As organizations prioritize data protection, the integration of artificial intelligence in encryption solutions is expected to enhance threat detection capabilities. Furthermore, the rise of remote work and mobile transactions will necessitate more robust encryption measures. In future, the focus will shift towards user-centric security solutions, ensuring that encryption technologies are not only effective but also user-friendly, fostering broader adoption across various sectors.
| Segment | Sub-Segments |
|---|---|
| By Component | Mobile Encryption Solutions (Software & Hardware) Mobile Encryption Services (Managed & Professional) |
| By Encryption Type | Device / Disk Encryption File / Folder Encryption Communication & Voice Encryption Cloud / Application Encryption |
| By Deployment Mode | On-Premises Cloud-Based |
| By End-User Industry | Banking, Financial Services and Insurance (BFSI) Government and Public Sector IT & Telecommunications Healthcare Retail & E-commerce Defense & Law Enforcement Others (Education, Manufacturing, Energy) |
| By Organization Size | Large Enterprises Small & Medium Enterprises (SMEs) |
| By Application Area | Mobile Banking & Digital Payments Secure Messaging & Collaboration Email & Data-at-Rest Protection Mobile Device Management & BYOD Security Others |
| By Country (APAC) | China India Japan South Korea Australia & New Zealand Southeast Asia (Indonesia, Malaysia, Thailand, Vietnam, Singapore, Philippines) Rest of Asia Pacific |
| Scope Item/Segment | Sample Size | Target Respondent Profiles |
|---|---|---|
| Financial Services Mobile Encryption | 120 | IT Security Managers, Compliance Officers |
| Healthcare Data Protection | 100 | Healthcare IT Directors, Data Privacy Officers |
| Retail Mobile Payment Security | 80 | Retail IT Managers, Payment Processing Heads |
| Telecommunications Encryption Solutions | 110 | Network Security Engineers, Product Managers |
| Government and Public Sector Encryption | 70 | Cybersecurity Analysts, Policy Makers |
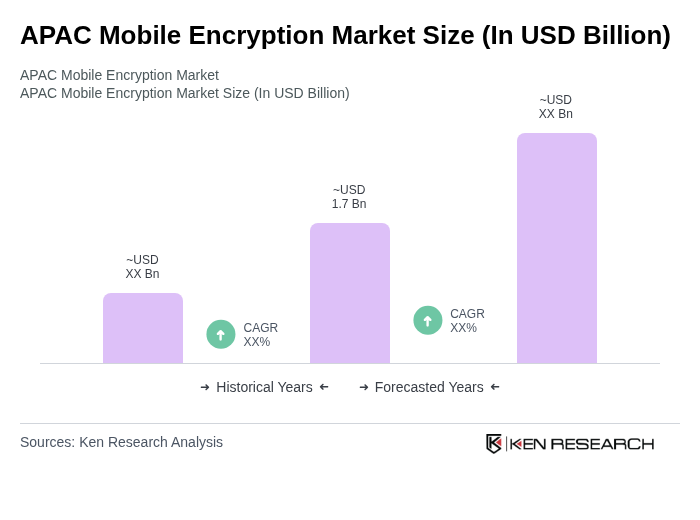
The APAC Mobile Encryption Market is valued at approximately USD 1.7 billion, representing a significant share of the global mobile encryption market, which is estimated to be around USD 4.04.5 billion.